Top10VPN is editorially independent. We may earn commissions if you buy a VPN via our links.
What Is Onion Over VPN & Is It Safe to Use?
Overview
Onion over VPN, also known as Tor over VPN, is when you connect to a VPN before using the Tor browser. It’s a privacy solution designed to protect your online identity by adding an additional layer of encryption before your traffic reaches the Tor Network. It combines the Tor Browser’s anonymity with a VPN’s security.

Onion over VPN combines the use of a Virtual Private Network (VPN) and The Onion Router (Tor) to amplify the anonymity and security of your browsing traffic.
Also known as ‘Tor over VPN’, it refers specifically to the process of connecting to a VPN server before connecting to Tor. When done in reverse, the solution is referred to as VPN over Tor. These methods have different privacy and security implications, which we explain later on in this article.
Summary: Onion Over VPN Explained
- Onion over VPN involves connecting to a VPN server before connecting to Tor.
- This technique adds an additional layer of privacy and encryption to your browsing traffic.
- Onion over VPN is safer than using Tor alone as it helps to protect against traffic correlation attacks and malware.
- Users are still at risk from malicious exit nodes and UDP data leaks.
- Tor over VPN is extremely slow and can impact your anonymity. Deciding if Onion over VPN is worth it is therefore circumstantial.
Why Trust Us?
We’re fully independent and have been reviewing VPNs since 2016. Our advice is based on our own testing results and is unaffected by financial incentives. Learn who we are and how we test VPNs.
How Onion Over VPN Works
While both tools are designed to encrypt your web traffic and hide your public IP address, there are many differences between the Tor browser and VPN software. Tor focuses on providing complete anonymity, while VPN software focuses on online privacy.
Users can combine the two tools in an attempt to enhance their privacy and security when accessing the Tor network. To achieve this, you can connect to a VPN server before using Tor. This is known as Onion over VPN.
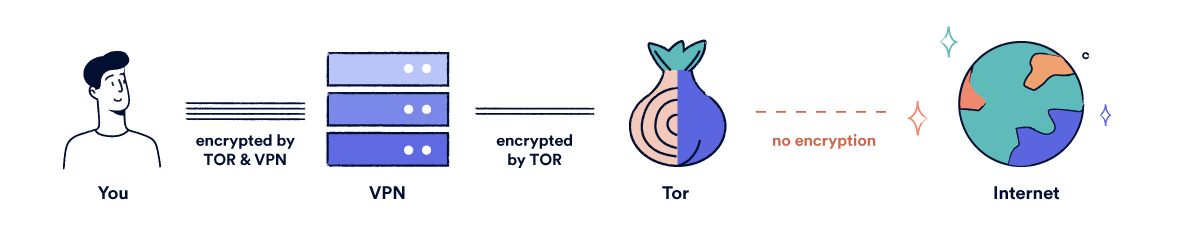
How Onion over VPN works.
Here’s how Onion over VPN actually works to anonymize your traffic:
- When you connect to a VPN server, the VPN software creates an encrypted tunnel between your device and a remote VPN server, concealing your browsing activity and IP address from your ISP (Internet Service Provider) and other third parties.
- If you use the Tor browser while connected to the VPN, the guard node (the first Tor node) will see the IP address of your VPN server instead of your own public IP address. This adds an additional layer of privacy.
- Your browsing traffic is decrypted once it leaves the VPN server, though it still carries the VPN server’s IP address.
- As your traffic travels through the Tor network, it is bounced through three ‘nodes’ in different locations: the guard node, the middle node, and the exit node. This adds three additional layers of Tor encryption. At each node, a layer of encryption is removed.
- At the exit node, your traffic is decrypted before it reaches its final destination. The Tor exit node is able to see the contents of your browsing data, but it does not know the VPN IP address.
Most users access the Tor network using the Tor browser. However, some VPN services offer native support for Onion over VPN, allowing direct access to Tor in a normal internet browser.
Put simply, the VPN server acts as an extra node in the data transfer. Four layers of encryption protect your traffic when using Onion over VPN, while only three layers of encryption are applied when using the Tor browser alone.
Is Onion Over VPN Actually Safe?
Connecting to a VPN before using the Tor network provides an additional layer of privacy and security compared to using the Tor browser alone. This means you can use Onion over VPN to improve your safety on Tor, but you cannot rely on it entirely.
Onion over VPN helps to protect your traffic and shield your browsing from surveillance. It prevents your ISP from knowing Tor is in use, and stops your VPN service from monitoring your activity.
However, it is extremely slow and inconvenient compared to using the Tor browser alone. For this reason, we only recommend using this setup in extreme circumstances where security is pivotal.
In the table below, we’ve compared the pros and cons of Onion over VPN so you can decide if it’s worth it:
| Pros | Cons |
|---|---|
| Provides an additional layer of encryption | Cannot control IP address location |
| Can access the Tor network in geo-blocked locations | Extremely slow connection speeds |
| Your ISP cannot see that you’re using Tor | Exit nodes are frequently blocked by websites |
| Your VPN service cannot monitor your browsing activity | Your VPN service will know you’re using Tor, but not what you’re doing |
| The Tor guard node cannot see your IP address | Your VPN service knows your IP address |
| Protects against certain forms of malware | Tor only support TCP protocol |
| Protects against complete de-anonymization in traffic correlation attacks | At risk from malicious exit nodes |
Here’s a more detailed overview of how Onion over VPN offers additional security, and how it doesn’t:
Your ISP and VPN Service Cannot Monitor Your Activity
Tor is associated with criminal activity due to its affiliation with the dark web. For this reason, the use of Tor can mark you for surveillance by the government.
Using Onion over VPN reduces the likelihood of this surveillance as your ISP (Internet Service Provider) will not know you are connected to Tor.
Your VPN service will know you are connected to Tor. However, it cannot see your browsing activity within the network. Even if your VPN keeps connection logs, there is no way for your VPN provider to see exactly which websites you access within the Onion network.
Additionally, the Tor guard node will be unable to see your true IP address – only the IP address of your VPN server. This provides an additional layer of privacy.
Risk of Malicious Exit Nodes
A VPN encrypts all web traffic between your device and the VPN server. When using onion over VPN, your traffic is decrypted after passing through the VPN server and sent on to the Onion network.
Within the Onion network, your traffic is then encrypted and decrypted three more times before reaching its destination. The traffic is decrypted at the exit node, which means third parties can see what you’re doing but not who is doing it.
Tor is a community-based network where anyone can set up multiple nodes and, in theory, spy on your activity. When an exit node is set up to spy on or exploit Tor users, this is known as a malicious exit node.
If you access web servers via HTTP (Hypertext Transfer Protocol) when using Onion over VPN, your traffic is not encrypted between the exit node and the web server. This leaves you vulnerable to malicious exit nodes as your traffic is visible.
However, if you access web servers via HTTPS (Hypertext Transfer Protocol Secure) when using Onion over VPN, your traffic is still encrypted between the exit node and the web server. Although exit nodes will see the data packets transmitted, they cannot decrypt them.
Protection from Malware
Tor is often compromised by malware. When using Onion over VPN, your VPN can act as a barrier between your device and ransomware by shielding open ports through the firewall on the VPN server.
Open ports receive and transmit TCP and UDP communications. While open ports normally aren’t dangerous, they can be used to spread malware and gain unauthorized access to personal information on your device.
Although VPN software is not designed to protect you from malware, a VPN firewall can help prevent port forwarding which stops infiltrators accessing your device. This offers a degree of protection against malware, making Onion over VPN safer than Tor alone.
Security Against Traffic Correlation Attacks
Traffic correlation attacks occur when third parties observe your traffic to find a correlation between incoming and outgoing data.
It’s possible to analyze the timing, behaviour, and volume of traffic to identify the websites you are using at particular times. Onion over VPN can prevent attackers from completely de-anonymizing you, as your true IP address is hidden by VPN software.
If a government or state agency is behind the traffic correlation attack, they are still capable of legally forcing your VPN service to hand over any records they have related to the associated VPN IP address.
If your VPN service keeps connection logs, it may be possible to match these to your identity. This is one of the many reasons it’s important to use a VPN service that only logs necessary data.
Protection From UDP Data Leaks
Tor only supports the TCP protocol. This means UDP traffic, including Voice-over-IP, will have to travel outside the Tor network. This traffic may expose your IP address and online activity to third parties – known as ‘bad apple’ attacks.
Onion over VPN provides a layer of protection against this form of attack. Any leaked UDP traffic would still be routed via the VPN server in an encrypted tunnel, which means they cannot be used to identify you.
Data leaks can still happen if the VPN connection is lost, which means it’s important to understand which traffic is able to travel through the Tor network and adapt your online activity accordingly.
Access to Tor in Geo-Blocked Countries
It is legal to use Tor in most countries around the world. However, there are still some places where it’s banned, including Belarus, Turkey, and China.
VPN software allows users to mask their true location by connecting to a VPN server in a different country. This means you can use a VPN to download and use the Tor browser in highly-censored countries.
Some websites block traffic from Tor IP addresses, which means you may still have difficulty accessing some services with Tor. To solve this issue, using VPN over Tor would be a better solution.
If Tor is blocked in your country, connect to a VPN first to access geo-restricted content.
When to Use Onion Over VPN
Onion over VPN is generally recommended for users transmitting highly-sensitive information that might benefit from an additional layer of encryption. Whistleblowers and journalists in high-censorship countries can utilize this setup to bypass geo-restrictions and access the Tor Network.
You should use onion over VPN if:
- Anonymity is of the utmost importance
- You cannot access the Tor Network directly
- You are a journalists, whistleblower, or activist
Do not use Onion over VPN if:
- You are browsing the internet casually
- You are accessing identifying websites (e.g. social media)
- Speed is of the utmost importance
This method can protect your device from ransomware and traffic correlation attacks, but it will not protect you from malicious exit nodes. As always, it is important to be cautious when using Tor. Due to the adverse effects on connection speeds, this method is not recommended for casual users.
Remember: you will never be 100% anonymous. VPNs do not offer pure anonymity, and your VPN service is technically able to see you have accessed the Tor browser. Ultimately, you are shifting your trust from your ISP to your VPN.
Whether Onion over VPN is worth it is therefore circumstantial. The setup provides some additional privacy and security, but it cannot protect you against malicious users within the Onion network.
How to Use Onion Over VPN Safely
In the video below we demonstrate how to safely use Onion over VPN with NordVPN:

How to use NordVPN's Onion over VPN feature.
If you do decide you use Tor over VPN, this section will teach you how to use it safely.
In fact, Tor over VPN is incredibly easy to set up. You simply need to connect to your VPN before launching the Tor browser.
Follow these steps to set up Tor over VPN safely:
- Subscribe to a no-logs VPN service, or pick from our best VPNs for Tor shortlist. We recommend using Private Internet Access with Tor as it combines a zero-logs policy with fast speeds and affordable pricing.
- Connect to a VPN server. Choose a remote VPN server and connect to it. The closer it is to your real physical location, the faster your speeds will be.
- Download the Tor Browser from the official Tor website.
Make sure you download the Tor Browser from the official website.
- Click your device’s icon and follow the installation prompts to automatically install the Tor Browser on your device.
- Launch the Tor Browser while still connecting to the VPN server.
- Browse anonymously. While browsing, it is important to avoid connecting to websites that might jeopardize your anonymity. This includes logging into personal online accounts or sending emails.
Onion Over VPN vs. VPN Over Tor
The Tor Browser and VPN software can also be combined in reverse. Here, the Tor browser is launched before you connect to a VPN. This is the opposite of onion over VPN, known as VPN over Tor.
VPN over Tor first sends your traffic through the Tor network, after which it is routed through the encrypted VPN tunnel. Unlike onion over VPN, exit nodes are not able to see the contents of your traffic, but guard nodes are able to see your real public IP address.
The Tor Project warns users against using a VPN over Tor as it undermines your anonymity.
Use the table below to understand the pros and cons of using a VPN over Tor:
| Pros | Cons |
|---|---|
| Protection from malicious exit nodes | Guard node can see your public IP address |
| VPN kill switch prevents data leaks | Complex to set up |
| Websites that block exit nodes are still accessible to Tor users | Choice of VPN service is limited |
| Extremely slow connection speeds | |
| Double encryption is excessive | |
| Your VPN service can theoretically monitor activity | |
| ISP can see you are connected to Tor |
VPN over Tor is complex to set up and less anonymous than Onion over VPN. Direct help from your VPN service is required, which means your choice of VPN will be limited.
We do not recommend setting up VPN over Tor unless you are technically proficient. An incorrect setup can result in traffic leaks which may compromise both your anonymity and security.
Here’s an overview of how VPN over Tor affects your privacy and security:
Your VPN Service Can Monitor Your Activity
The Tor project warns users against VPN over Tor as it gives your VPN provider access to both your IP address and the contents of your web traffic, defeating Tor’s primary focus: complete anonymity.
Some VPN services keep records of your online activity. If you use one of these VPN services after connecting to Tor, your online activity will be entirely traceable.
You Can Be Marked For Surveillance
If you connect to Tor before connecting to a VPN, the Tor guard node is able to see your public IP address. Though it is unable to decipher the contents of your web traffic, it is less private.
Without connecting to a VPN server first, your ISP will also be able to see that you’re using Tor. This can mark you for surveillance by government authorities including the National Security Agency (NSA).
The NSA obtains and stores the IP addresses of thousands of Tor users. This information is collected by XKeyscore, a computer system designed by the NSA for analysing online activity.
Protection from Malicious Exit Nodes
Despite its privacy and anonymity drawbacks, VPN over Tor does provide an extra layer of protection from malicious exit nodes.
Unlike Onion over VPN, Tor exit nodes cannot see your data if you connect to a VPN after connecting to Tor. The VPN will encrypt all traffic from the exit node to the internet, which means the exit node knows that you are connected to VPN software, but not which websites you’re visiting.
If your VPN connection is lost, a kill switch will disconnect your device from the internet. This prevents your IP address and other sensitive information from being disclosed. In combination, these factors make it significantly harder for third parties to exploit your information using malicious exit nodes.
Access to Websites That Block Tor Traffic
Websites that are blocked to Tor IP addresses are also made accessible when using VPN over Tor. These websites will receive your decrypted traffic from the VPN server, which means they will not see the IP address of the Tor exit node. As a result, you can access websites that are usually blocked in the Tor Browser.
How Is Double VPN Different from Onion Over VPN?
Also known as ‘multi-hop VPN’, Double VPN is an advanced feature offered by some VPN services for extra security. Simply put, it routes your traffic through two different VPN servers instead of one.
NordVPN’s Double VPN feature is found in the protocol menu.
While Double VPN and Onion over VPN might appear similar, they are structurally different. Onion over VPN connects users to two different types of anonymity software, whereas Double VPN routes your traffic through one type of software, twice.
Here’s a list of the key similarities and differences between Double VPN and Onion over VPN:
Similarities:
- Double VPN and Onion over VPN both result in significantly slower connection speeds.
- Both setups encrypt your web traffic more than once.
- Onion over VPN will hide your IP address from the guard node. Double VPN will hide your IP address from the second VPN server.
Differences:
- Onion over VPN utilizes two types of anonymity software: VPN software and the Tor Browser. Double VPN only uses VPN software, which centralizes your risk.
- Onion over VPN encrypts your data four times, while Double VPN only encrypts it twice.
- Double VPN supports both the UDP and TCP protocol, while onion over VPN only supports the TCP protocol.
- You cannot access the dark web or .onion websites with Double VPN. Onion over VPN supports access to the dark web.
Like Onion over VPN, Double VPN is designed to obscure your online activity from your ISP and other intrusive third parties. It encrypts your data twice, and has a significant impact on your connection speeds.
The second VPN server in the Double VPN setup only sees the IP address of the first VPN server. Some users consider this an additional layer of protection, but it is largely unnecessary for most users.
One layer of AES-256 encryption is enough to prevent snooping by third parties. In addition, the VPN service still owns and controls the network you’re using. If they wanted to, it’s technically possible for them to trace your traffic back through the network.
Unlike Onion over VPN, Double VPN centralizes your risk as you put all of your trust in the VPN service.