Android Proxy Apps Investigation: What Are The Privacy Risks?
Analysis of 20 of the most popular proxy Android apps reveals nearly 185 million peoples' privacy is at risk.

- Tested: We analyzed 20 of the world’s most popular proxy Android apps with 184 million installs between them to identify any potential risks to their users’ privacy.
- Risky Permissions: 9 proxy apps contain permissions with highest risk to privacy, and a further 6 feature permissions of some concern.
- Yandex & Bytedance: 5 proxy apps contain code from or phone home to one of these controversial Russian and Chinese companies.
- High risk functions: 20 apps contain high risk functions, including 4 that declare use of GPS and 4 that declare use of camera.
- Location tracking code: 15 apps contain location tracking code for reasons other than displaying local IP address.
- First-party data collection: Our analysis uncovered first-party code that queried the following:
- Device & SIM card details (10 apps)
- Location data (7 apps)
- Contact list (6 apps)
- Sharing user data: Our analysis uncovered code whose function was to share the following data with third parties:
- Location data (9 apps)
- Device & SIM card details (8 apps)
- Unique device ID (8 apps)
- Google Ads: was the most frequently found third-party code with implications for privacy (15 apps), followed by Facebook (11 apps)
- Device fingerprints: 12 apps harvest detailed device fingerprints (11 also share this data with third parties)
- User IP addresses: 4 apps collect and share this data
Privacy Risks of Android Proxy Apps
Accessing the internet via a proxy server is a very popular way to change your IP address and circumvent basic content restrictions. Proxies are particularly appealing wherever low internet speeds are an issue, as they can be faster than other types of circumvention software.
Proxy servers can be accessed a number of ways, such as from within the browser or by changing a device’s network settings. One of the easiest ways to connect to a proxy server on a mobile device however is via one of the many dedicated proxy apps available in the app stores.
Proxy apps have a number of similarities with VPNs (Virtual Private Networks) in terms of how they work and also share a near-identical user interface. For the average user, this could lead to an unrealistic expectation of privacy.
In light of their popularity and similarity to VPNs, we decided to investigate 20 of the world’s most popular proxy Android apps in order to determine the potential privacy risks associated with their use.
These 20 proxy apps have so far amassed 184 million installs in total from Google’s Play Store.
We focused on Android as it’s the mobile operating system with by far the largest reach, particularly in the global south where proxies have a significant user base.
We identified apps for inclusion in our research by reviewing the Google Play Store search results for the term “proxy” in multiple locales.
How We Tested The Proxy Apps
In order to identify the potential privacy risks associated with these proxy Android apps, we primarily analyzed their source code and performed network traffic analysis.
We also scanned each APK (Android Package Kit) file using VirusTotal for any security issues.
Why Did We Do This Research?
We’ve been highlighting the dangers of free VPN apps for everyday internet users since 2018. There is substantial overlap between the Play Store search results for this search and for “VPN”. This is largely due to app developers agressively optimizing their listings to try to appear high up on both sets of results pages. The most popular proxy and VPN apps tend to be listed with names that are a string of keywords, often including the words “VPN” and “proxy”, that bear little relation to the name of the app once installed on a device.
As a result, it’s often unclear exactly what type of software is being installed. This deliberately confusing situation further prompted us to assess the privacy risks associated with proxy apps. While proxy apps do come with a general expectation of privacy, that expectation is much higher if a user is under the misapprehension that they are using a VPN.
PROXY Vs VPN: WHAT’S THE DIFFERENCE?
- Most proxies don’t encrypt internet traffic, unlike a VPN.
- A proxy is often faster than a VPN, but not always.
- Proxies are less effective at circumventing sophisticated internet restrictions
For a more detailed explanation, read our guide on the differences between VPNs and proxies.
Proxy Apps Privacy Analysis Findings
The following table provides a summary view of all the findings of our privacy investigation into 20 of the most popular proxy Android apps. Click the Expand Table button below right for a fullscreen view and scroll horizontally and vertically to see all the data.
The apps are listed in descending order by number of installs.
You can also access the data via a Google Sheet.
In the table’s column headings, 1P and 3P refer to first- and third-party code. Core Android refers to the fundamental common components of the Android platform.
<
For more detail on specific elements of the analysis and definitions of key terms, use the following jumplinks:
While we dive into individual apps that stood out during specific aspects of our investigation, such as those with the most egregious permissions or that share the most detailed device fingerprints, there were also a handful of apps that caught our particular attention overall.
With 50 million installs each, Proxy Speedfiy (com.free.speedfiy) and VD Browser & Video Downloader (vpn.video.downloader) merit particular attention due to their incredible global reach.
Proxy Speedfiy appears to be trying to exploit its huge user base by inserting TikTok ad tracking code into its app. What this means for Proxy Speedfiy users is that their internet traffic will be monitored while using the proxy app and sold to the social media company to allow it to better target them ads. Proxy Speedfiy also invades its users’ privacy by sharing detailed fingerprints of its users’ devices to adtech platforms Vungle and Adjust.
VD Browser & Video Downloader, which is a proxy app that’s focused around dowloading videos and other online content, requests some alarming permissions, including use of the camera and recording audio and declares the use of this hardware in the app’s Android manifest file. This proxy app also shares its users’ location data with Facebook and Google.
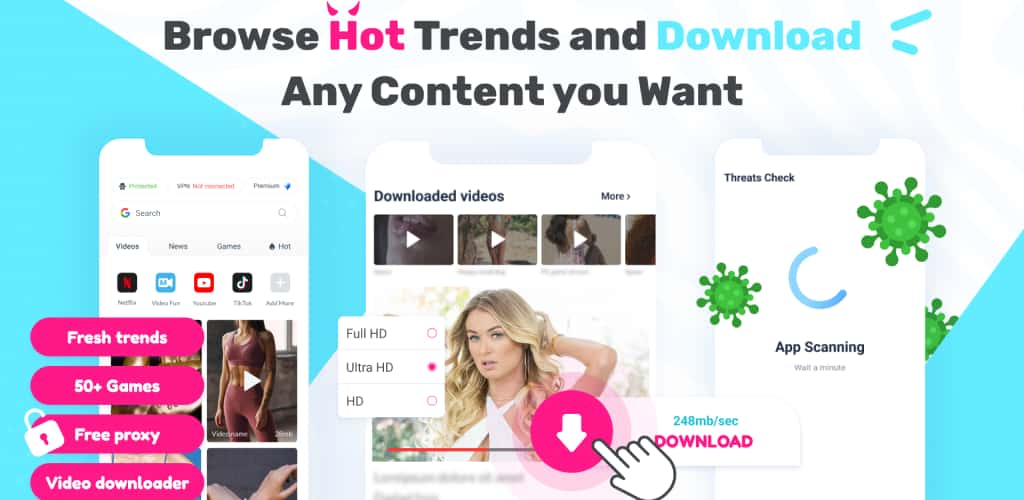
Marketing material for VD Browser & Video Downloader proxy app.
Although EasyConnect has far smaller reach with 1 million installs, it poses a potentially serious risk to users. Respected malware scanner VirusTotal flagged its APK com.gnostic.proxy.easy as “Malware Banker Trojan Evader”.
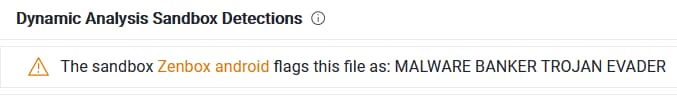
Screenshot of VirusTotal scan results for EveryConnect proxy app.
EasyConnect was also the only proxy app to request the elevated permission READ_PRIVILEGED_PHONE_STATE, which allows it to access protected device data on devices running older versions of Android. It was also one of four proxy apps that looked up all other apps installed on the host device, which Google states is against its policies unless required as part of an app’s core functionality, which is not the case here.[1]
Riskiest Proxy App Permissions
The following table lists the app permissions we discovered during our analysis that have implications for users’ privacy and/or felt inappropriate for a proxy app.
The table lists the permissions in descending order of the number of times they appear in the 20 proxy apps tested.
| Permission | Definition | Found in (apps) |
|---|---|---|
READ PHONE STATE |
Allows an app to determine the phone number, device IDs, whether a call is active, and the remote number connected by a call. | 8 |
ACCESS FINE LOCATION |
Provides most precise device location possible, accurate to 10 feet or better, using GPS, WiFi and mobile cell data. | 6 |
ACCESS COARSE LOCATION |
Provides approximate device location, accurate to within around 1.2 square miles. | 6 |
MODIFY AUDIO SETTINGS |
Allows an app to modify a device’s global audio settings. | 5 |
RECORD AUDIO |
Allows an app to record audio. | 3 |
QUERY ALL PACKAGES |
Allows an app to have visibility over what other apps are installed on the device. | 2 |
BLUETOOTH |
Allows applications to connect to paired bluetooth devices. | 1 |
BLUETOOTH ADMIN |
Allows an app to discover and pair with a bluetooth device. | 1 |
DOWNLOAD WITHOUT NOTIFICATION |
Allows an app to download files through the download manager without notifying the user. | 1 |
READ PRIVILEGED PHONE STATE |
Provides highest-level access to phone details (on older versions of Android). | 1 |
Almost a third of apps we tested seek permission to track users’ precise location. This is deeply sensitive personal data that can reveal much about someone’s health, beliefs, financial status and even sexual activity and orientation, simply from tracking and logging the places they visit on a daily basis while the app is running.
Not only is such data packaged up and potentially sold by the app developers but it’s also harvested directly by third parties, such as Google and Facebook, whose SDKs (Software Development Kits) we frequently found embedded in the apps.
In extreme cases, smartphone users have found themselves caught up in law enforcement investigations based on their location data.[2]
We found that 8 apps featured the READ_PHONE_STATE permissions, which allows an app to collect a device’s identifying information that’s typically then used for tracking purposes, often in combination with location data.
It’s a major red flag that as many as three apps sought permission to record audio as there is no credible reason for a proxy app to do such a thing.
It’s notable when looking at permissions and our analysis of the apps’ source code together that they are not in perfect alignment. For example, many more apps contain location tracking code than seek permission to execute that code. While it’s true that code without the appropriate permission is currently dormant, there is nothing to prevent future app updates to introduce the relevant permission.
In the case of location tracking, it’s unlikely that a developer would include such code in first party components without hoping to use it. This is in contrast with third-party libraries where the omission of relevant permissions is the only realistic way to exclude any unwanted functions.
The READ_PRIVILEGED_PHONE_STATE permission has been restricted to system apps since the launch of Android 10 in 2019. It’s now required to access non-resettable device identifiers.
As this permission has simply not been available to an app like EasyConnect for the last several versions of Android, its presence in the app’s Android manifest file raises red flags. Whether by negligence or design, this permission potentially exposes the IMEI and serial numbers of any device still running Android 9 or earlier. Older versions of Android persist in significant numbers: almost 13% of Android devices worldwide were running versions 8 and 9 of the operating system as of April 2023.
Source Code Analysis
We analyzed the source code of each proxy app to identify functions which potentially put user privacy at risk when using these apps.
We divided the results of this analysis into two parts, looking first at privacy intrusive functions within first-party and core Android components. Any data generated by these functions would be harvested directly by the developer but could then be potentially sold on or used in other ways to generate a profit.
We also identified any code within third-party libraries that might impact user privacy.
Risky First-party App Code
The following table lists the 10 first-party and core Android app functions we discovered most frequently during our analysis of the apps’ source code that have implications for users’ privacy and/or felt inappropriate for a proxy app.
The table lists the functions in descending order of frequency of detection by number of apps among the 20 proxy apps we tested.
| Function | Found in (apps) |
|---|---|
| Queries phone & SIM details | 10 |
| Queries the SIM provider mobile country code & mobile network code | 7 |
| Queries phone location | 7 |
| Queries contact list | 6 |
| Queries Android advertiser ID | 6 |
| Queries phone & SIM details, inc IMEI number | 4 |
| Queries list of installed apps | 4 |
| Declares use of GPS | 4 |
| Declares use of camera | 4 |
| Declares use of camera & autofocus | 3 |
| Makes itself visible to major social media platforms | 1 |
| Can modify web pages | 1 |
| Declares use of microphone | 1 |
| Queries phone configuration | 1 |
The functions in the above table can mostly be divided into two broad types. The first and most frequently discovered in our analysis relates to data collection.
Almost three quarters of the apps we tested (13) contained first-party code that collected personal data about users’ devices and SIM cards. This number rises to 15 when also looking at code in third-party libraries. Examples of such code include:
getDeviceIdgetImeigetMccMncgetPhoneTypegetNetworkOperatorgetNetworkOperatorNamegetNetworkCountryIsogetSimOperator
A device’s IMEI number is its unique 15-digit serial number, while getMccMnc refers to its mobile country code and mobile network code.
Note that IMEI numbers have been protected beind the READ_PRIVILEGED_PHONE_STATE permssion that’s only available to system apps since Android 10 in 2019. However, older versions of Android, which make up 13% of all devices worldwide, only require the lesser READ_PHONE_STATE permission to be in place to allow collection of that data.
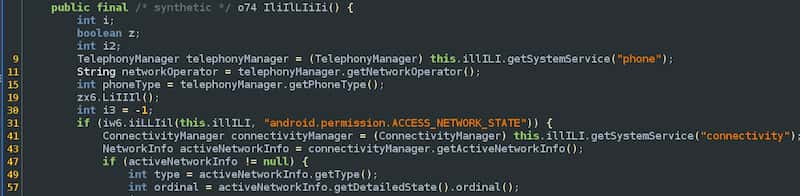
Screenshot of source code in the Rain Proxy Android app that collects data about a user’s phone and SIM card.
As well as detecting first-party code that enables tracking of users’ online behavior by identifying their devices, we also frequently discovered code that tracked users’ physical location in functions either created directly by the app developer, or within core Android components. Note that we excluded common components with clearly benign functionality, such as Android’s night mode that makes use of a device’s approximate location to determine when to dim the lights.
Four apps contained code that creates a list of all other apps installed on a user’s device. Google explicitly states that the “inventory of installed apps queried from a user’s device [is] personal and sensitive information”, which should only be accessed by apps whose core functionality requires it. It’s clear that proxy apps don’t meet this criterion and should not contain such code.
The other type of first-party code we discovered related to inappropiate use of hardware, such as the camera or microphone. Four apps contained such code, while one of them (UPX) featured code for both mic and camera. There’s no credible reason why a proxy app should contain first-party code of this kind.
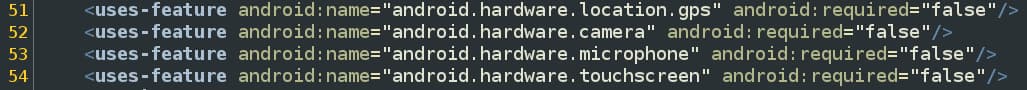
Screenshot of source code in the UPX proxy Android app that invokes the device camera and microphone.
Risky Third-party App Code
The following table lists the types of third-party code that we discovered most frequently during our analysis of the apps’ source code that have implications for users’ privacy and/or felt inappropriate for a proxy app.
The table lists these third-party library functions in descending order of frequency of detection in the 20 proxy apps we tested.
| Function | Found in (apps) |
|---|---|
| Contains third-party tracking code | 18 |
| Queries phone location | 9 |
| Queries phone & SIM details | 8 |
| Queries Android advertiser ID | 7 |
| Queries contact list | 2 |
| Queries device ID | 1 |
| Creates a geolocation record | 1 |
| Connects to Yandex | 1 |
Most common third-party SDK providers
The following chart shows the five third-party providers of SDKs with protential privacy impacts that we found most frequently in our app code analysis. They are ordered by the number of apps containing an SDK published by that provider. There were 11 providers in total whose SDKs we flagged as a potential privacy risk.
Chart showing the 5 third-party SDKs with privacy implications most frequently found in the proxy apps we tested.
The privacy impacts of Facebook SDKs are well-documented, and while Google has promised to phase out cross-app tracking, this won’t be fully in place until 2024.[3][4]
These SDKs contained code that variously queried device location, device and SIM details and the Android Ad ID in order to better track proxy app users.
Applovin is a mobile app adtech platform, part of which is an ad exchange. Notably, the company recently acquired MoPub, which prior to acquisition was exposed for selling location data from Grindr.[5]
As well as looking up the same personal data as the Facebook and Google SDKs, Applovin code also connected with Russian search company Yandex.
Adjust is another tracking platform in a similar vein to Applovin.
Yandex and Bytedance
We found four apps that contained code from the Yandex AppMetrica SDK, which is the Russian search engine’s multi-purpose ad tracking and analytics platform. User data harvested by AppMetrica is processed and stored on Russian servers, while Yandex has close ties to the Kremlin.[6] Given Russia’s draconian approach to internet freedom, we would certainly advise against using apps that funnel your personal data into that jurisdiction.
Another app contained the Bytedance SDK, which is similarly risky from a privacy perspective. The TikTok developer remains under a cloud due to its suspect privacy practices and revelations that the Chinese company spied on journalists who had been critical of Bytedance via their smartphones.[7]
The SDK allows developers to share user data with TikTok. Its documentation explicitly states: “We may use this app event data for subsequent retargeting and dynamic product ads”.
Proxy Apps Network Traffic Analysis
Network traffic analysis involves capturing the stream of server requests made by an app and the responses it receives. The nature of this traffic is not only determined by how a user interacts with the app but also by the status of any first- and third-party servers involved.
While this type of analysis is ideal for collecting evidence of any data sharing in action, it won’t therefore always align perfectly with what’s specified in the code.
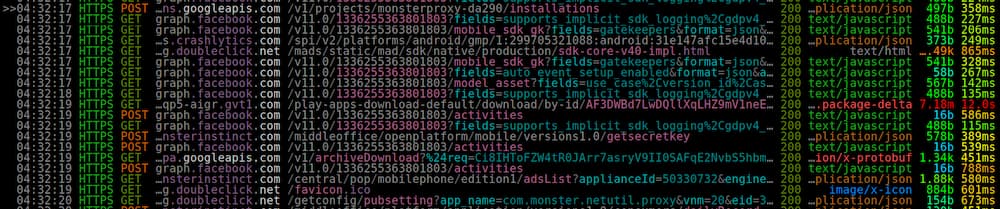
Screeshot of network traffic capture using mitmproxy.
When we captured and analyzed the network traffic generated by proxy apps, we found four categories of user data:
- Real IP address
- Highly-detailed device information with the potential for fingerprinting
- Unique Google Advertiser IDs
- Basic device information
The harvesting of a proxy app user’s real IP address and sharing it with third-parties is particularly problematic given the core functionality of a proxy involves hiding that information.
We found four apps that shared users’ IP addresses:
- IronMeta One
- Movie&Video Proxy
- Proton Proxy
- Proxy Speedfiy
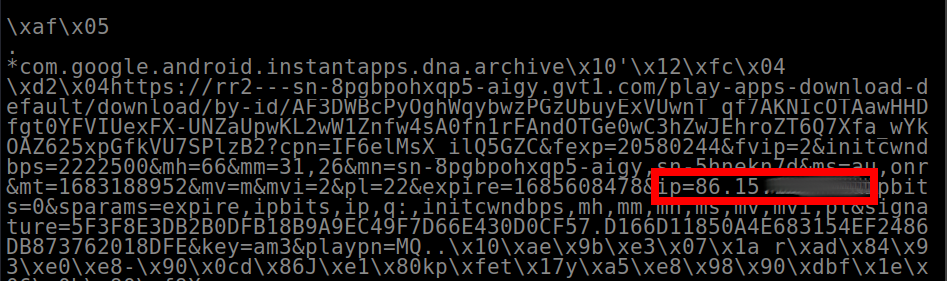
Screenshot of IP address sharing with Google on Proton Proxy Android app.
A fifth – Flag Proxy-Fast&Stable – shared the IP addresses of the proxy servers selected.
Device fingerprints are comprised of long lists of very specific data points. These varied from app to app but included:
- Device name (ie Simon’s iPhone)
- Network operator
- Free memory
- Battery level
- Screen brightness
- Device volume
- Screen height
- Screen width
- Free storage space
- Last time device was switched on
- Network connection type (ie WiFi)
- Android version
- Device model
- Language
As with browser fingerprinting, each data point on its own poses little risk to privacy. However, when harvested together, such a collection of granular information about your device makes it easy to to identify and track you across the internet.
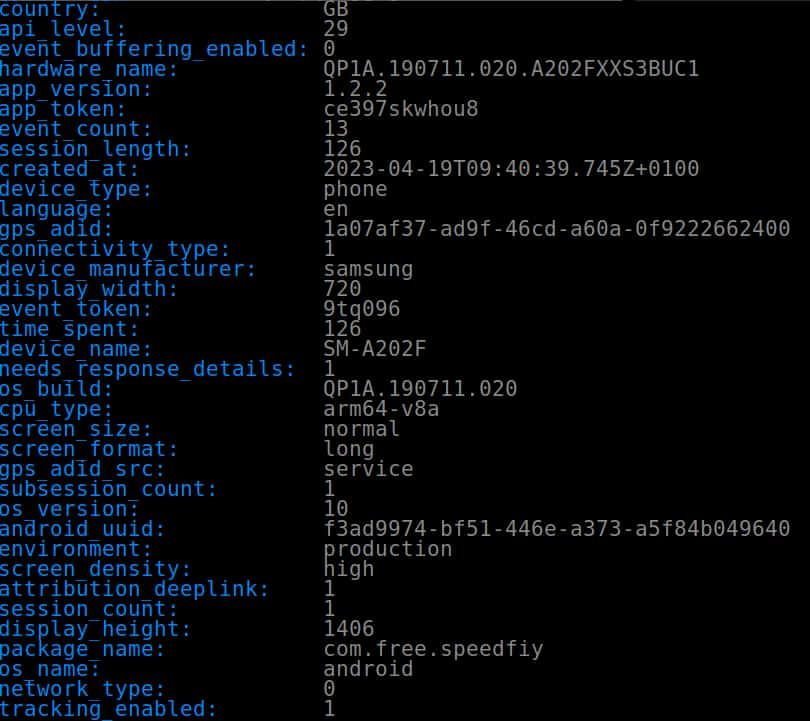
Screenshot of device fingerprinting on the Speedfiy proxy Android app.
Two apps (IronMeta One and VPN Proxy Browser & Downloader) went even further, collecting a vast array of device data, that included data points such as the manufacturer and model name of individual device sensors, along with other very specific hardware info. IronMeta One even harvests a string of data called a build_fingerprint about users’ devices.
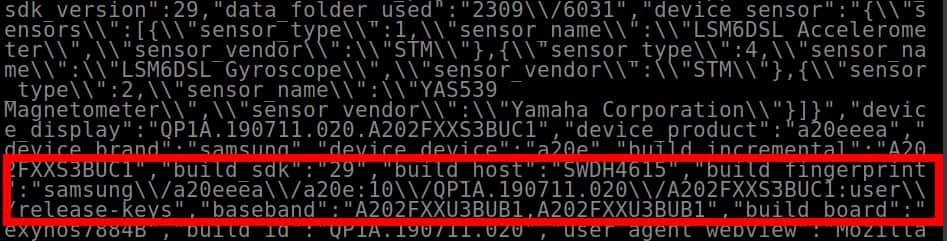
Screenshot of a portion of the device fingerprint data collected by IronMeta One proxy Android app.
Any data sharing with advertisers that was limited to device model, Android version, screen height and other general data points has been classified as “basic device information”.
This basic information on its own can’t strictly be used by advertisers to track you. However, we included it in our findings as it helps determine the overall privacy risk of each proxy app.
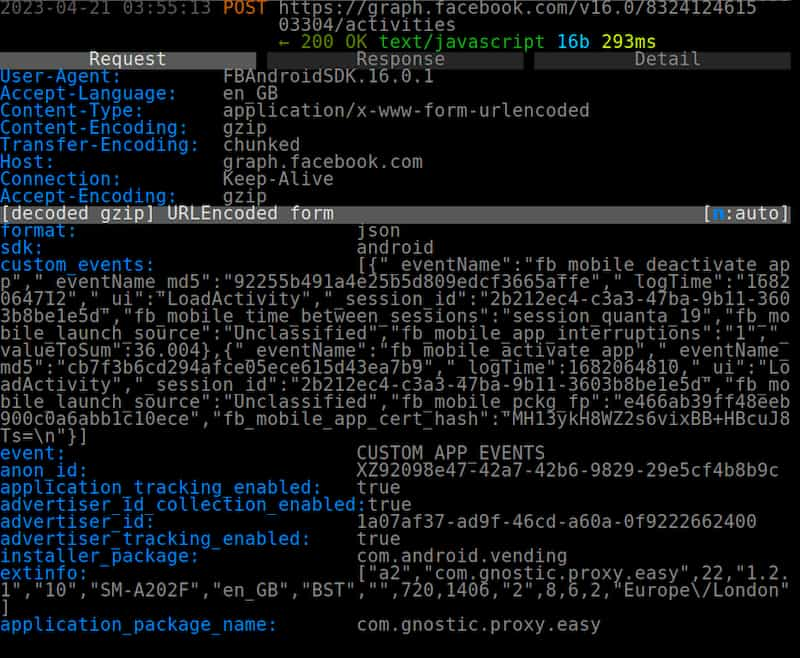
Screenshot of basic device information shared with Facebook by EasyConnect proxy app.
The Google Advertiser ID is a unique, user-resettable ID used to track users and provide personalized ads based on their internet browsing behavior. It is provided by Google Play services.
While the above data is sometimes harvested by the app developers themselves, in our tests we found it was more frequently shared with the following third parties:
- Vungle
- Adjust
- UserX
- Yandex
- Firebase
- Ad Colony
Facebook was by far the most common recipient of user data with 14 apps sharing data with the social media platform during our tests. While this was typically in the form of basic device info, apps also more often than not shared the Google Ad ID with Facebook, while one app – VPN Proxy Browser & Downloader – provided it with an extensive device fingerprint.
Traffic analysis revealed that nearly half of the apps (9) actively shared data with Google Ads. Other third parties we detected as receiving data included ad exchanges such as Vungle and Ad Colony. These platforms facilitate the trade of vast amounts of digital ad inventory and offer powerful tools that exploit user data to better target their ads.
Others were mobile monetization tools, such as Adjust, or user analytics platforms such as Firebase and UserX.
Methodology
We selected the 20 proxy Android apps with the highest number of installs that were discoverable via searches for “proxy” in the Play Store across a number of locales, including the U.S., UK, Pakistan, India, Algeria, Turkey and Egypt.
We analyzed their source code to identify functions with the biggest potential risk to users’ privacy. We also performed a network traffic analysis of each app using an Android test device and mitmproxy, an open source tool installed on our Linux-based dedicated testing environment.
We also scanned each APK (Android Package Kit) file using VirusTotal to help identify any security or other issues.
The data is available for download via this Google Sheet.
The authors of all our investigations abide by the journalists’ code of conduct.
References
[1] https://support.google.com/googleplay/android-developer/answer/10158779?hl=en-GB ↩
[2] https://www.nytimes.com/interactive/2019/04/13/us/google-location-tracking-police.html ↩
[3] https://privacyinternational.org/report/2647/how-apps-android-share-data-facebook-report ↩
[4] https://www.protocol.com/google-android-ad-tracking-apple ↩
[5] https://www.eff.org/deeplinks/2020/01/grindr-and-okcupid-sell-your-data-twitters-mopub-real-problem ↩
[6] https://www.dailysabah.com/business/tech/kremlin-ally-joins-tech-giant-yandex-as-senior-adviser ↩
[7] https://www.ft.com/content/0c0f9670-2e3a-4af8-bcd5-85e314f6ac5e ↩