In this section we’ll teach you how to discover where a VPN server is really located.
Using a few online tools, you can find out whether your provider is being honest about its use of fake server locations.
These tests might seem daunting at first, but we’ll walk you through a simple step-by-step process that you can use to test your VPN server’s physical location. We’ll then present a few case studies so you can see the testing process in action.
1. Find the VPN Server’s IP Address
To start, you’ll need to identify the IP address of the VPN server you want to test.
The easiest way to do this is to connect to your VPN server of choice and head to our IP checker tool. It’ll show you your current public IP address.
EXPERT TIP: If your geographic location is showing up as similar to your true location, it’s possible your VPN is leaking. To check whether this is the case, use our VPN leak test tool.
2. Ping the VPN Server From a Range of Locations
A ping test measures the time it takes for a request to be sent to a server and for a response to be sent back. This helps test the rough distance between two points in a network: the higher the ping, the longer the distance between the two points.
To test where your server is physically located, you need to ping it from a number of locations around the world. By finding the lowest ping rate we can hone in on the server’s real physical location.
There are a number of online tools that allow you to run a ping test on a specific server from multiple locations worldwide. Our favorite is the CA App Synthetic Monitor ping tool, but you can also use MapLatency.com.
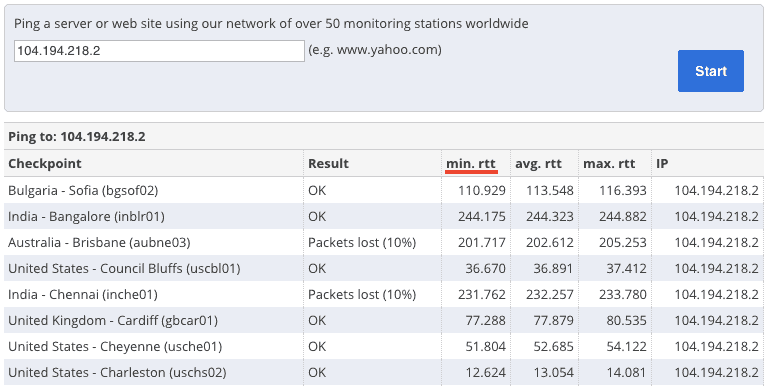
To begin, enter the VPN server’s IP address into the search box at the top and click the start button.
The tool will ping the server from each of their monitoring stations and record how long it takes. The CA App Synthetic Monitor tool has over 50 stations located around the world.
In this tool, rtt stands for ‘round trip time’ and refers to the amount of time (ms) it takes for a signal to be sent and an acknowledgement of that signal to be received.
You can analyze the results of this ping test to see which locations have the lowest round trip time and then infer the rough physical location of the server from there. Networking complications can sometimes lead to anomalous results, so the “minimum rtt” figure is usually the most reliable number to use.
If the rough location you can infer from the shortest round trip time differs significantly from the VPN server’s advertised country, it is likely that the server is using a fake location.
3. Run Traceroute Tests to Investigate the Findings
Using the traceroute tools offered by Looking Glass or CA App Synthetic Monitor, you can plot a data packet’s journey through the network from a monitoring station to your chosen VPN server.
The number of network hops, the location of the network hops, and the transmission time all help you investigate where your server is really located.
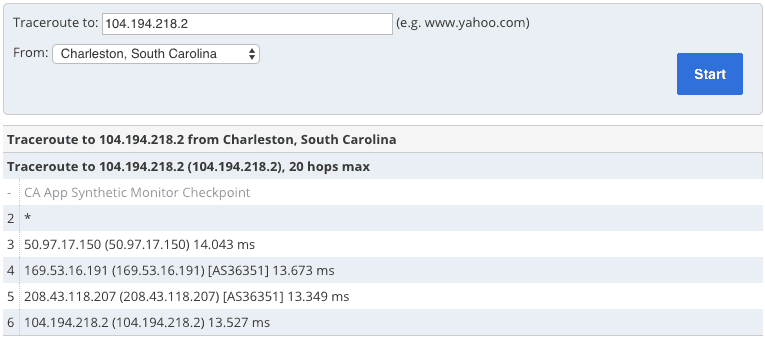
To start, run the traceroute that should be the closest to the VPN server. In other words, select a location that is as close as possible to the server’s advertised country.
Then, test the locations which had the smallest round trip times in the initial ping test.
Roughly speaking, if these locations show faster speeds and fewer network hops than the advertised location, it’s likely that your server’s location is fake.
4. Verify Your Results With a Separate Ping Tool
Network variability can sometimes lead to anomalous results, so it’s worth running each of the above tests multiple times in order to ensure your results are reliable. To finish, it is also worth running a second ping test, using a different online tool.
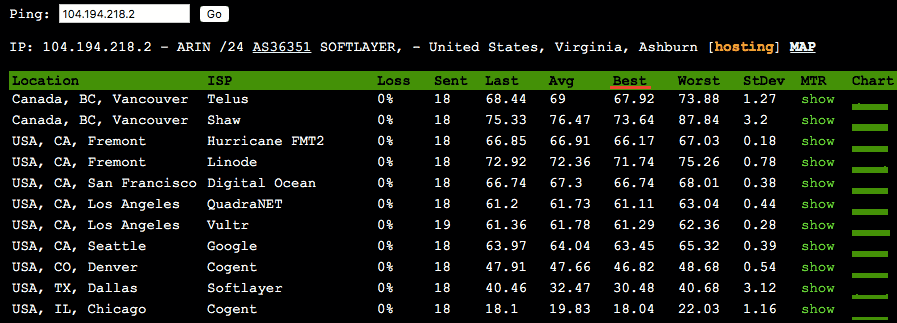
We like to use ping.pe as it has a good range of monitoring locations.
Input your server’s IP address in the box at the top and the tool with start pinging it from a range of locations. The ping times should hopefully match your previous findings, giving an indication of your server’s true location.
With these four easy steps you should be able to get a rough idea of where your VPN server is physically located. If the country you’ve found differs significantly from the location of the server’s advertised IP address, you’ve probably found a fake VPN server location.
It’s worth noting that this is not an exact science. Ping time is an indicator of geographic location, but a number of factors can distort it. The steps described in this guide will give you a rough idea of where a server is (or is not) located, but you should be wary of using these methods to draw definitive conclusions.
In the remainder of this report, we’ll run through a few case studies to demonstrate the investigation process in action.
Case Study #1: ExpressVPN
ExpressVPN offers users a server in Vietnam, but is transparent about the fact that it is a fake location. The server is actually located in Singapore.
We can verify that this is indeed a fake location using the steps described below.
1. Server’s IP address: 45.10.234.90
We can see the server’s IP address by connecting to ExpressVPN’s Vietnam server and checking browserleaks.com.
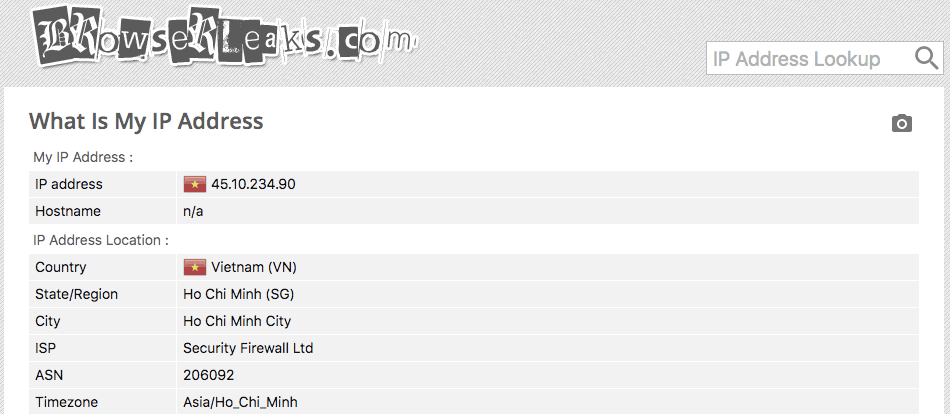
2. An initial ping test strongly suggests the server is physically located in Singapore and not Vietnam.
When we pinged the VPN server from a range of global locations, the shortest ping times came from Singapore, India, and China – with Singapore being the fastest by a significant margin.

Shortest Pings:
- Singapore — Singapore (0.945ms)
- India — Chennai (33.227ms)
- China — Hong Kong (37.918ms)
- India — Bangalore (38.497ms)
- India — Mumbai (60.718ms)
In contrast, a ping from Ho Chi Minh City – where the IP address is registered – took a minimum of 74.881ms.

The 0.945ms ping time from Singapore is significantly smaller than those from other locations. This alone is enough to infer a better idea of the server’s real location.
However, some small calculations show us that, even moving at the speed of light (300km/ms), data from the Singapore monitoring station can travel a maximum of 283km in 0.945ms. The data has to travel to and from the VPN server in this timeframe (0.945ms).
As the shortest distance between Singapore and Vietnam is 1,488km, this makes it impossible for the VPN server to be located in Vietnam.
We can therefore conclude with confidence that the ExpressVPN Vietnam server is not physically located in Vietnam. It is most likely based in Singapore, just as ExpressVPN states.
3. Our findings are supported by a traceroute and a separate ping test.
When we cross-checked our results with a traceroute test and with a separate ping tool, we found very similar stories.
Although the ping.pe tool doesn’t have a monitoring station in Vietnam, the extremely low ping times recorded at the Singapore monitoring station strongly suggest this VPN server is physically located in Singapore.
Case Study #2: CyberGhost
Like ExpressVPN, CyberGhost is transparent about which of its servers use fake locations. Unfortunately, it isn’t also transparent about where these servers are actually located.
CyberGhost state that their Isle of Man servers use virtual locations.
We used the methods described in this section to investigate where these VPN servers are really located.
1. Server’s IP address: 45.132.140.22
When you connect to a CyberGhost server location, the application helpfully tells you what your new IP address is. We confirmed this using several IP address checking tools.
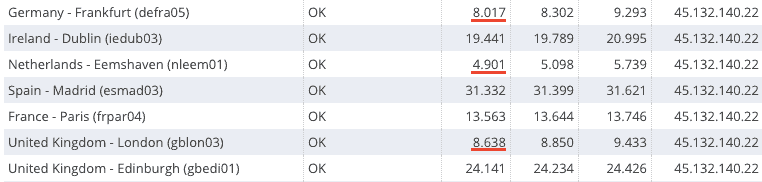
2. An initial ping test suggests the VPN server is located in Western Mainland Europe.
When we pinged the VPN server from global monitoring stations, the results indicated that it was located in mainland Europe, near the Netherlands or Belgium.
Shortest Pings:
- Netherlands — Eemshaven (4.901ms)
- Belgium — St. Ghislain (5.691ms)
- Germany — Frankfurt (8.017ms)
- UK — London (8.638ms)
- Denmark — Copenhagen (13.007ms)
3. Traceroute testing suggests the server might be located in Amsterdam, Netherlands.
We ran a traceroute on Looking Glass comparing Dublin (which is closest to the Isle of Man geographically) and Amsterdam.
The results showed an increased transmission time and several additional network hops when connecting to the server from Dublin as opposed to from Amsterdam. Also of interest was that network hop 3 in the Dublin traceroute connected it to the Amsterdam internet exchange.
This all suggests that the VPN server is not located in the Isle of Man, but is probably based somewhere closer to Amsterdam, Netherlands.
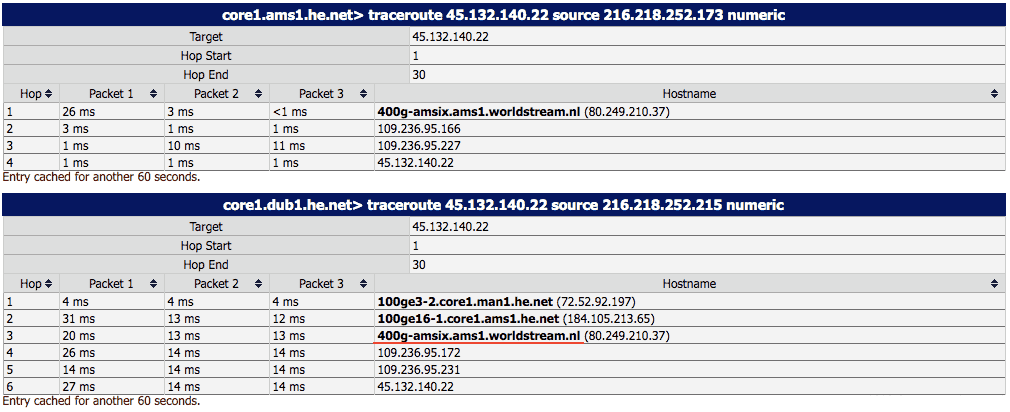
Traceroute tests from Amsterdam (top) and Dublin (bottom) to CyberGhost’s Isle of Man VPN server
4. A second ping test supports our findings that the VPN server is most likely located somewhere in the Netherlands.
We then cross-checked our findings with a ping test tool that uses a monitoring station in Amsterdam. The ping time averaged under 2ms.
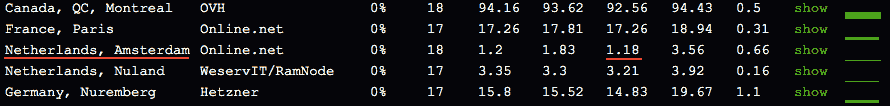
With a bit of math, we can work out that the furthest possible distance our VPN server can be from Amsterdam is 177km. We get this from the speed of light (300km/ms) multiplied by the shortest ping time (1.18ms) and divided by two (because it’s a round trip).
When we plot this on map, we can see that it is highly probable the CyberGhost Isle of Man server is in fact located in the Netherlands — most likely somewhere near Amsterdam.
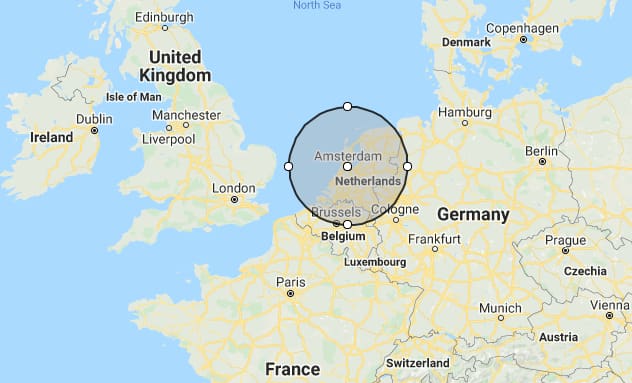
CyberGhost’s Isle of Man server has to be within a 177km radius around Amsterdam, Netherlands (Map made using mapdevelopers.com).