How to Access the Dark Web on a Computer (PC & macOS)
The safest way to access the dark web is to use a desktop computer and the Tor Browser. Tor (The Onion Router) is a free, open-source system designed to enable anonymous communication across the internet.
It does this by routing your traffic through three random servers, encrypting your traffic and hiding your IP address in the process.
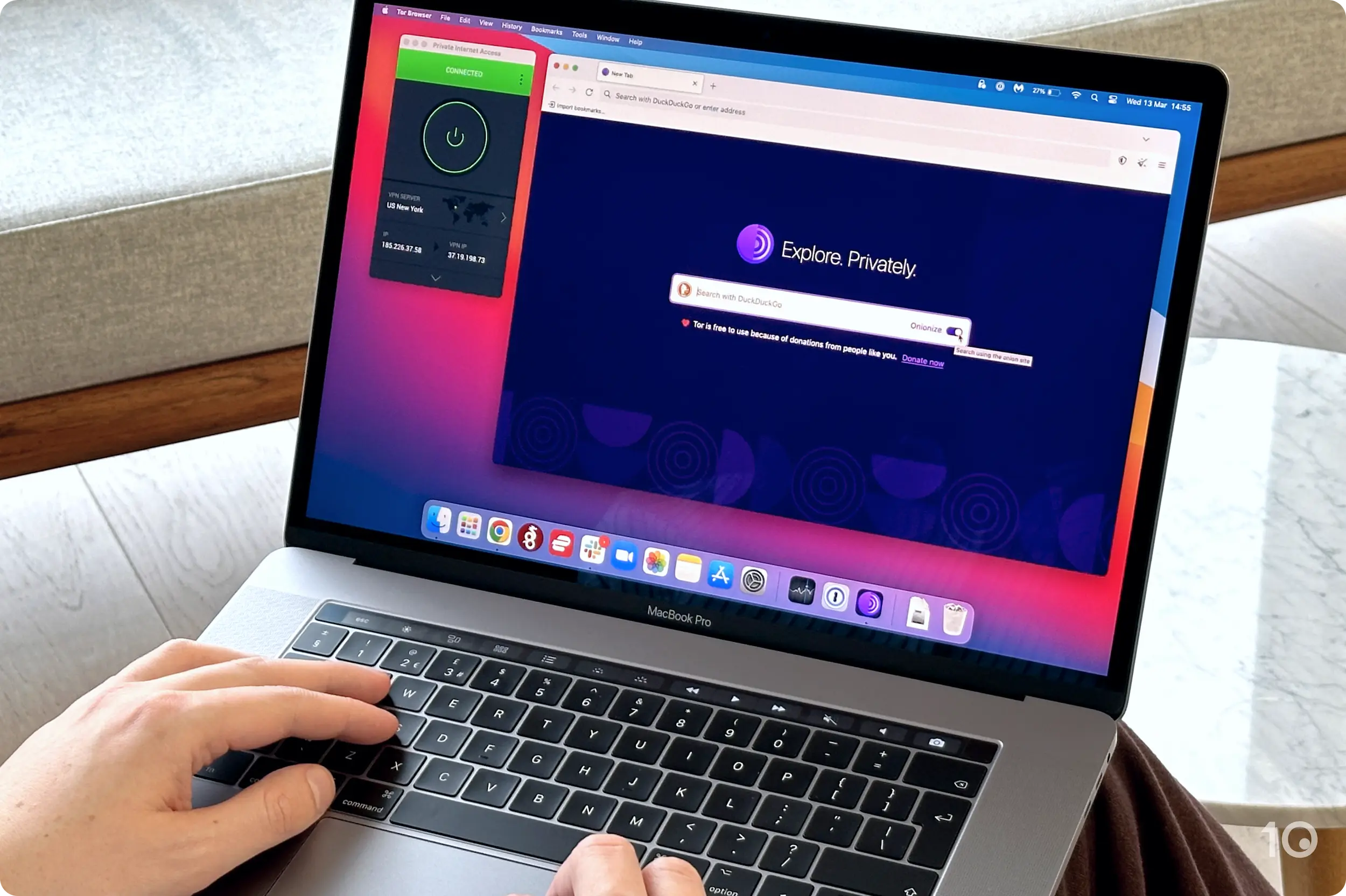
Unlike other web browsers such as Google Chrome or Safari, the Tor Browser is designed to access hidden .onion sites which are blocked on the surface web. As a result, it has built-in security and privacy features to protect your identity.
There are two main methods for accessing the dark web on a computer:
The best method for you will depend on your own personal threat level and how deeply you want to go into the dark web.
If you’re just curious about what the dark web looks like, you can choose the easiest setup: antivirus software, VPN software, and the Tor Browser (method 1).
If you plan to spend longer on the dark web, we recommend using Tails OS with the Tor Browser (method 2). It’s more complicated to set up, but it offers a higher level of protection.
Method 1: Use a VPN & the Tor Browser
Safety Level: Moderate
Setup Difficulty: Easy
What You’ll Need: Computer, VPN Subscription
To safely access the dark web on Windows and macOS, you can combine the Tor Browser with a VPN to hide your identity.
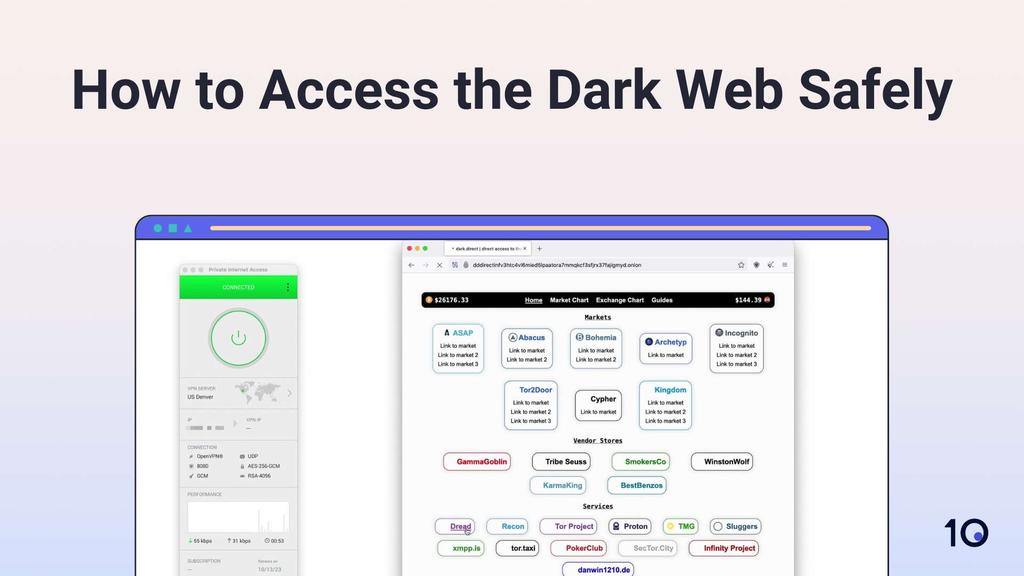
The only equipment you’ll need for this method is your computer and a no-logs VPN subscription. It’s a relatively easy process that still maintains a high security level. In fact, our research team uses this method to gather information on darknet marketplaces.
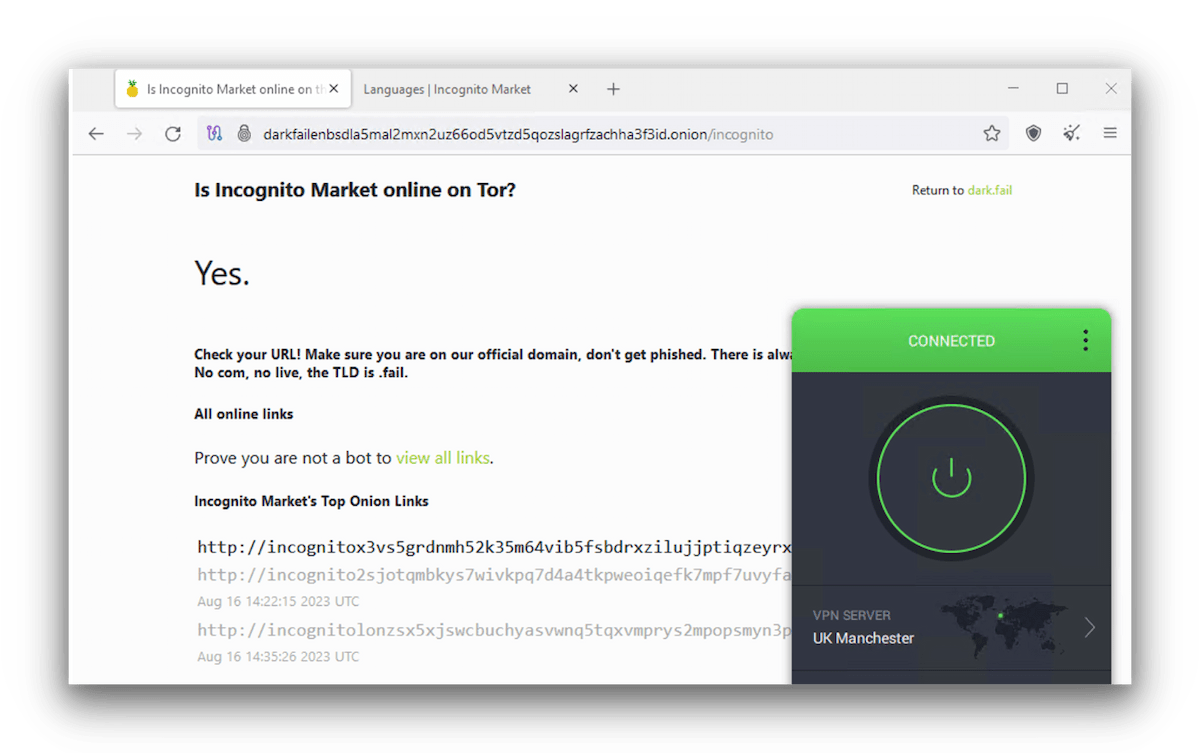
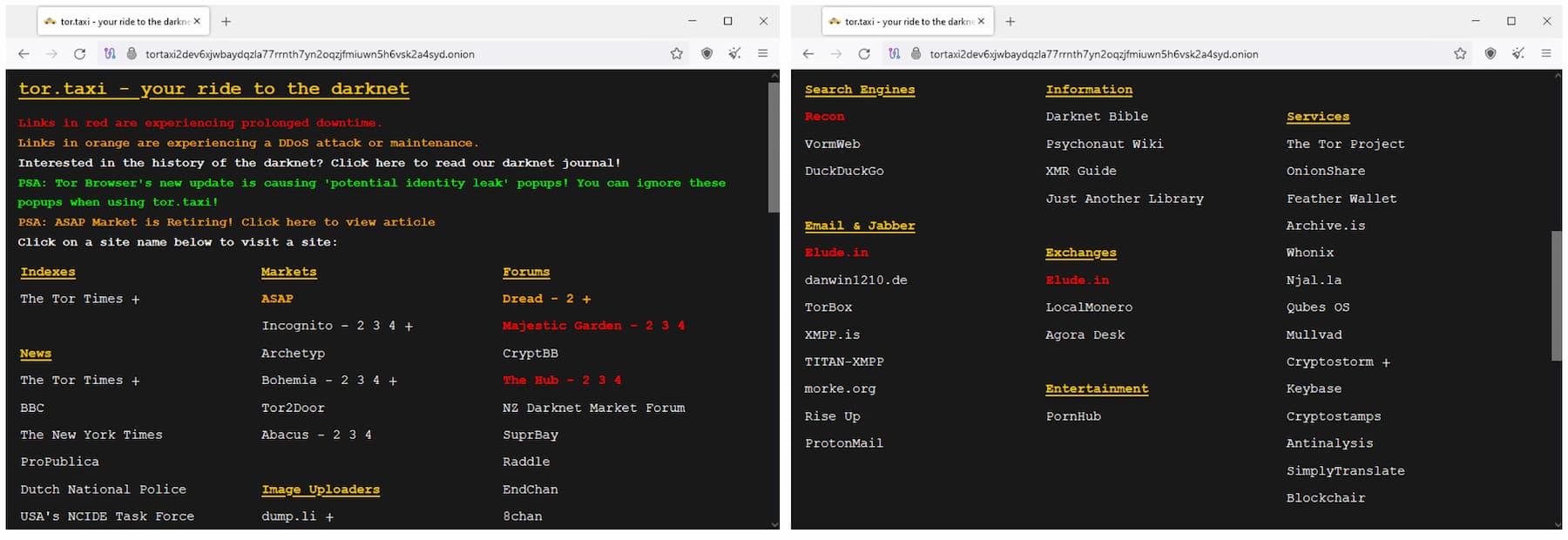
We used a VPN and the Tor Browser to access Incognito, a dark web marketplace, on Windows.
EXPERT ADVICE: When using this method, we recommend taking some basic precautions to protect your device and personal files.
Crucially, you should complete these steps before you access the Tor network. Once completed, you’ll be ready to continue the process.
Before you continue, follow these steps:
- Install trustworthy antivirus software. Scan your device for existing malware and make sure it is clean. Keep the software on to avoid downloading malware while browsing the dark web.
- Backup any important documents, images, or videos to an external hard drive. This gives you a failsafe in case something happens to your device.
- Cover up your webcam, disable your device’s microphone, and turn off location services on your computer.
- Close all unnecessary programs you have running in the background.
Here’s how to access the dark web safely using VPN and the Tor Browser:
- Sign up for a secure, no-logs VPN like Private Internet Access (PIA).
- Install the VPN app onto your computer and log in to your account.
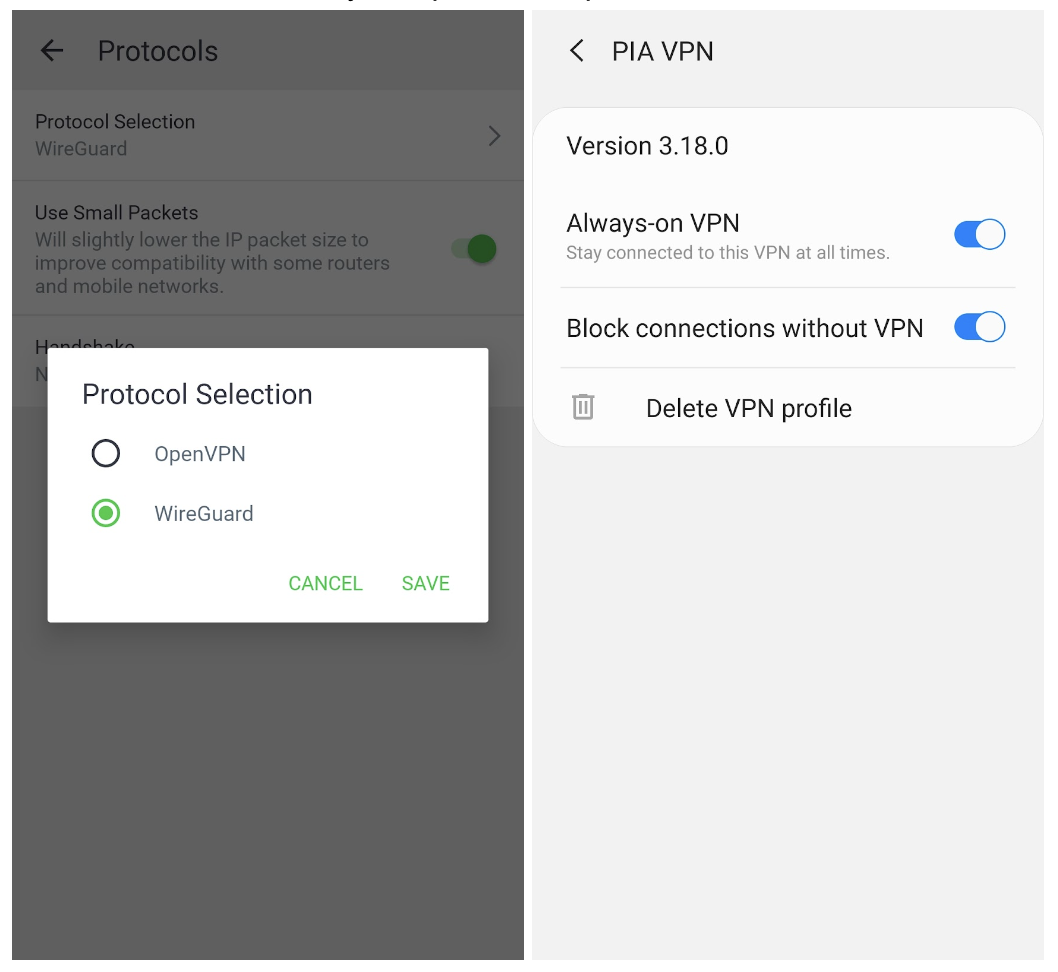
- Change VPN protocols to OpenVPN or WireGuard, enable the VPN kill switch, and ensure any leak protection features are switched on.
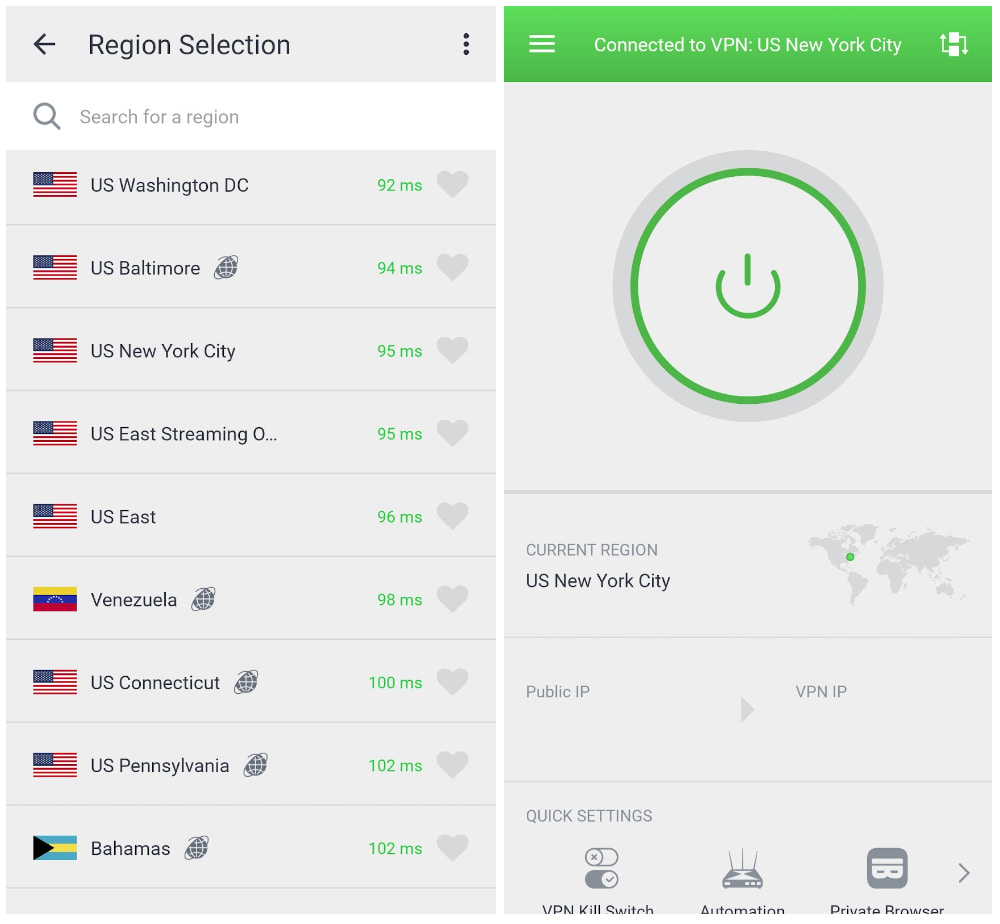
- Connect to a nearby VPN server for the fastest speeds.
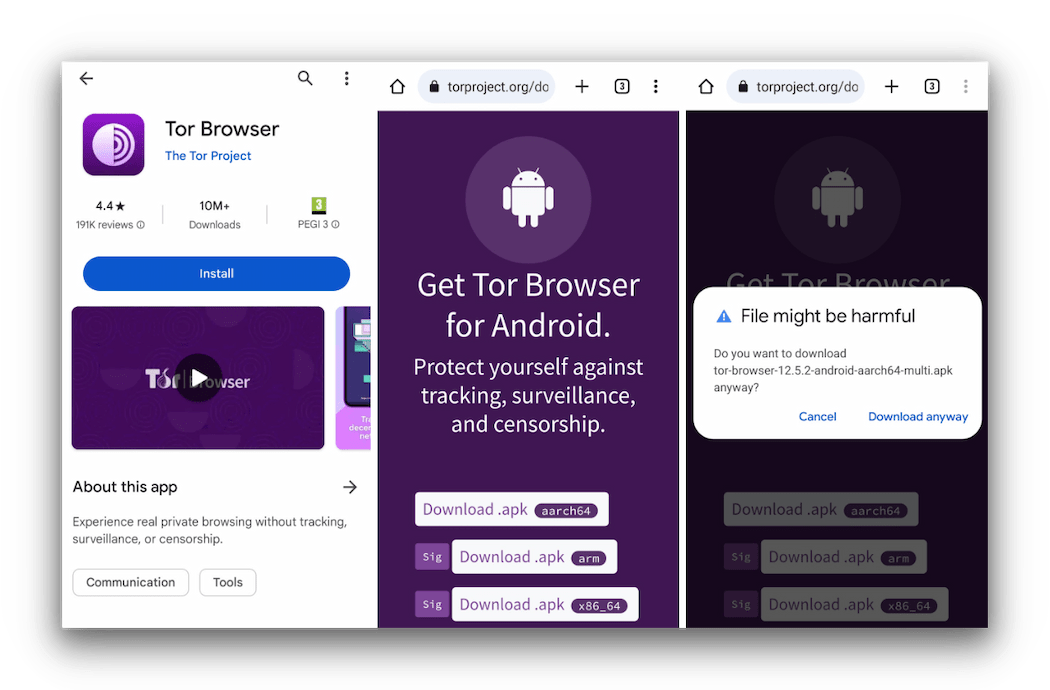
- With the VPN connected, open your preferred web browser and head to the Tor Project’s download page.
- Click on Download for Windows or Download for Mac, depending on your device.
- Once installed, launch the Tor Browser and click Configure Connection.
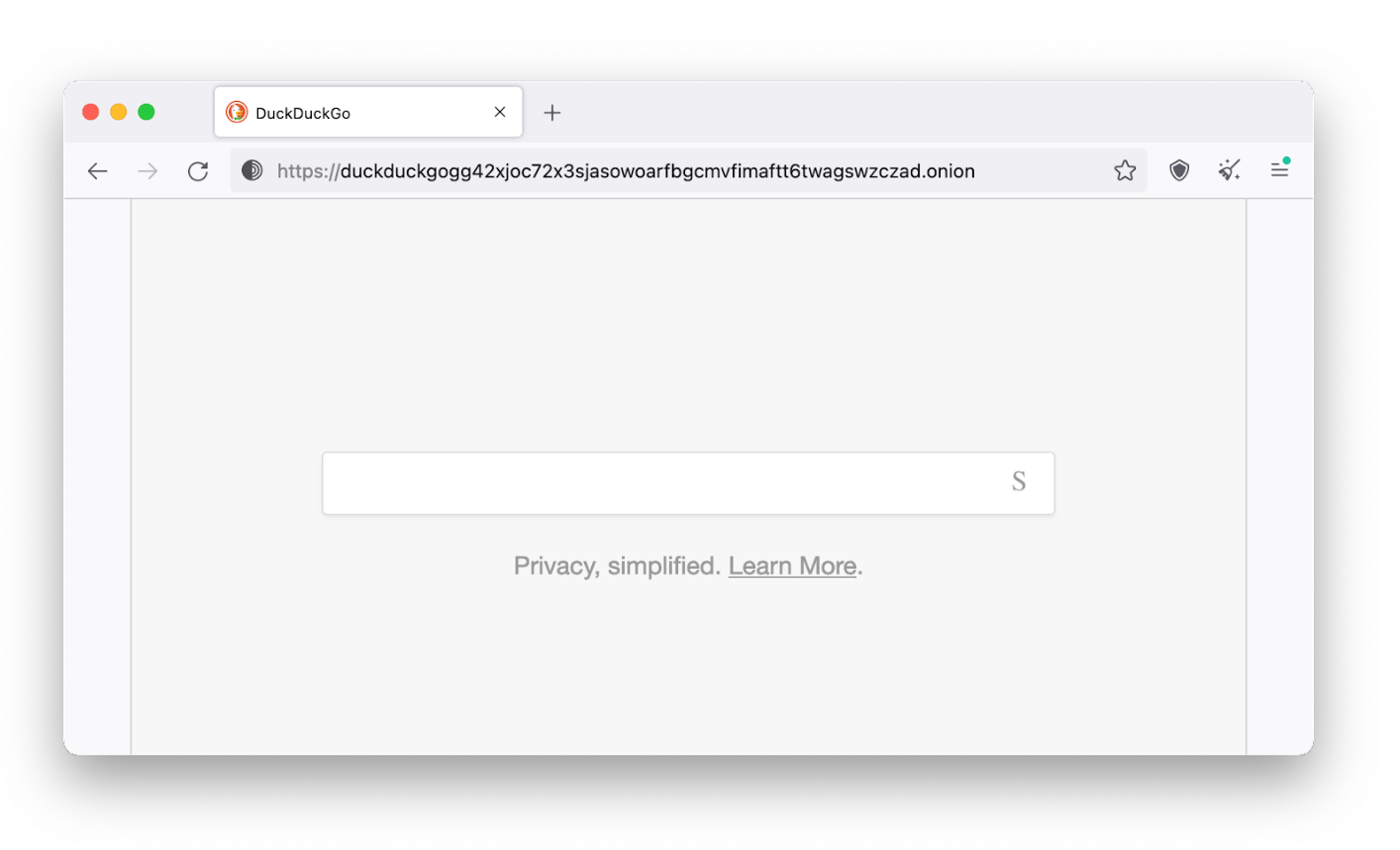
- In Settings > Search, change your default search engine to DuckDuckGoOnion.
- In the Privacy & Security menu, choose the following settings:
- Tick “Always” under “Prioritize .Onion sites”.
- Tick “Delete cookies and site data when Tor Browser is closed”.
- In Permissions, tick “Block pop-up windows and “Warn you when websites try to install add-ons”.
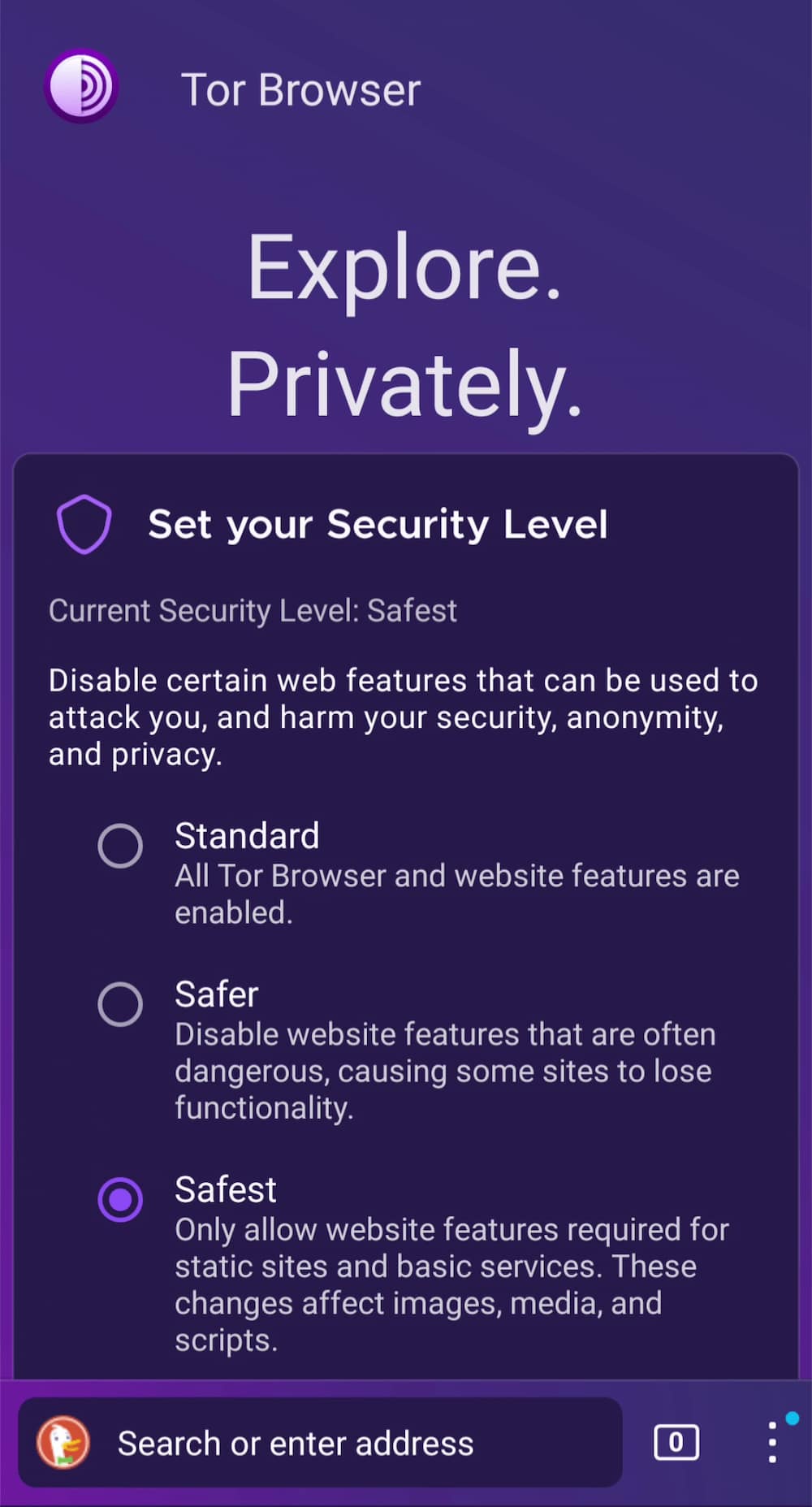
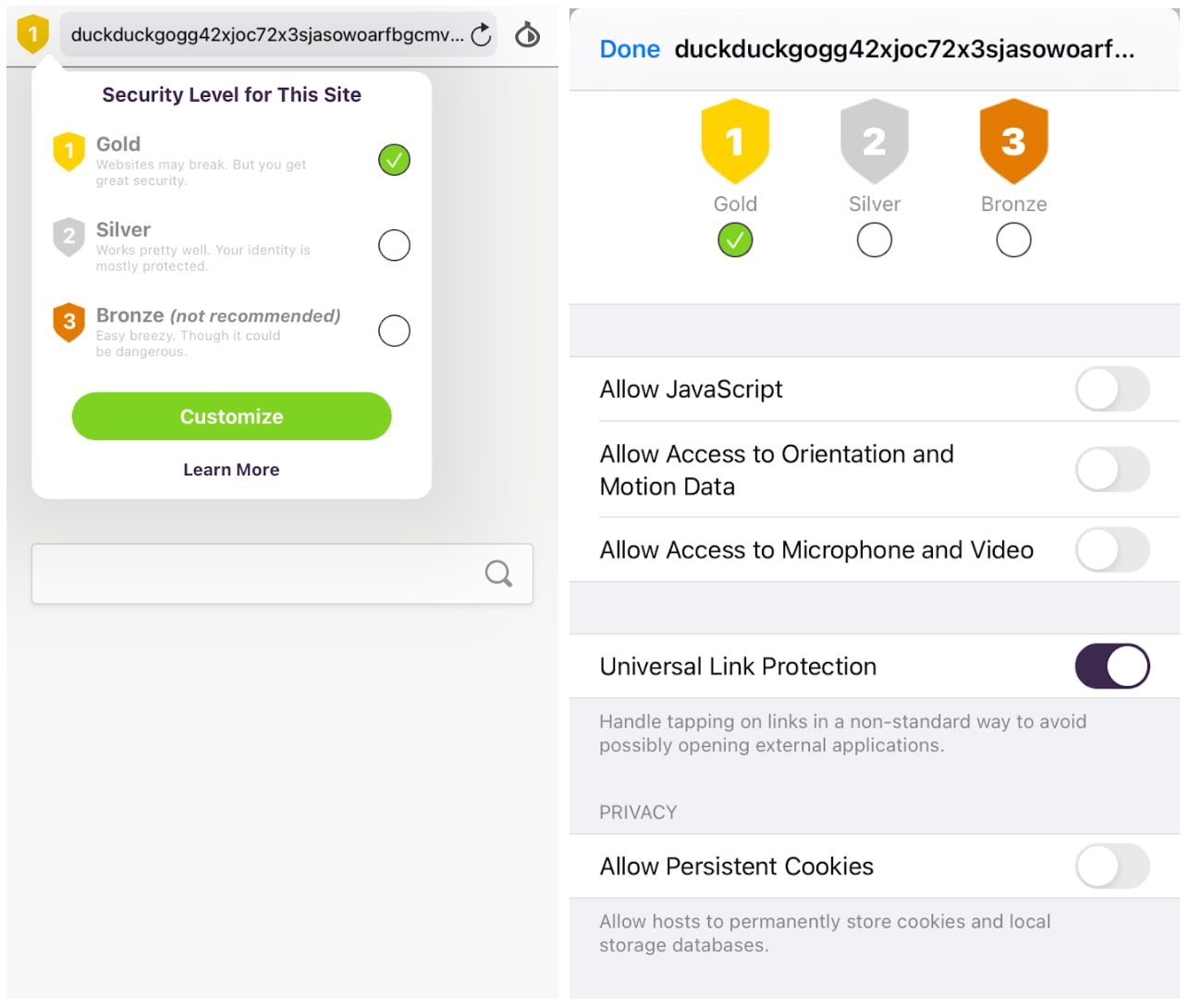
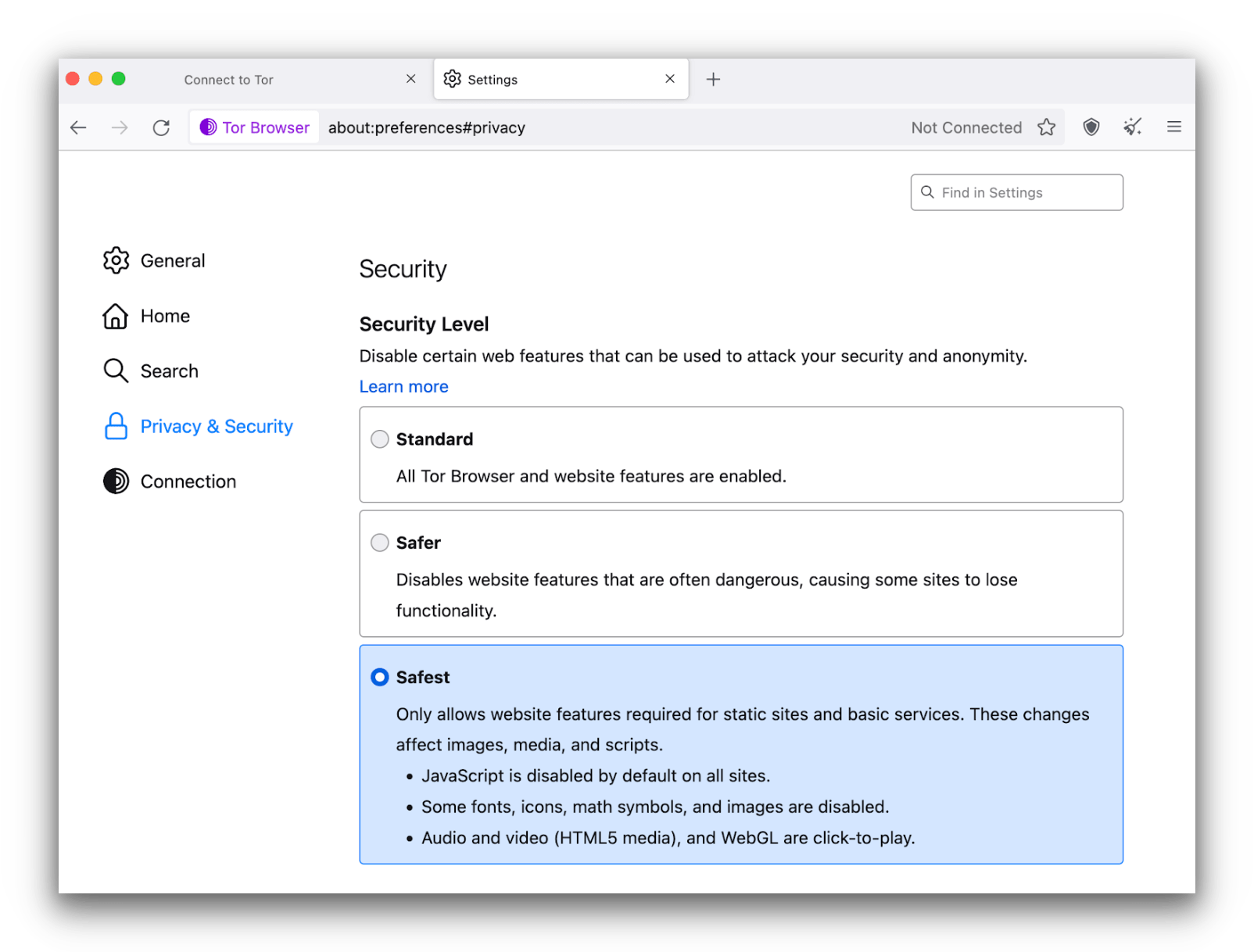
- In Security, select the “Safest” mode. This will disable Javascript, block certain images, and make all video files click-to-play.
- Tick “Enable HTTPS-Only Mode in all windows”.
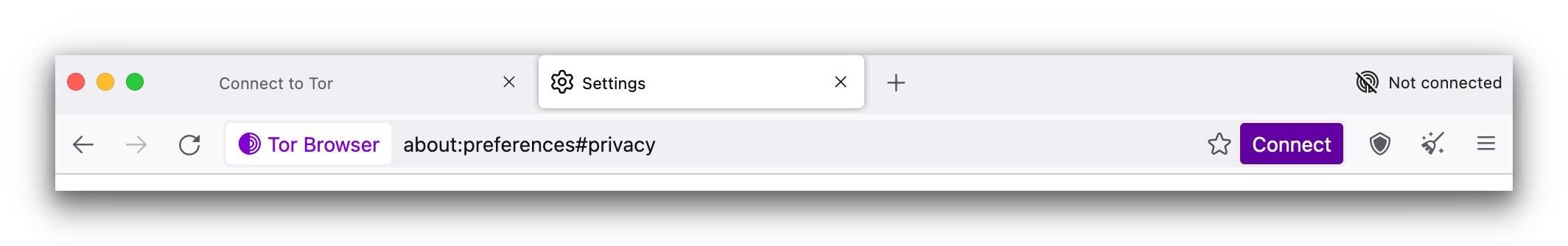
- In the top right-hand corner of the browser, click on the purple Connect button. You’re now connected to the Tor network and can browse the Dark Web safely.
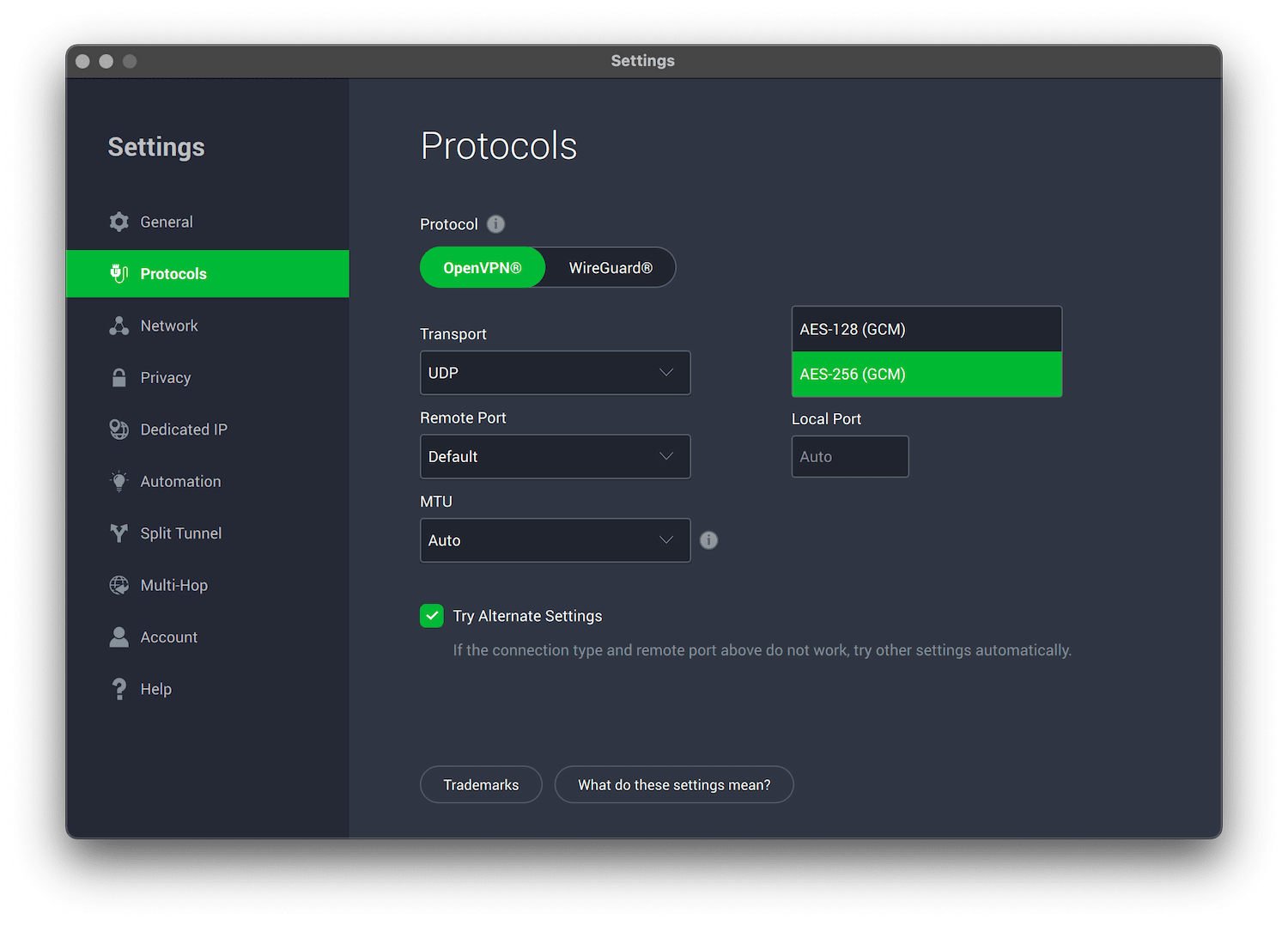
PIA also lets you choose the level of AES encryption on your connection.
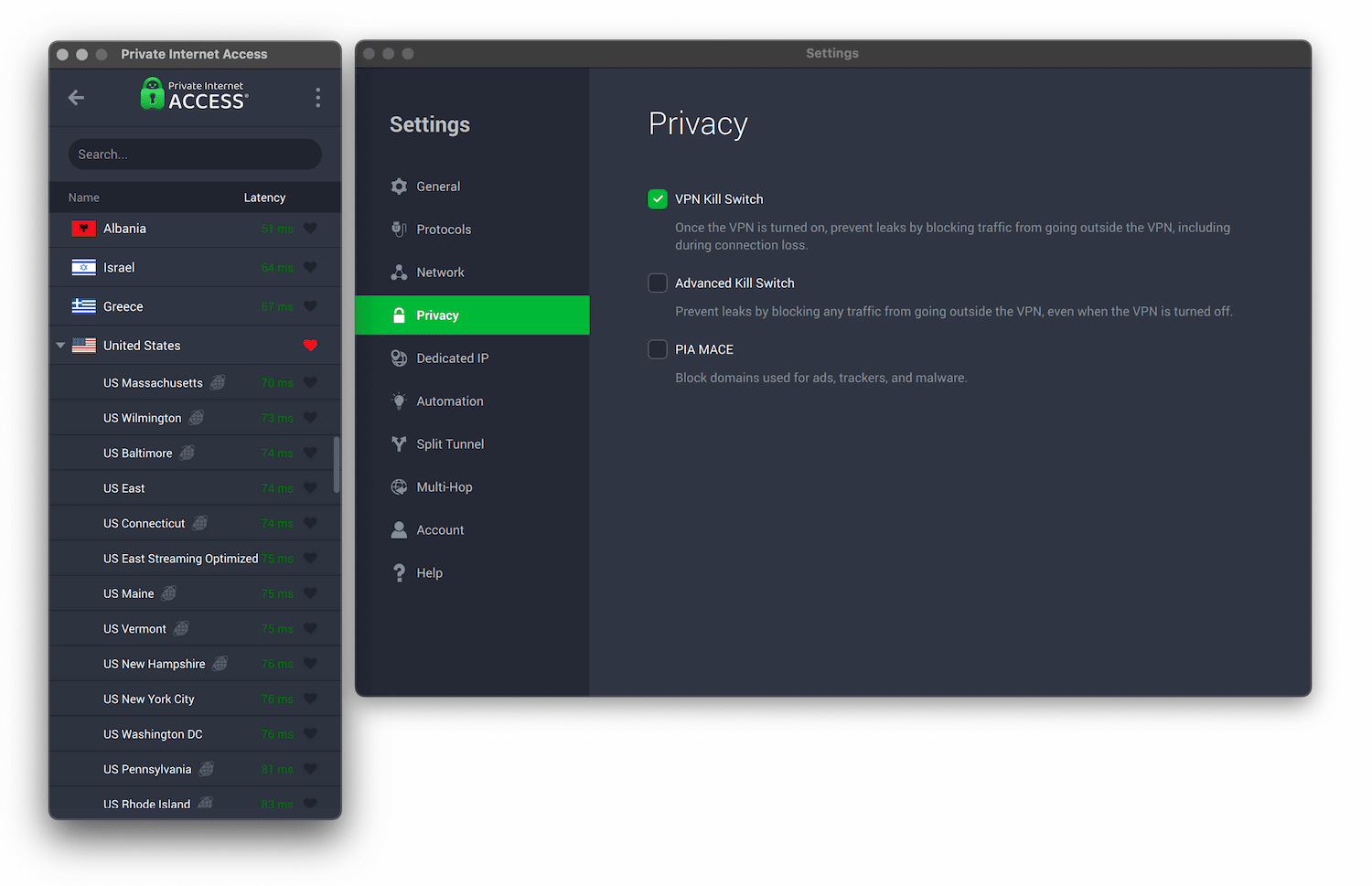
Tor can be slow, so choose a nearby VPN server for the fastest speeds.
The Tor Browser is available on Windows, macOS, Linux, and Android.
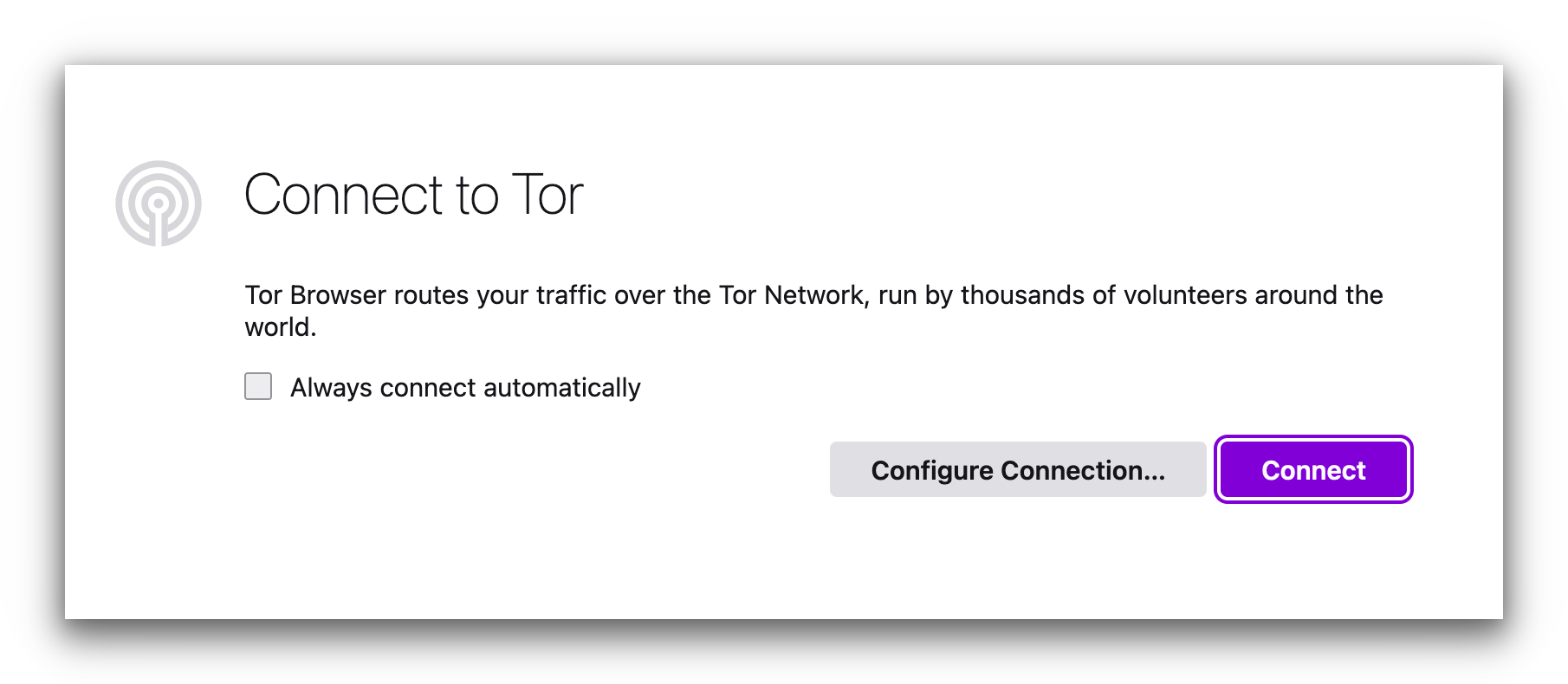
We suggest tweaking the security settings in the Tor browser before connecting.
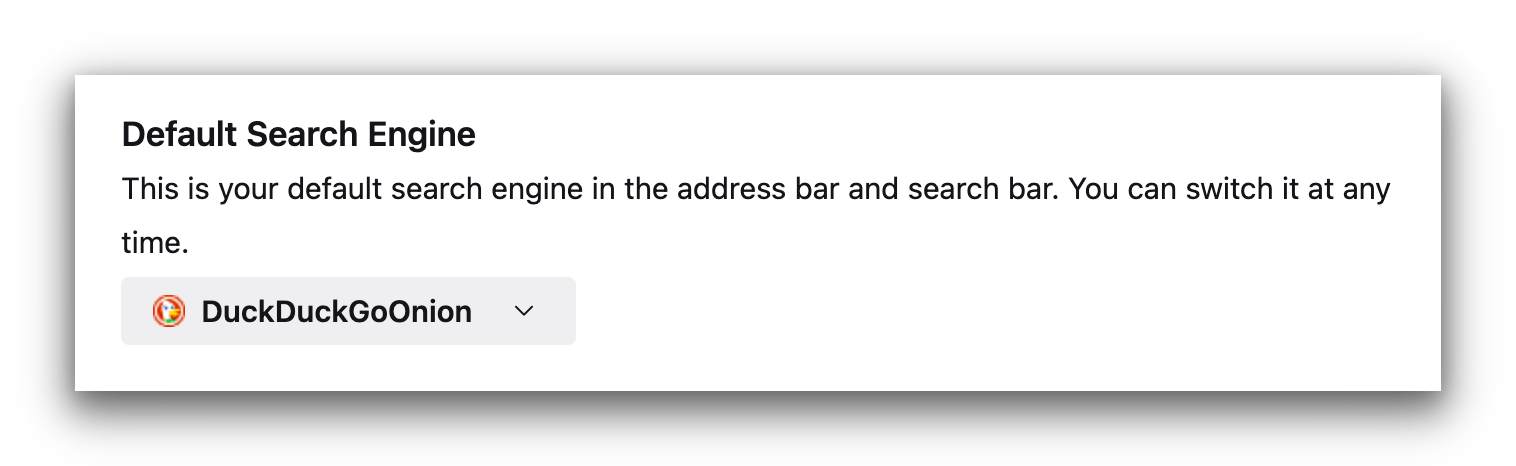
We discovered DuckDuckGoOnion has the most reliable and useful search results on the dark web.
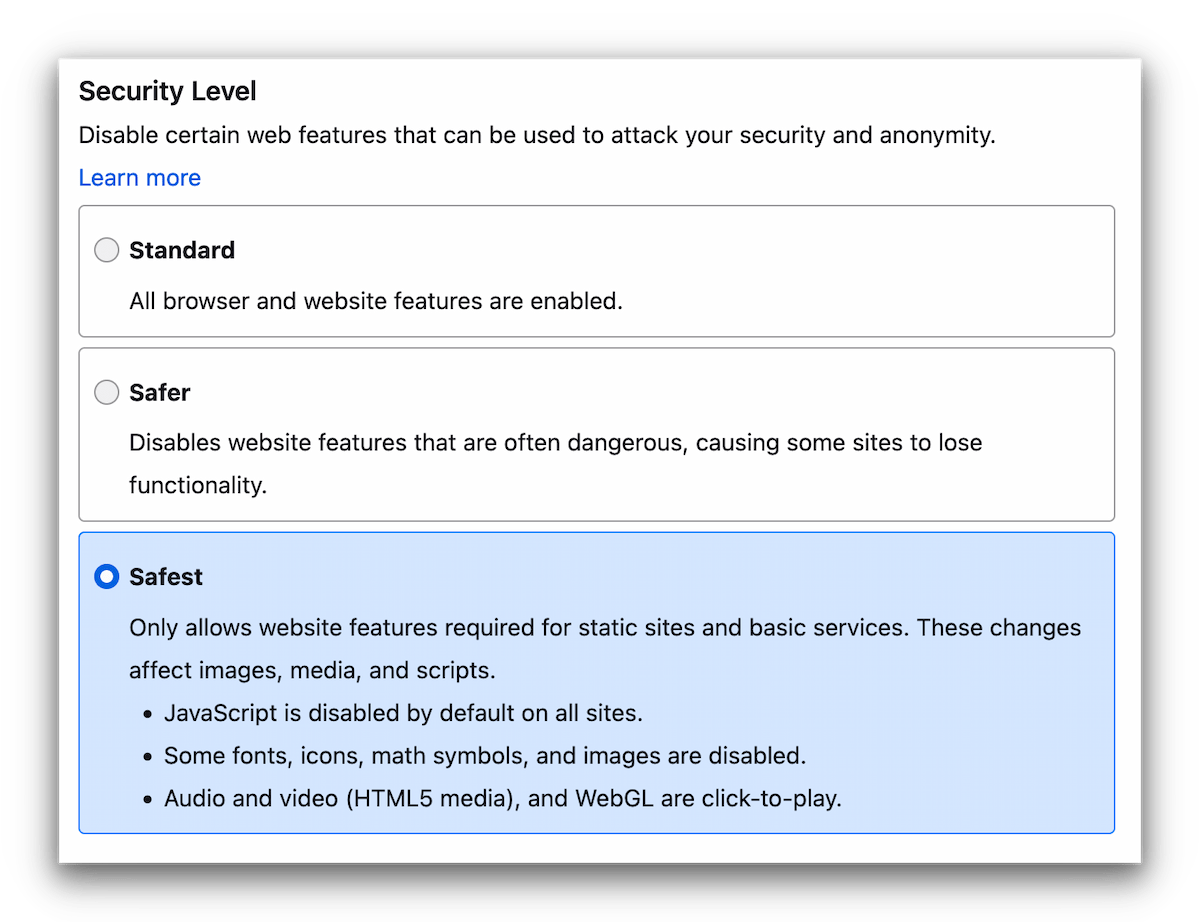
Select the safest security setting.
Method 2: Use Tails & the Tor Browser
Safety Level: High
Setup Difficulty: Moderate
What You’ll Need: Computer, 8GB USB Flash Drive, Mobile Device
You can also access the dark web on a computer using Tails OS and the Tor Browser. This is the safest method as it completely isolates your dark web activity from your main hard drive.
Despite its safety benefits, this method is also the most complicated. We only recommend using this method if your activities require the highest level of security.
Tails is a unique OS that works totally differently to ones you might be used to. By design, it removes the risk of third-parties accessing files on your hard drive (like your pictures, videos, and sensitive documents).
In addition, if anyone were to physically seize your computer, you can quickly unplug the USB to eradicate all evidence of your activity.
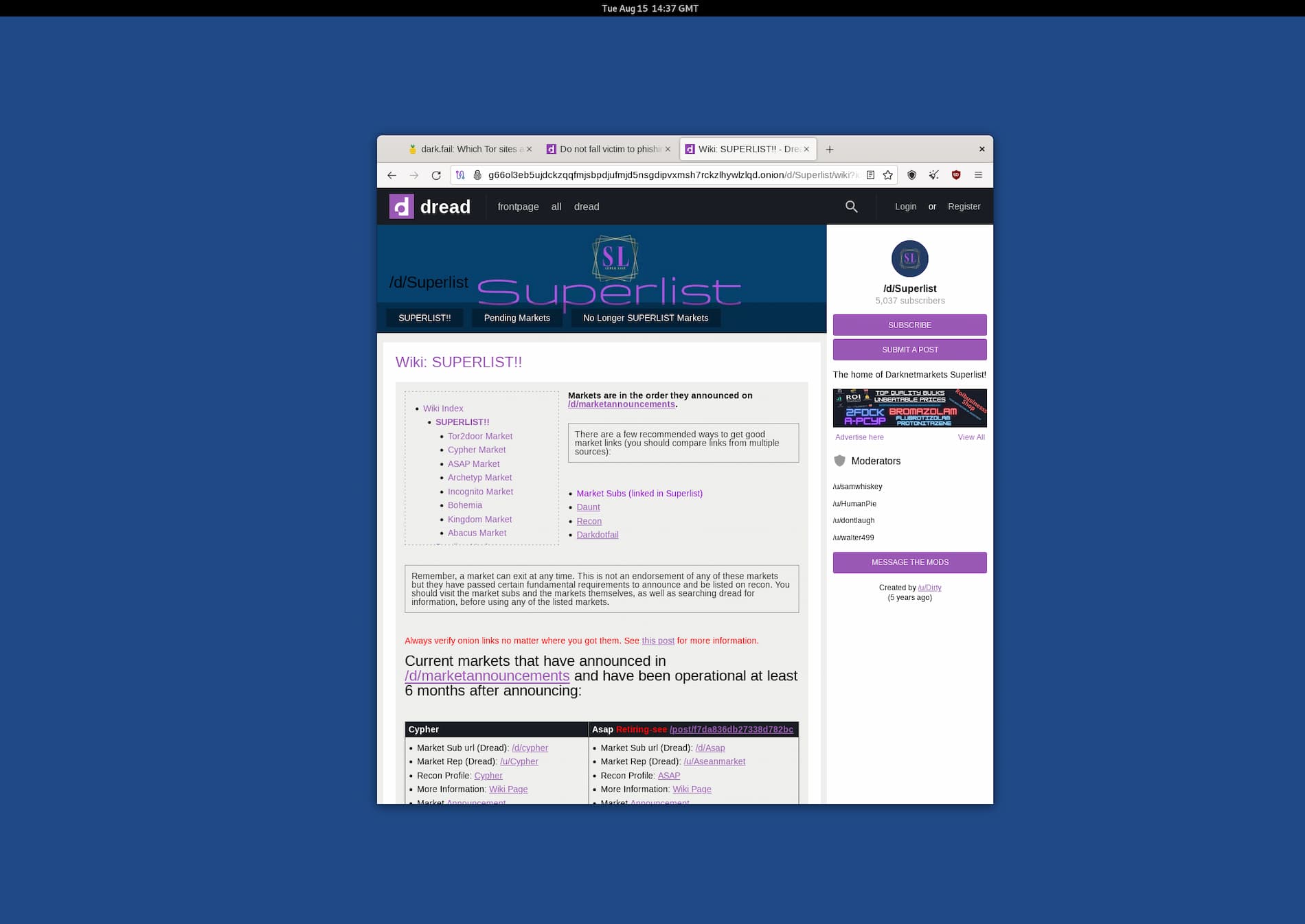
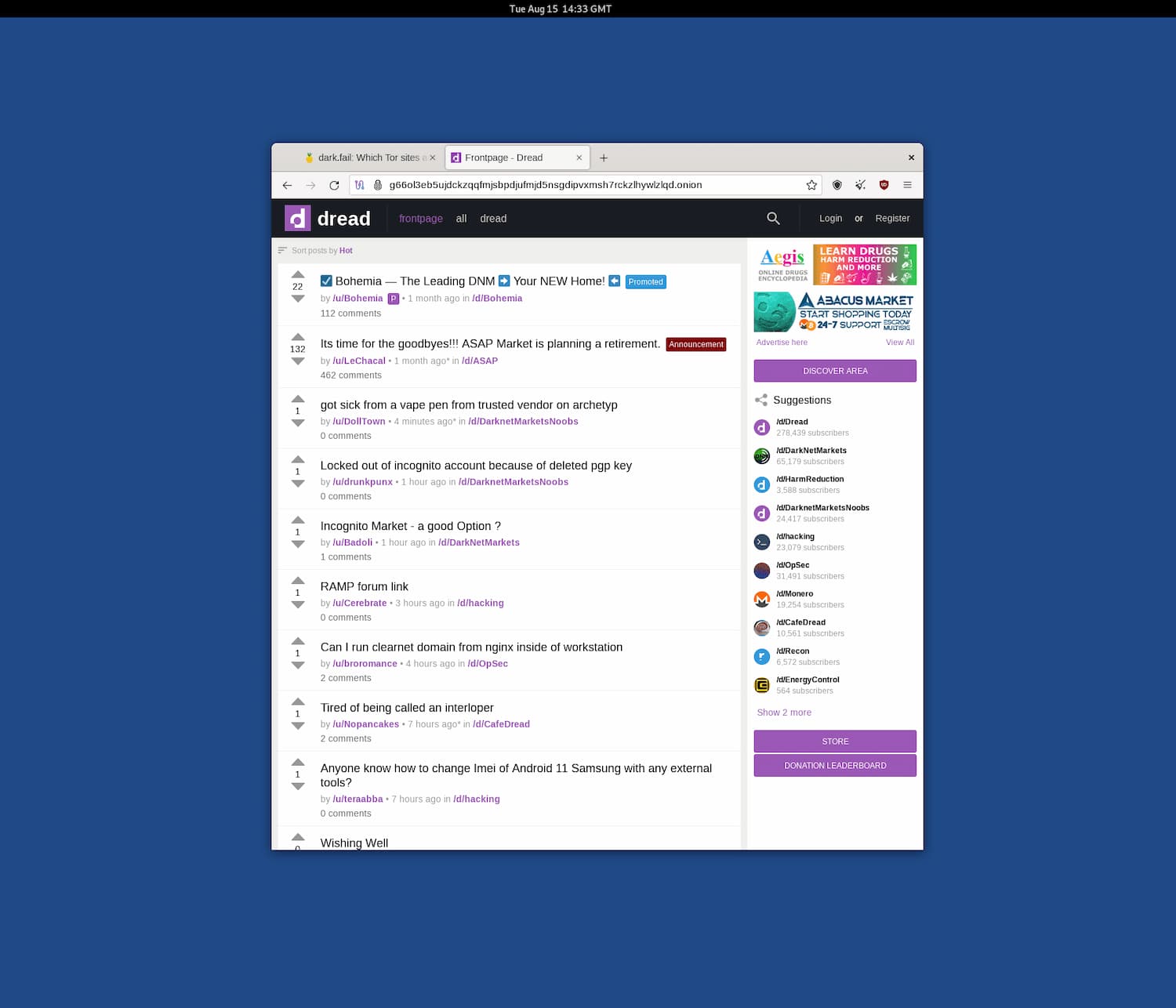
We used Tails and the Tor Browser on an iMac to access Dread, a dark web forum similar to Reddit.
Tails is an alternative operating system to Windows and macOS. Here are some of its unique features:
- It’s portable. You install Tails onto a flash drive and then plug that into your computer’s USB port. This means all of your Tor activity is automatically compartmentalized and separate from your day-to-day system.
- Tails is an amnesic OS, which means it deletes all files, cache, and saved data every time the USB drive it’s running from is disconnected.
- Tails automatically routes all internet traffic via the Tor network.
Here’s how to access the dark web safely using Tails and the Tor Browser:
Download & Install Tails
- Plug the USB flash drive into your computer.
- Rename the USB “Tails OS” and make sure to only use it for Tails.
- Head to the Tails official website and select your chosen device. The Tails website also has detailed instructions on how to properly install Tails onto a USB drive.
- Download the latest version of Tails onto your computer. It’s a large file, so it might take a little while to complete.
- Verify your Tails download to make sure it’s safe and hasn’t been corrupted. There are some copycat files on the internet posing as Tails.
- Once your Tails download is verified, download balenaEtcher from the Tails website.
- Navigate to the balenaEtcher application and start it.
- Click on the “Flash from File” button and select Tails. Make sure the Tails file ends with .img and not .iso.
- Click the “Select target” button to select your chosen USB drive.
- Click “Flash!” and enter your device’s password if you are asked for it.
- Wait for the installation to finish. It should take just a few minutes, then balenaEtcher should verify the installation.
- Close balenaEtcher and eject the USB flash drive you installed it to, but do not physically remove it.
- You’ve successfully installed Tails onto a USB drive. Now open the Tails installation instructions on your mobile device.
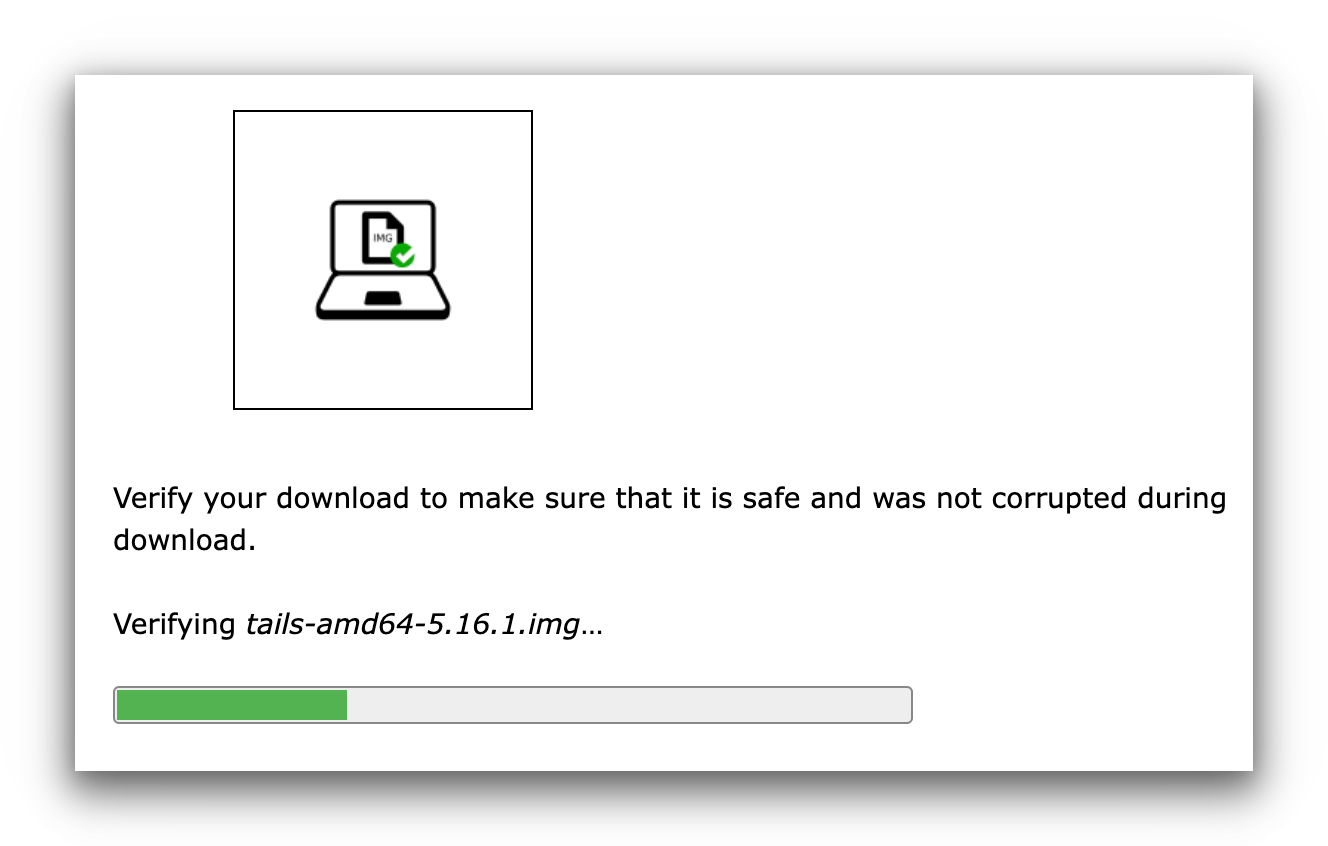
Verify your Tails download.
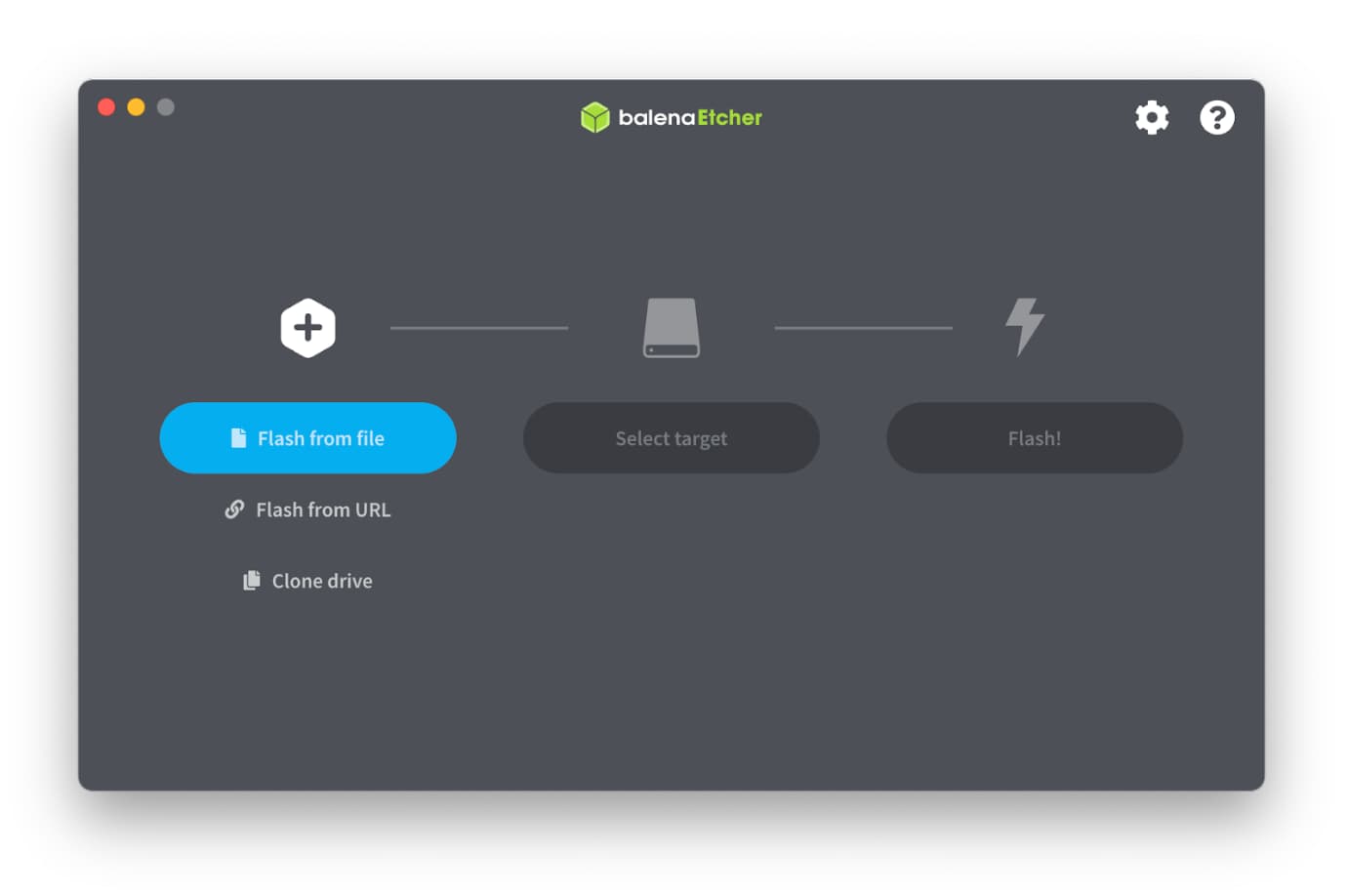
Choose the option to Flash from File.
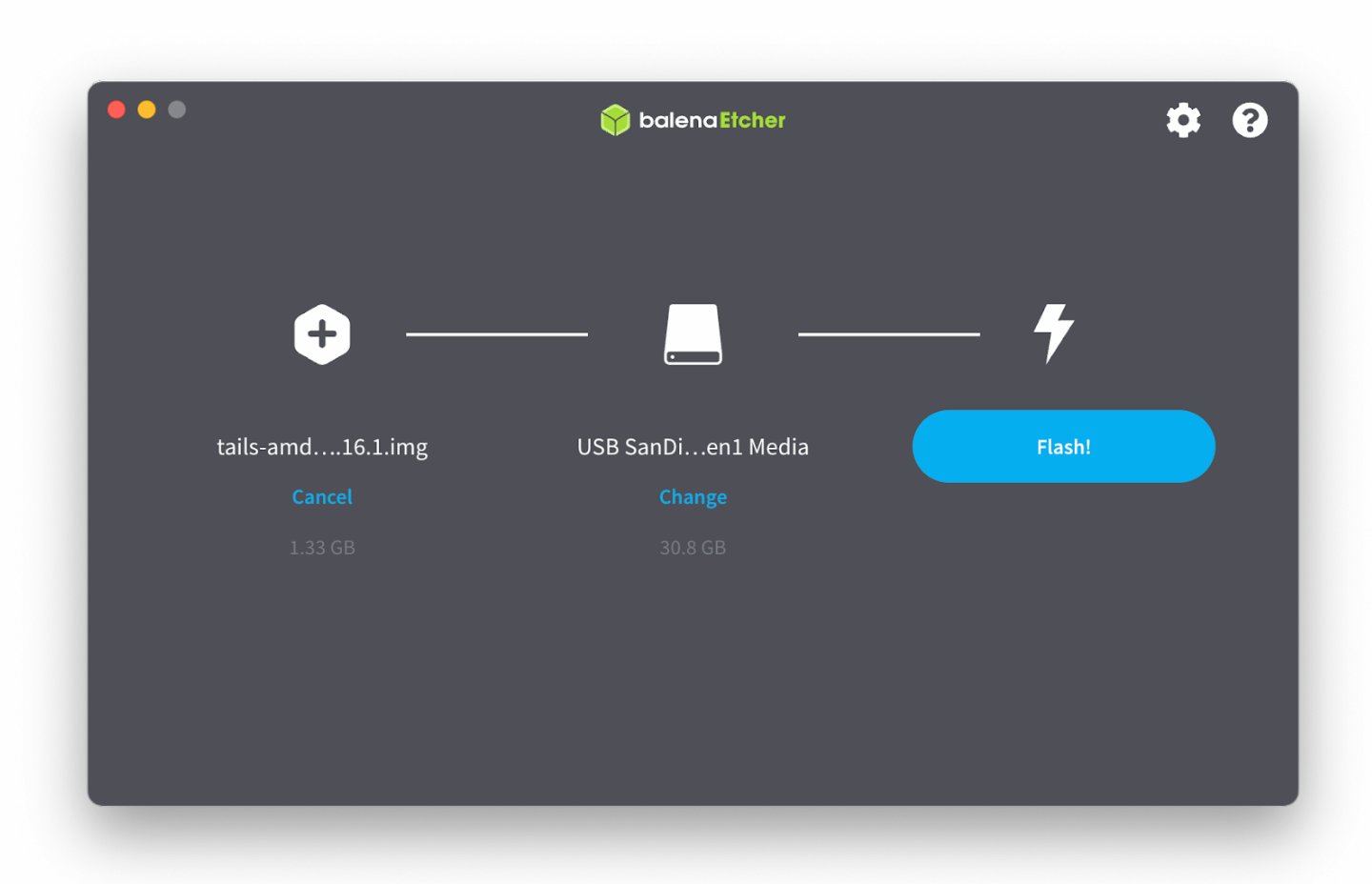
The file and USB stick should look like this.
Reboot on Your Tails USB Drive
Now you’ve downloaded Tails, you’ll need to restart your computer to use it to browse the dark web. Here’s how:
- Insert your USB drive into your computer.
- On macOS, restart your device, immediately press and hold down the Option key until a list of possible startup disks appear. On Windows, go to Start > Power > Restart. In the Choose an option screen, choose Use a device > Boot Menu.
- Choose EFI Boot on macOS and press enter. On Windows, select your USB drive and press enter. Do not select your usual startup disk. If you do accidentally select your original OS, you can simply restart your device and try again.
- Once selected, Tails will start up automatically and you’ll see a dark screen.
You can see the Tails logo in the middle of the screen.
Set Up Tails
At this point, Tails is downloaded, installed, and started. You now need to configure it for browsing the dark web safely. Here’s how:
- After one to two minutes, the welcome screen will appear, and you can select your Language & Region, as well as your Keyboard Layout. We recommend ignoring the Persistent Storage setting, which allows you to save files, bookmarks, and Wi-Fi passwords on your USB.
- Click on the blue “Start Tails” button.
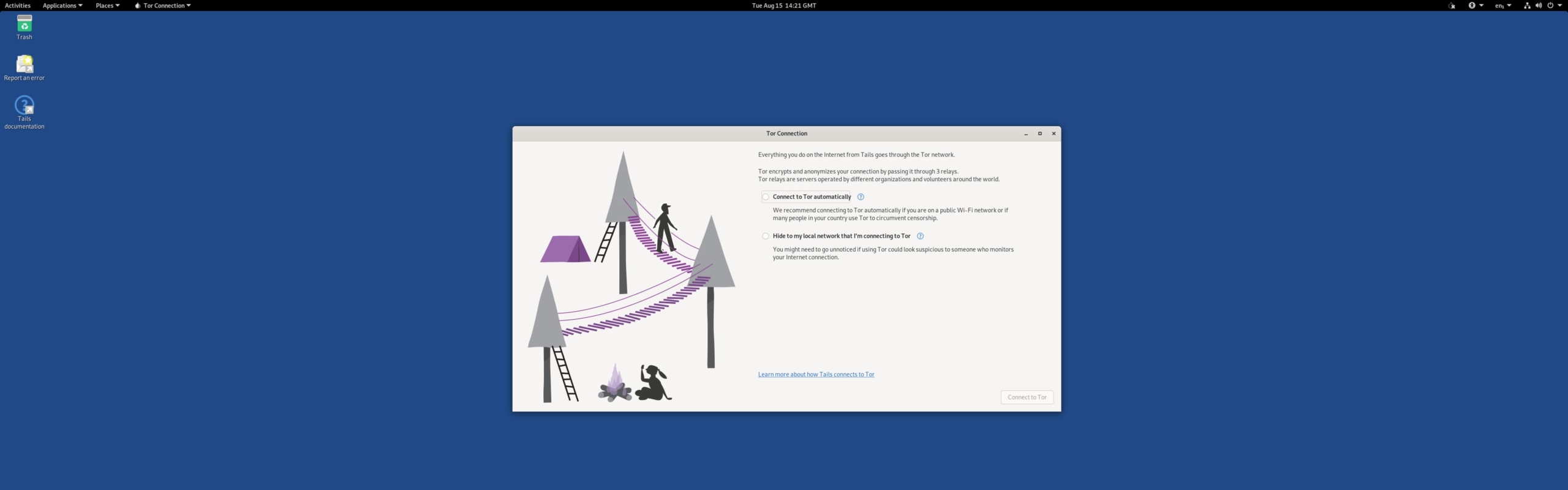
- After 30 seconds, you’ll see the Tails desktop screen. Click on the drop-down menu in the top-right corner and click on WiFi > Select Network. Select your home WiFi network.
- Once connected to the internet, a pop-up window will automatically appear. Select “Connect to Tor” automatically if you’re in the US, UK, or any other country that doesn’t block Tor connections. If you’re based in a country that blocks Tor, connect to a Tor bridge by selecting “Hide to my local network that I’m connecting to Tor“.
- You’re now connected to the Tor network on Tails, and can browse the dark web.
Can You Use a VPN with Tails?
Many users want to use a combination of a VPN and Tails to protect themselves on the dark web.
The Tails official website currently states the Tails system isn’t compatible with VPNs. It uses a firewall to block all VPN connections within Tails OS, and there isn’t a way to configure a VPN connection within Tails.
However, in April 2023, the Tails project started researching new ways to incorporate VPNs into the Tails OS. One possible solution is a new version of Tails that uses a VPN connection (instead of Tor) for the whole system and offers a Tor browser for accessing the dark web.