What Are VPN Leaks?
A ‘VPN leak’ refers to a security flaw that allows your IP address, DNS requests, or other identifying information to be revealed to any third party monitoring your internet connection.
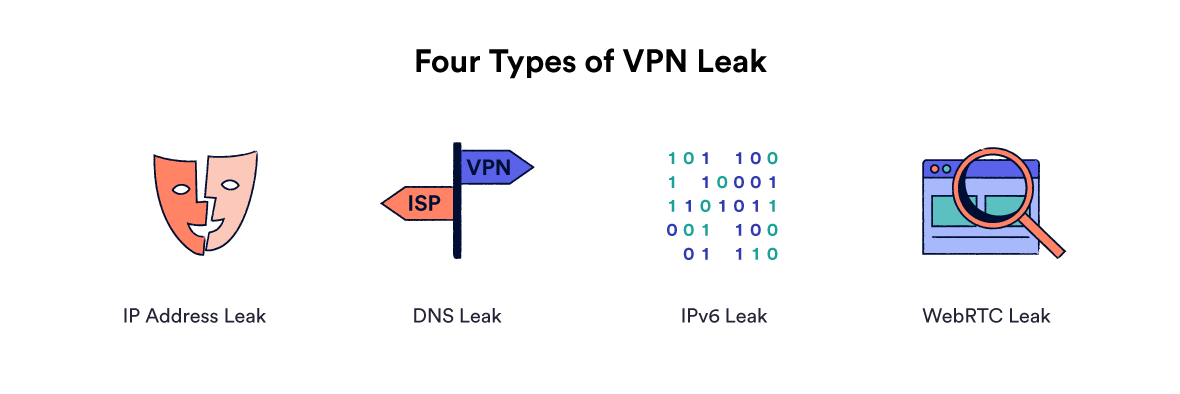
Four different types of VPN leaks.
VPN software is primarily designed to hide your public IP address and encrypt your web traffic by rerouting it through a secure tunnel to a remote server. When your VPN leaks, some or all of this sensitive information passes outside the encrypted tunnel.
If your real IP address or DNS requests are leaking, your ISP can still see your browsing activity and any websites you visit can see your real IP address. Your privacy is not protected, and your identity is exposed, making the VPN service useless.
To find out if your VPN is working as it should, you can run your own test at home using our VPN and torrent IP leak testing tool. It requires very little technical knowledge and takes just a matter of minutes.
You can also conduct a basic manual test for IP leaks using our What Is My IP checker tool. Simply check your IP address before and after connecting to a VPN server – if your IP address doesn’t change, your VPN isn’t working.
Here is a summary of the three main types of VPN leak:
IP Address Leaks
IP address leaks occur when your VPN service fails to mask your public IP address with one of its own. This is a significant privacy risk as any websites you visit will be able to see your real identity and geographic location.
If your IP address is leaking, your VPN is simply not doing its job. Your online privacy is not protected, and streaming services will be able to detect your true location.
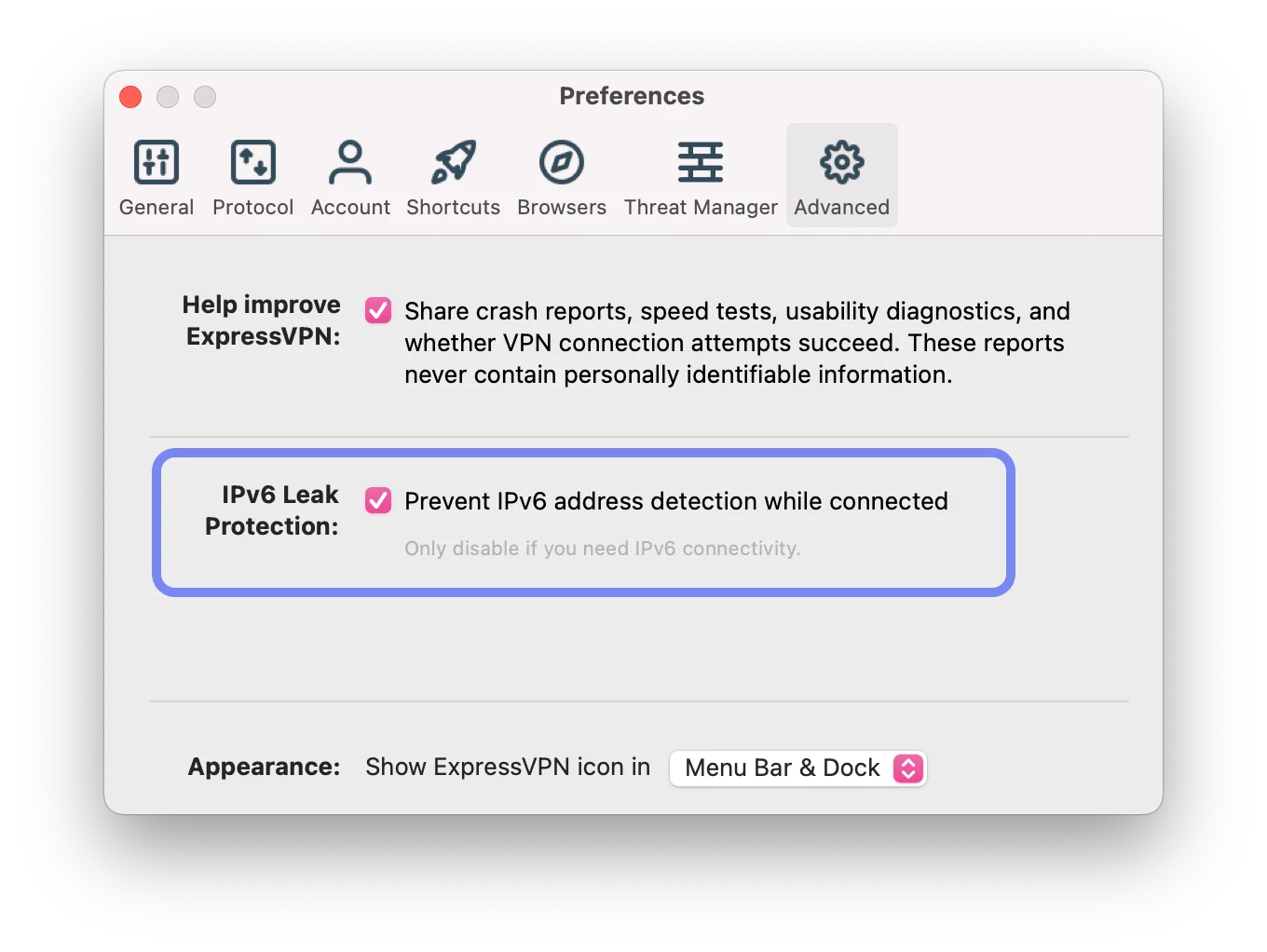
IPv4 leaks are rare, but IPv6 leaks are quite common – especially amongst low-quality VPN services. Only VPNs specifically developed to reroute or block IPv6 traffic will offset this problem.
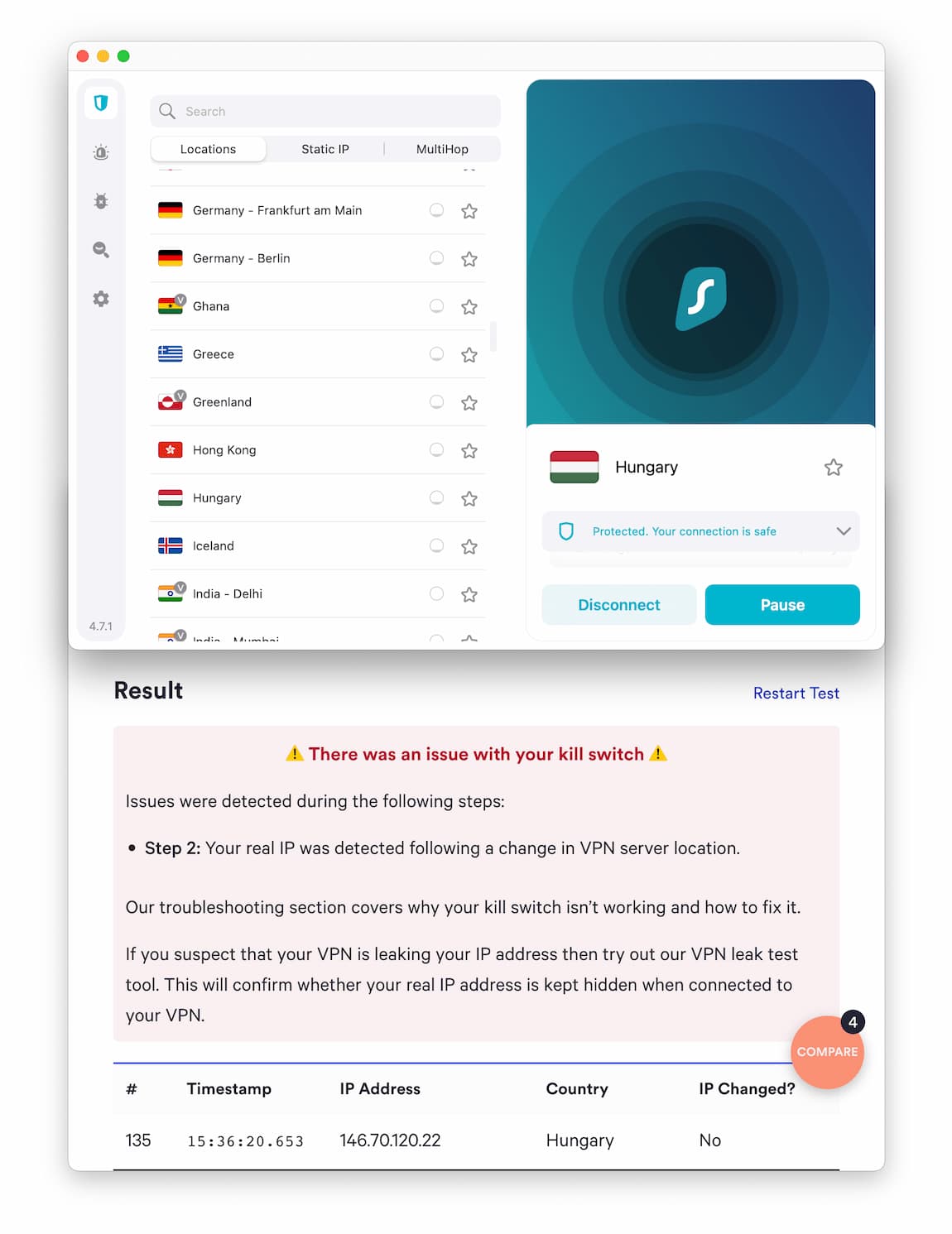
Surfshark’s kill switch does not stop IP address leaks when changing servers on macOS.
Premium VPNs should include a kill switch to protect your IP address in the event of a connection loss. However, our VPN kill switch testing revealed that many top services still leak your IP address if you change VPN servers while connected.
DNS leaks
DNS leaks occur when your DNS requests are revealed to your ISP’s DNS servers even when connected to a VPN server.
DNS requests are essentially records of the websites you visit when browsing the internet. Normally, this process is carried out by your ISP’s DNS servers, which often log the requests along with your IP address.
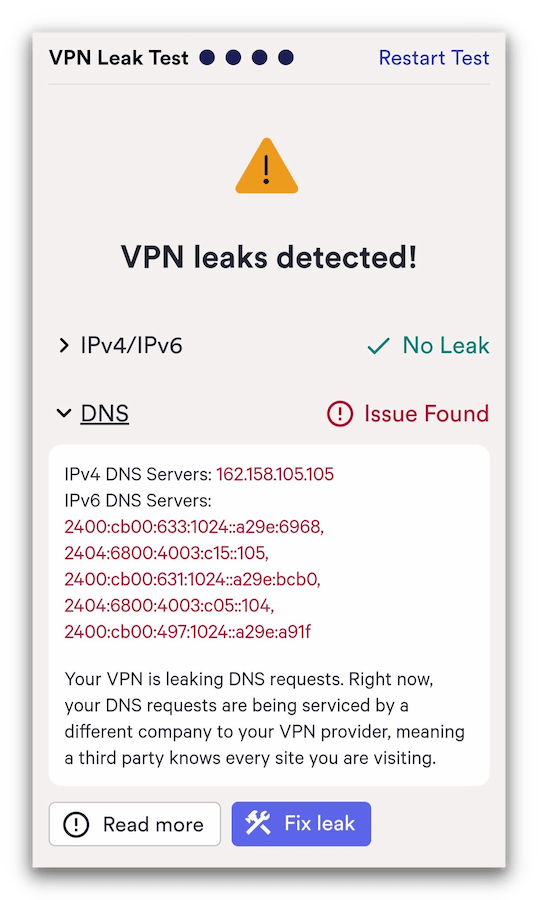
In our tests, SuperVPN leaked our DNS requests.
A VPN is supposed to encrypt your DNS queries and route them to its own private DNS servers. This prevents your ISP from monitoring the websites you visit. If your VPN fails to reroute your DNS requests and routes them to your ISP’s default DNS servers instead, it’s called a DNS leak.
To find out which servers your device is using, you can test your DNS servers using our tool.
WebRTC leaks
WebRTC is a browser-based technology that allows audio and video communications to work inside web pages. It’s enabled by default in popular browsers such as Chrome, Firefox, and Opera.
Websites can use your browser’s WebRTC functionality to discover your true IP address, even when you’re using a VPN. If this happens and your true IP address is not blocked by your VPN, it’s known as a WebRTC leak.