Free VPN iOS App ‘Request to Track’ Compliance Investigation
We tested 20 of the most popular ad-supported free VPN iOS apps in the U.S. and found that just 15% comply when you refuse permission for advertisers to track you.

Do Free VPN Apps Respect Ad Tracking Choices?
- 20 free VPN iPhone apps tested: we analyzed the most popular ad-supported free services in the U.S.
- Just 3 free VPNs (15%) respect your choice to not allow advertisers to track you
- 7 free VPNs (35%) fail to ask for consent to allow advertisers to track you
- 13 free VPNs (65%) share your real IP address with advertisers even after you refuse permission to do so
- 9 free VPNs (45%) share detailed information about your iPhone that could be used to uniquely identify you
- 15 free VPNs (75%) share basic info about your iPhone with advertisers
- Loophole: 16 free VPN apps (80%) already share your IP address before asking for you permission to allow ad tracking. 10 apps (50%) have shared detailed information about your iPhone by this point.
App Tracking Transparency in Free VPNs
Since April 2021, iOS apps have had to ask permission before tracking your activity across other apps and websites in order to deliver targeted advertising.[1]
This “Request to Track” should appear as a dialog box every time you install a new app containing ads on your iPhone or iPad, unless you have opted to universally block them in your privacy settings.
This new feature, dubbed “App Tracking Transparency”, is part of Apple’s ongoing public pivot to privacy. That strategy also included the launch of new App Store privacy labels,[2] which we found to be flawed in a recent VPN (Virtual Private Network) app investigation.
In light of those findings and Apple’s spotty record at enforcing its own privacy guidelines, we decided to investigate whether free VPN app developers actually comply with users’ wishes when they refuse to consent to ad tracking.
This issue is of particular importance for VPN users, given the privacy-focused nature of personal Virtual Private Networks.
As most free apps generally are supported by advertising, it’s in their developers’ interest for you to say yes to ad tracking. Targeted ads are more effective, which means more revenue for the developers.
In the screenshots below you can see how the hugely popular free VPN app Hotspot Shield tries to nudge you into allowing ad tracking in a splash screen that’s displayed immediately before the “Request to Track” dialog.
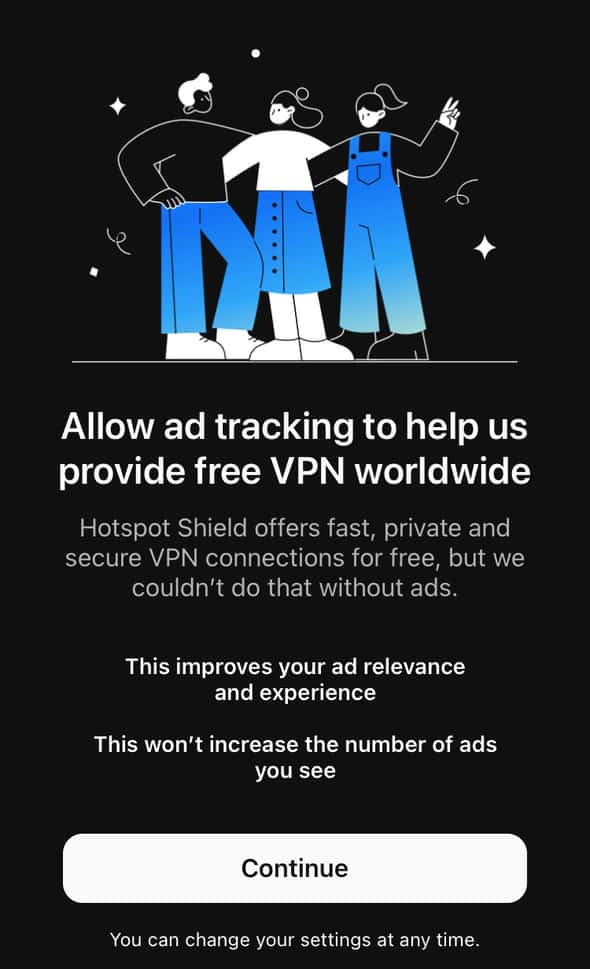
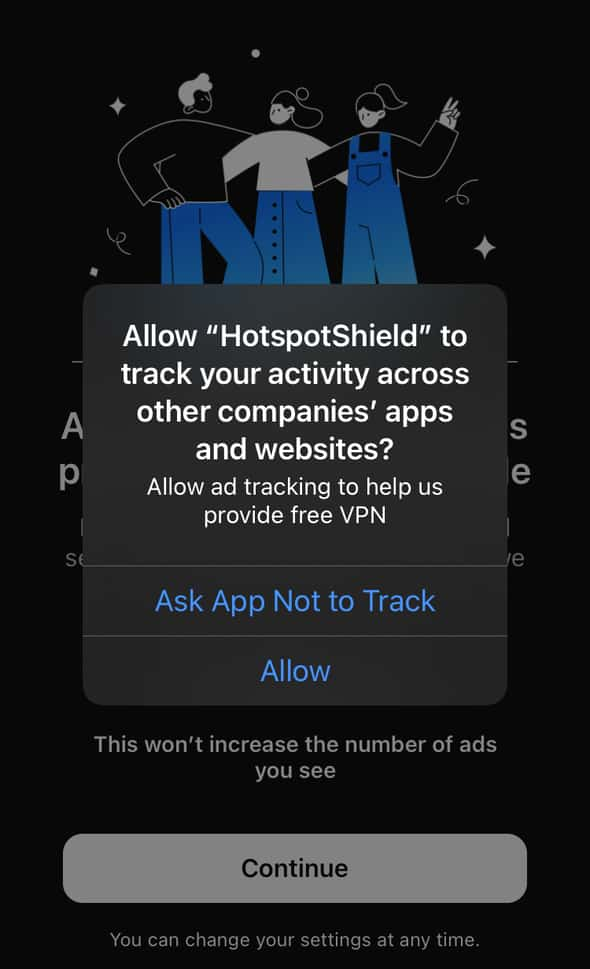
Note that Hotspot Shield was one of the tiny minority of free VPN apps (15%) that actually respected users’ refusal to permit ad tracking.
Unfortunately, we found that the majority of apps are so desperate for revenue that they continue to share tracking data with advertisers even when consent is denied.
In the course of our investigation we also discovered that over a third of free VPN apps ignore Apple’s supposedly mandatory guidelines and fail to seek consent at all.
We also found a loophole exploited by the 80% of the VPN apps we tested, whereby they shared tracking data with advertisers in the window between first launching the app and the Request to Track being made.
How did we test the VPN apps?
To conduct our research, we identified the 20 most popular ad-supported free VPN apps on the U.S. version of Apple’s App Store. In a controlled testing environment, we installed each app and monitored its network traffic as we launched it then connected and disconnected to various VPN servers.
After determining the point that we denied the Request to Track, we were able to identify any subsequent traffic to third-party advertisers that contained user data that could be used for tracking.
We found three types of user data:
- Real IP address
- Highly-detailed device information with the potential for fingerprinting
- Basic device information
The sharing of a VPN user’s real IP address with third-party advertisers is particularly problematic given the core functionality of a VPN involves hiding that information.
The highly-detailed device info comprised long lists of very specific data points, some of which included:
- Network operator
- Free memory
- Battery level
- Screen brightness
- Device volume
- Device name (ie Bob’s iPhone)
- Free storage space
- Last time device was switched on
- Screen height
- Network Connection Type (ie WiFi)
- Screen width
- iOS version
- Device model
- Language
As with browser fingerprinting, the collection of such granular information about your device can be used to identify and track you. Apple says fingerprinting is against its rules.[3]
We classed as “basic device information” any data sharing with advertisers that was limited to iPhone model, iOS version, screen height and width, language and country, along with some other general data points.
This basic information can’t strictly be used by advertisers to track you. However, we included it in our findings as in our view it should be made clear that this type of data will continue to be shared with advertisers even when you refuse to allow ad tracking.
Why did we do this research?
We’ve been campaigning to force Apple to pay more than lip service to its own guidelines as they relate to iOS VPN apps since 2018.
Free VPN apps are hugely popular, not only in the U.S. and Europe but also and especially in the global south and with people living in high-censorship regimes.
We want Apple to treat privacy as more than just a marketing gimmick that lulls iOS users into a false sense of security.[4]
The goal of this investigation is put pressure Apple to actually enforce its own app privacy guidelines and remove any apps from its store that are in breach.[3]
This would make it easier for anyone to choose a free VPN with peace of mind about their privacy.
Which Free VPNs Ignore Do Not Track Requests?
The following tables show the results of analyzing the network traffic from the 20 most popular free VPN apps in the U.S.
Ticks and crosses show whether the following data was found in server requests from the VPN app to third-party advertisers.
IP addressis the unique address for each device on a network. Note that a tick below means a user’s true IP address is shared rather than any IP address assigned by the VPNFingerprintingrefers to highly-detailed device information that is sufficiently granular to potentially uniquely identify a user.Basic Device Inforefers to much less detailed telemetry that is not likely to uniquely identify a user.
Monthly installs reflect September 2021 data.
After ‘Request to Track’ Declined: Apps 1-10
The following data is shared with third-party advertisers after the user has tapped the option to refuse permission to allow ad tracking.
After ‘Request to Track’ Declined: Apps 11-20
Before ‘Request to Track’ Declined: Apps 1-10
The following data is shared with third-party advertisers before the option to refuse permission has been offered to the user.
Before ‘Request to Track’ Declined: Apps 11-20
For list of apps with app store URLs and additional detail on findings, refer to the VPN iOS Do Not Track Compliance Data Sheet
VPN Developer Response
We spoke with Aura, developer of Hotspot Shield, Betternet and VPN 360, prior to publication and made them aware of our findings.
In a very positive response, Aura confirmed they are working on changes that would not only lead to better compliance for VPN 360, but would also limit any potential tracking data being shared before the Request to Track is first made across all three apps.
These changes are expected to be included in the apps’ next update.
Which Advertisers Received User Data?
- Aarki
- AdColony
- Adnexus
- Casale Media
- Chartboost
- Google (DoubleClick)
- Flurry
- GumGum
- Mopub
- presage.io
- Revenuecat
- Smadex.com
- Stack Adapt
- Supersonic Ads
- Tapjoy Ads
- Unity
- Yandex
By far the biggest recipient of user date was Google via its DoubleClick platform. All but two of the apps shared user data with Google either before or after the “Request to Track” was made.
Most of the other entities in the above list are ad exchanges, ie platforms that facilitate the trade of vast amounts of digital ad inventory and offer powerful tools that exploit the user data harvested by apps, such as those in this report, in order to better target their ads.
Note that while Flurry is well-known for its mobile analytics service, it also offers app monetization tools.
Methodology
We identified the 20 most popular ad-supported free services in the U.S. version of the iOS App Store based on the most recent install data available from SensorTower.
We captured and analyzed internet traffic to and from each app using the mitmproxy tool. After identifying the point at which permission to track was denied for each app, we were able to determine what information was subsequently shared with third-party advertisers. We also identified all information shared before that point.
Our test device was running the most up-to-date version of iOS at the time of publication.
The authors of all our investigations abide by the journalists’ code of conduct.
References
[1] https://developer.apple.com/documentation/apptrackingtransparency ↩
[2] https://developer.apple.com/app-store/app-privacy-details/ ↩
[3] https://developer.apple.com/app-store/user-privacy-and-data-use/ ↩
[4] https://www.apple.com/uk/newsroom/2021/01/data-privacy-day-at-apple-improving-transparency-and-empowering-users/ ↩