To understand if a VPN can be hacked, you first need to understand exactly how a VPN works.
Here’s a brief summary of what happens when you use a VPN:
- You download VPN software to your device, connect to a VPN server, and request a website.
- The VPN software uses a connection protocol to safely connect your device to the server, and an encryption cipher to encrypt the data traveling to it.
- When your data reaches the VPN server, it is decrypted and the server connects to the website on your behalf.
- The website sends the requested information back to the VPN server, where it is encrypted and forwarded back to your device.
- The VPN client decrypts the information and the website appears in your browser.
To hack your VPN connection, a hacker would have to compromise your data at some point during this process. This might involve attempting to decrypt the data using a brute force attack, capturing data sent outside the VPN tunnel, or compromising the VPN server itself.
Here’s a more detailed list of how a VPN can be hacked:
1. Through Vulnerabilities In VPN Protocols
VPN protocols describe the rules that your VPN uses to create a secure connection between your device and the VPN server. The most common protocols in consumer VPN services include OpenVPN, WireGuard, and IPsec.
Some VPN services let you choose a preferred protocol, while others don’t let you choose at all. Each protocol has its own strengths and weaknesses, and some are much more secure than others.
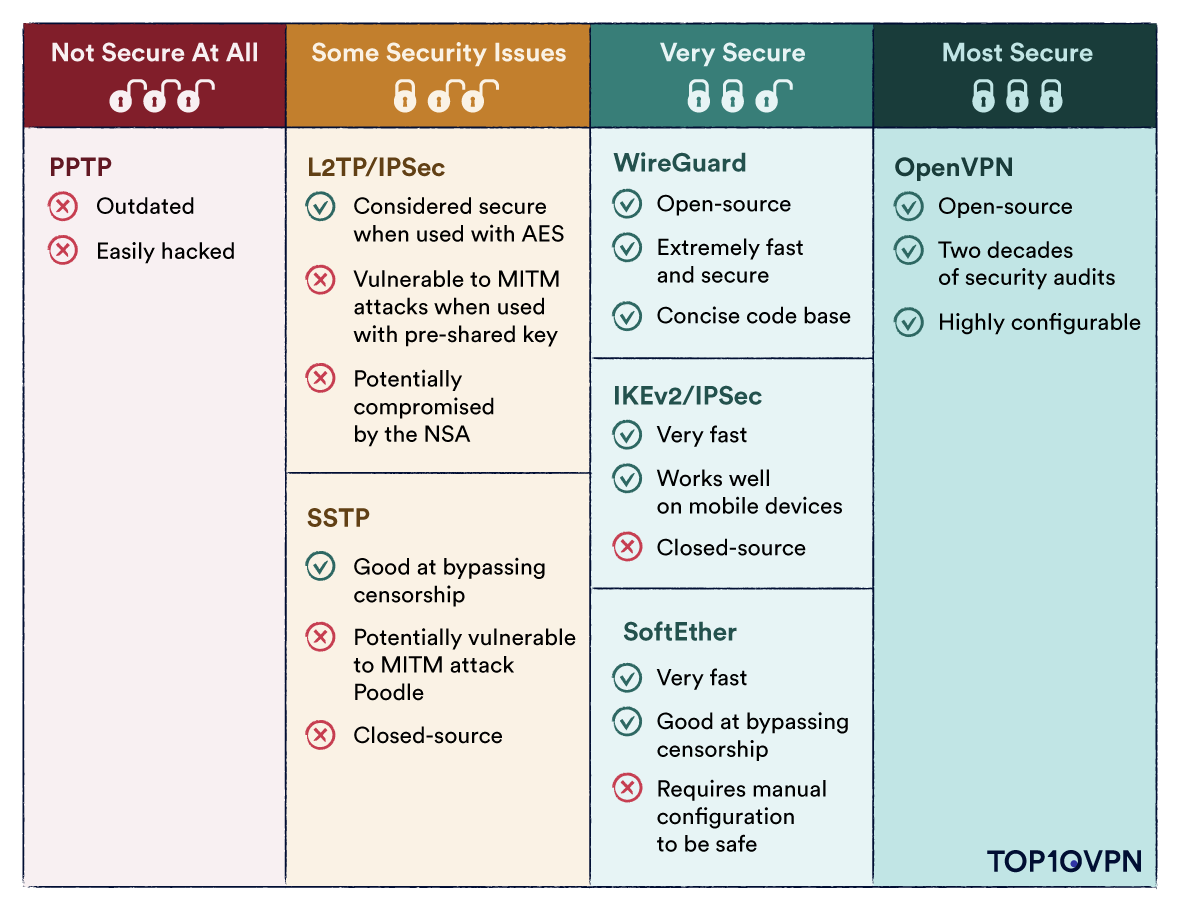
If there is a vulnerability in the underlying protocol you’re using, your VPN connection can be hacked. This could happen as a result of design flaws if the protocol is newly developed, or simply because the VPN client hasn’t been configured properly.
For example, the PPTP protocol is no longer considered secure due to reports that the NSA cracked a PPTP VPN connection to spy on a target. Despite being outdated, it is still included as an option by some VPN services.
2. Through Cryptographic Attacks
To convert your web traffic into an unintelligible code, VPNs need to use an encryption cipher. This simply refers to the algorithm used to encrypt and decrypt your data. This is used in combination with a hash authentication, which further secures your connection.
The most common ciphers used in VPN services are AES, ChaCha20, and Blowfish – though the latter is fairly rare.
Ciphers are usually paired with a key-length, which describes the number of digits in the encryption key. At its simplest, longer key lengths are usually more secure. For example, AES-256 is considered more secure than AES-128.
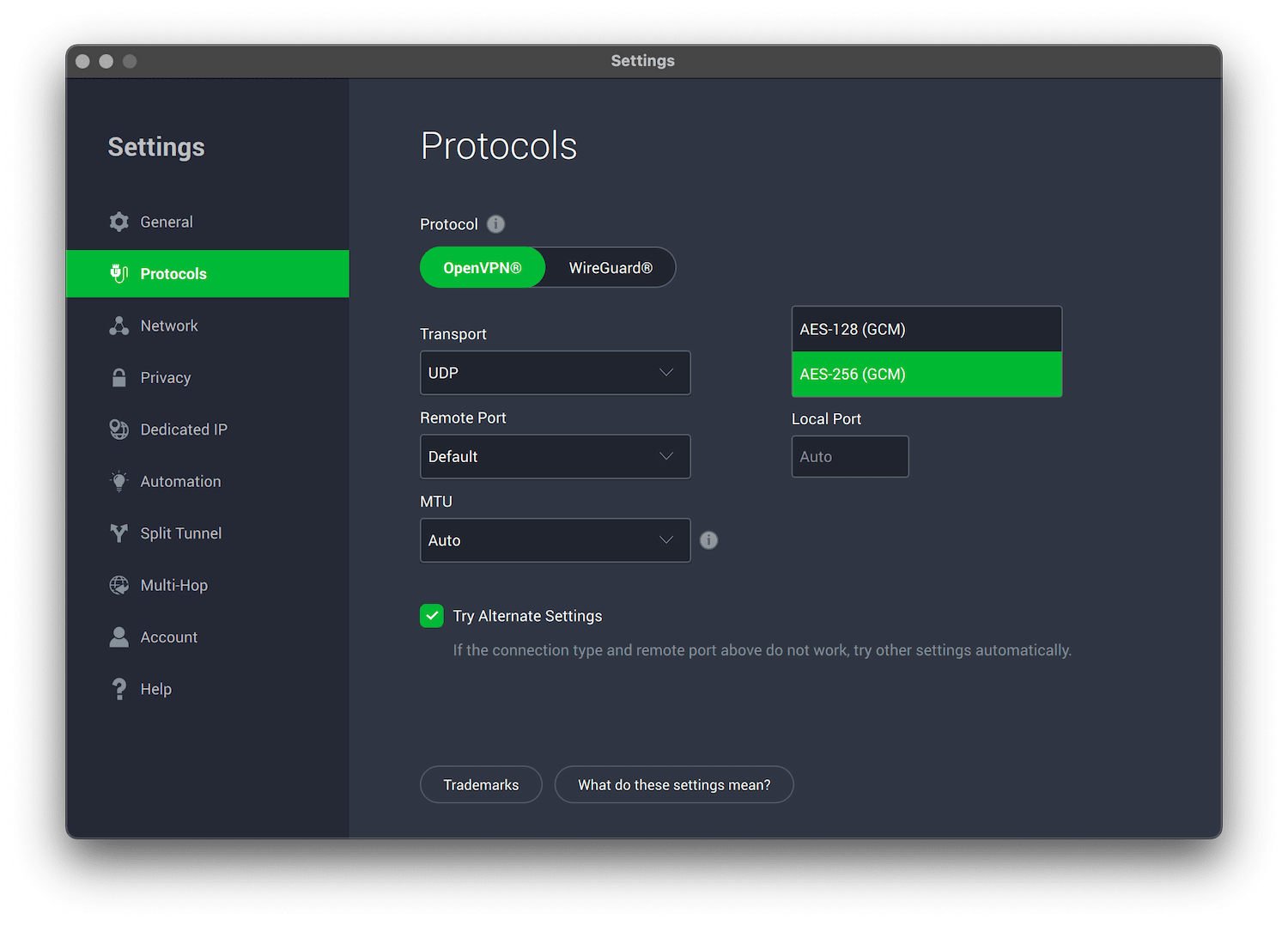
A VPN should not use anything less than the AES-128 cipher to encrypt your data.
Due to advancements in computing, older hash functions and encryption ciphers can be broken in a shorter amount of time, making it possible to hack a VPN connection if it uses an outdated cipher.
For example, the SHA-1 hash function is cryptographically broken, and the Blowfish cipher is susceptible to ‘birthday attacks’. These cryptographic functions are still used by some low-quality VPNs.
A VPN should not use anything less than the AES-128 cipher to encrypt your data, though AES-256 is even more secure. ChaCha20 is a secure alternative for WireGuard users that also uses 256 bits, which means it’s equally as secure as AES-256 encryption.
3. Through IP, DNS, or WebRTC leaks
Although it doesn’t technically involve ‘breaking’ your VPN connection, a hacker could compromise your identity or activity by monitoring for data leaking outside the encrypted VPN tunnel. This is known as a ‘VPN leak’.
For example, your real IP address can be exposed if your VPN does not encrypt any IPv6 requests made by your browser, or if it doesn’t re-route WebRTC connections. Similarly, your browsing activity can be exposed if your DNS requests are handled by your ISP rather than the VPN service, or if the VPN kill switch isn’t working.
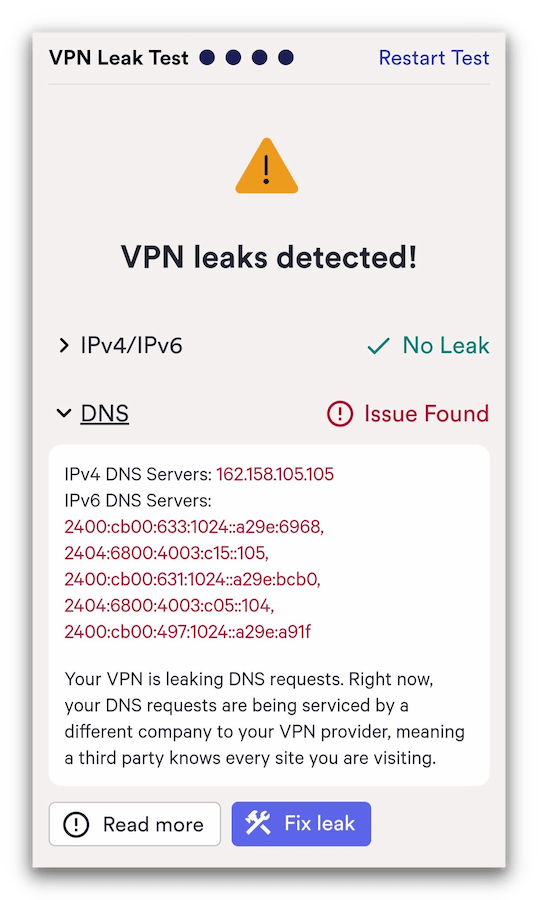
Our leak test tool checks whether your VPN is properly hiding your real IP address and DNS requests.
Most top-rated VPN services now include leak protection by default, which should keep you safe on most connections. You can also use our dedicated tool to check if your VPN is leaking.
4. By Compromising a VPN Server
If an attacker can’t compromise your VPN connection directly, they may be able to target the VPN service itself.
It’s possible for VPN servers to be misconfigured or set with weak login credentials, which makes them an easy target for hackers. If an attacker gains entry to the server, they can potentially access your personal information, browsing history, and future activity when connected to the server.
For example, one of NordVPN’s servers was breached In March 2018 due to a third-party error. This allowed hackers to see which users were connected to the breached server, as well as the websites they were visiting.
In March 2021, SuperVPN, GeckoVPN, and ChatVPN were also hacked. As a result, the names, email addresses, location, and payment information of 21 million users were made public.
The risk of your VPN server being compromised is significantly reduced if you choose a premium VPN service with a history of third-party security audits. For even more reassurance, use a VPN with RAM-only servers to prevent your data ever being written to the hard drive.
5. By Stealing Encryption Keys
If hackers obtain the encryption keys used to secure your data, they can hack your VPN connection and read all of the incoming and outgoing traffic.
Fortunately, most VPN software encapsulates its encryption keys, and most top-tier VPNs use Perfect Forward Secrecy (PFS) by default.
PFS is a protocol feature which ensures your VPN server and client use unique symmetric keys for every VPN session. Both sides generate the key independently, and the key is never exchanged across the connection. A new key is automatically issued for each session, making the previous key obsolete.
In short, Perfect Forward Secrecy removes the threat of a single encryption key that would expose all of your VPN sessions if compromised. Instead, the temporary keys ensure that a hacker could only ever expose one specific session, and nothing more.
EXPERT ADVICE: If you’re using a VPN headquartered in a Five Eyes jurisdiction, government agencies may access your identity and activity even without hacking your VPN. Some countries can legally force VPN companies to log and share your data, getting the information they need without compromising your connection.