SUMMARY: VPNs use encryption ciphers and protocols to convert your web traffic into unreadable code, protecting your browsing activity from third-party surveillance. A secure VPN shouldn’t use anything weaker than the AES-256 or ChaCha20 cipher to encrypt your data.
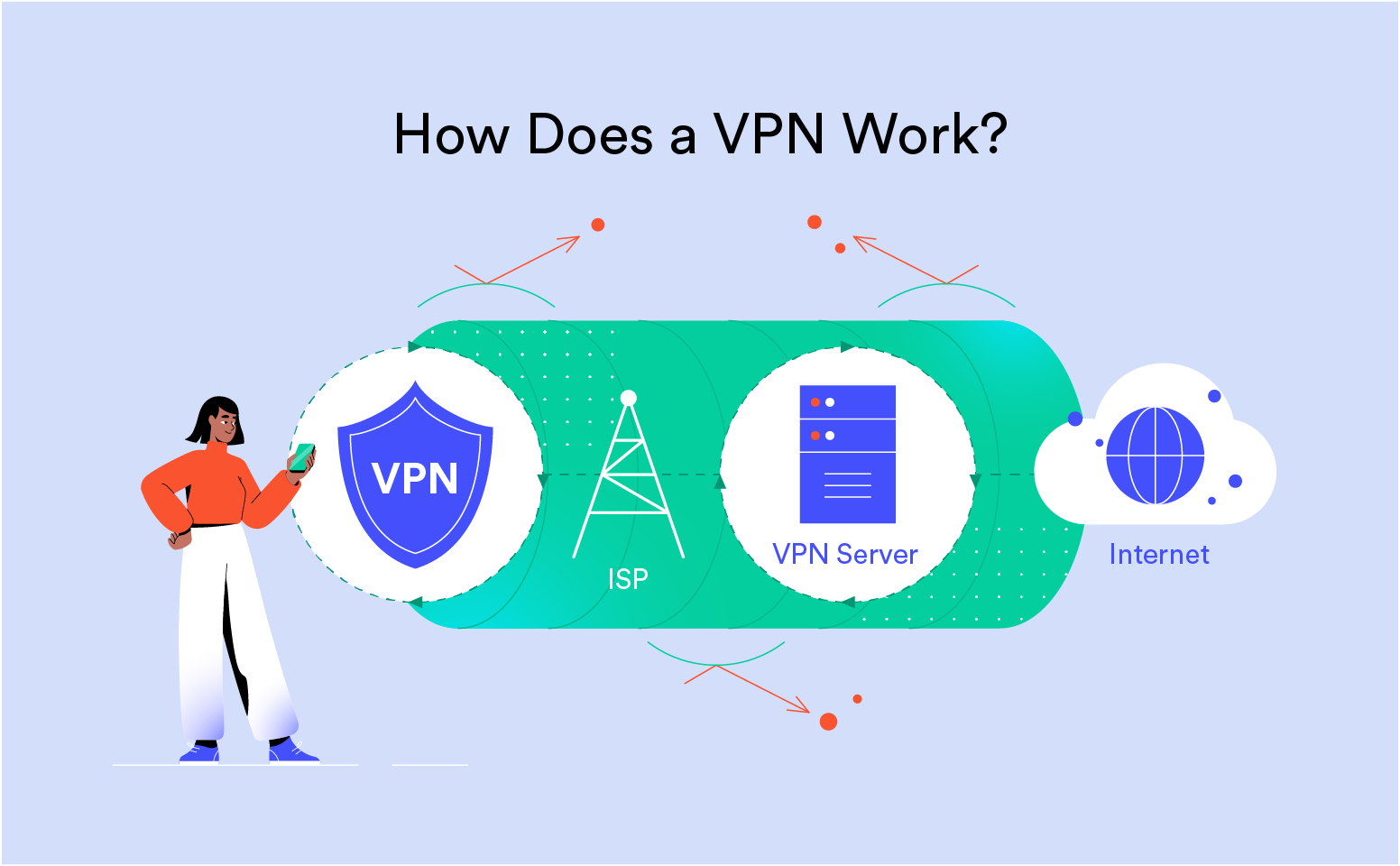
What is a VPN Tunnel?
A VPN tunnel is simply a secure channel established between your device and the VPN server, creating a safe, private route through the public internet.
It’s referred to as a tunnel because your original traffic is encrypted and wrapped in a layer of unencrypted traffic.
Think of it as placing a sealed envelope inside another envelope with a different address, concealing your original message and making it unreadable by anyone who might intercept it.
This process, called encapsulation, is performed by tunneling protocols.
VPN Encryption Ciphers
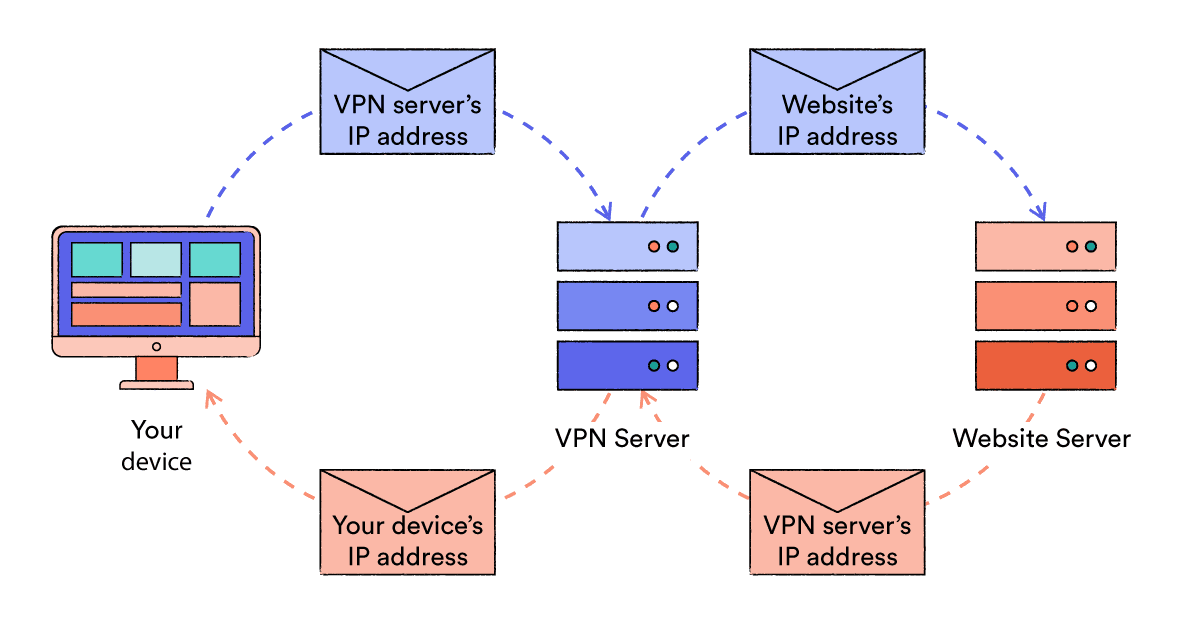
Encryption transforms plaintext data into a secret code, making it unreadable to anyone without the necessary key to decrypt it.
VPNs use encryption to hide your browsing activity between your device and the VPN server, protecting you from various forms of surveillance.
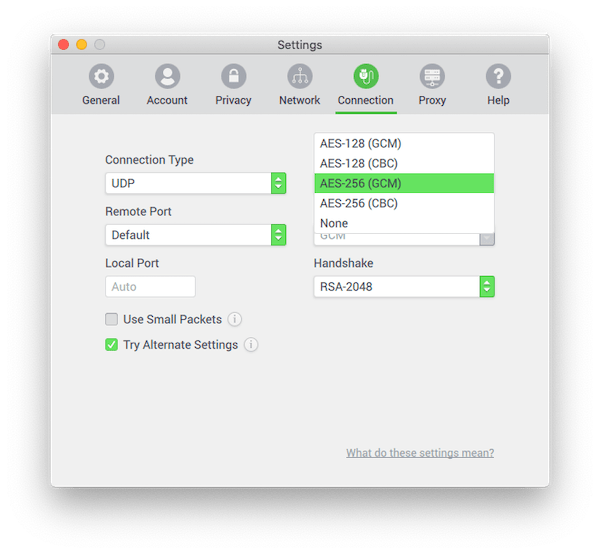
VPNs use encryption ciphers to convert your online activity into unreadable code. A cipher is a mathematical algorithm (i.e. a set of rules) that encrypts and decrypts data, often paired with a specific key length.
The key is a string of characters that is used to alter the data being encrypted. Only someone in possession of the same key is able to decrypt the data.
Longer key lengths generally offer more security. For example, AES-256 is considered more secure than AES-128.
Some VPN protocols use static keys, designed for long-term use, while others use ephemeral keys that expire after a single session or transaction.
Here’s how encryption ciphers work:
- The cipher uses a key to encrypt the data before sending it.
- The same or a related key is used to decrypt the data at the receiving end.
- Only those with the correct key can decrypt and read the information.
The cipher used by a VPN is often determined by the degree to which its developers prioritized security over performance, as stronger ciphers tend to require more processing power.
Newer ciphers also emerge over time and are incorporated by higher quality services.
The most commonly used ciphers in VPN services are:
- Advanced Encryption Standard (AES)
- Gold standard for online encryption
- Available in 128-bit and 256-bit key-lengths
- AES-256 preferred for stronger protection
- Considered quantum-resistant
- Blowfish
- Designed in 1993, largely replaced by AES-256
- 128-bit key length (32 to 448 bits possible)
- Has known weaknesses
- Used as fallback to AES-256
- ChaCha20
- Newer cipher gaining popularity
- 256-bit key length
- Comparable security to AES-256
- Faster performance, especially on mobile devices
- Camellia
- Developed in 2000
- Security and speed comparable to AES
- Not certified by NIST
- Limited availability in VPN services
Encryption modes determine how ciphers like AES encrypt data. They’re crucial for VPN security, affecting both privacy and performance. Here are the most common modes used in VPNs:
- CBC (Cipher Block Chaining)
- Traditional mode
- Creates chain of dependent blocks
- Can be slower than newer modes
- Requires additional security measures
- GCM (Galois/Counter Mode)
- Provides encryption and authentication
- Faster than CBC
- Considered very secure
- Widely used in modern VPNs
- CTR (Counter)
- Turns block cipher into stream cipher
- Fast and allows parallel processing
- Doesn’t provide authentication alone
- Used by ChaCha20
- OCB (Offset Codebook Mode)
- Provides authenticated encryption in single pass
- Very efficient
- Limited adoption due to patent concerns
Other modes are best avoided in VPNs. ECB (Electronic Codebook) in particular is too simple to be secure, while CFB (Cipher Feedback) and OFB are both prone to misconfiguration due to their complexity as well as being considered outdated. Any mode without integrity checks should also be avoided unless paired with a separate authentication mechanism.
Most top-tier VPNs now use GCM mode with AES or the ChaCha20-Poly1305 combination, as these provide a good balance of security and performance. When reviewing VPNs, we look for these modern, authenticated encryption modes.
VPN Protocols
VPN protocols are the sets of rules and processes used to establish secure connections between your device and the VPN server.
They determine how the VPN tunnel is formed and managed, while encryption ciphers secure the data within the tunnel.
Each protocol offers a unique balance of speed, security and compatibility. Most VPN services will default to a particular protocol but allow you to change it in the app settings.
Common VPN protocols:
- OpenVPN: Open-source, highly secure, widely compatible and highly configurable.
- WireGuard: Very fast and efficient. Relatively new but gaining rapid adoption.
- IKEv2/IPsec: Good for mobile thanks to fast reconnection, but closed-source and potentially compromised.
- SoftEther: Fast, secure, bypasses censorship, but not well supported.
- L2TP/IPsec: Slower, also potentially compromised.
- SSTP: Good with firewalls, but closed-source and potentially vulnerable.
- PPTP: Outdated and insecure, avoid.
For a detailed comparison of VPN protocols, see our VPN protocols guide.
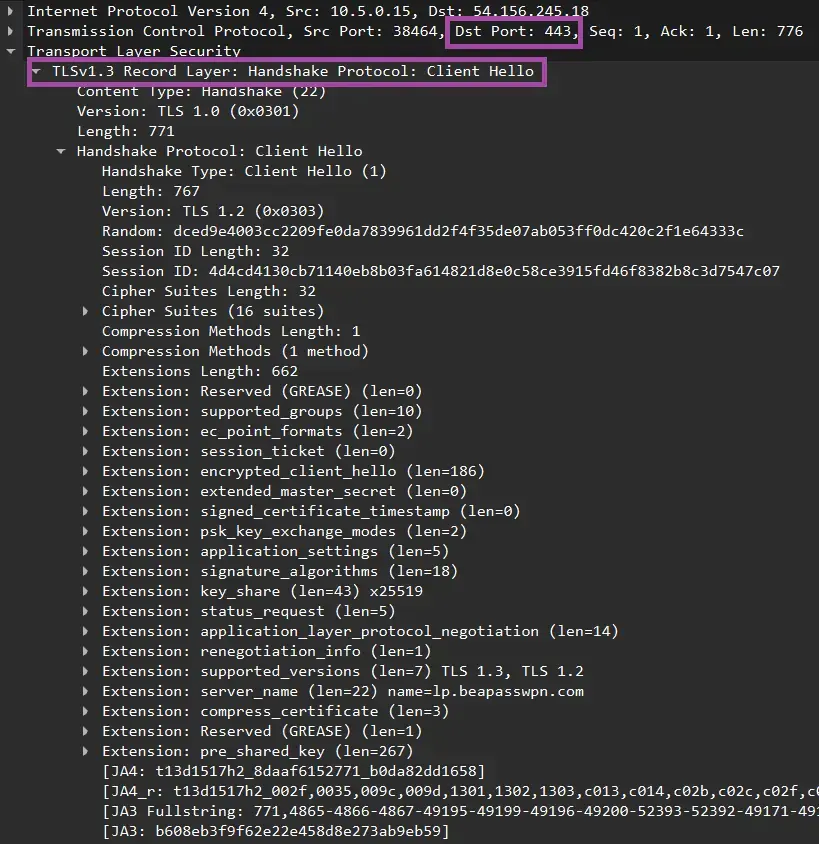
VPN Handshakes
VPN handshakes are crucial for initiating secure connections. This process involves:
- Authentication: Verifying the identity of both the VPN client and server.
- Key Exchange: Securely sharing encryption keys for the session.
- Parameter Negotiation: Agreeing on communication rules and cipher suites.
During a VPN handshake, your device and the VPN server exchange information to establish a secure channel. This exchange results in a shared secret key used for encrypting and decrypting data throughout the VPN session.
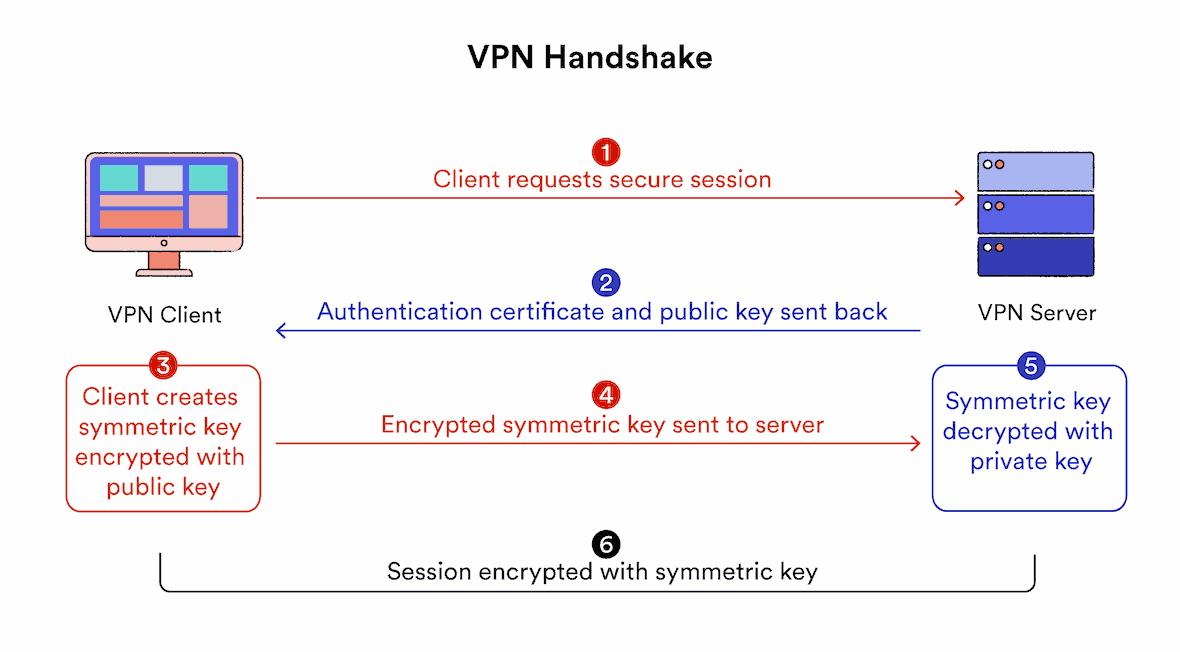
VPN handshakes typically use the RSA (Rivest-Shamir-Adleman) algorithm. RSA has been the basis for internet security for the last two decades. However, key length is critical.
For adequate security, use VPN services implementing RSA-2048 or RSA-4096. RSA-1024 is no longer considered secure due to advances in computing power.
While broadly secure, the handshake process generates a ‘master key’ that could potentially decrypt all sessions on that server if compromised.
In such a scenario, an attacker could hack into the VPN server and gain access to all data flowing through the VPN tunnel.
To mitigate this risk, we recommend using VPN services with Perfect Forward Secrecy.
Perfect Forward Secrecy
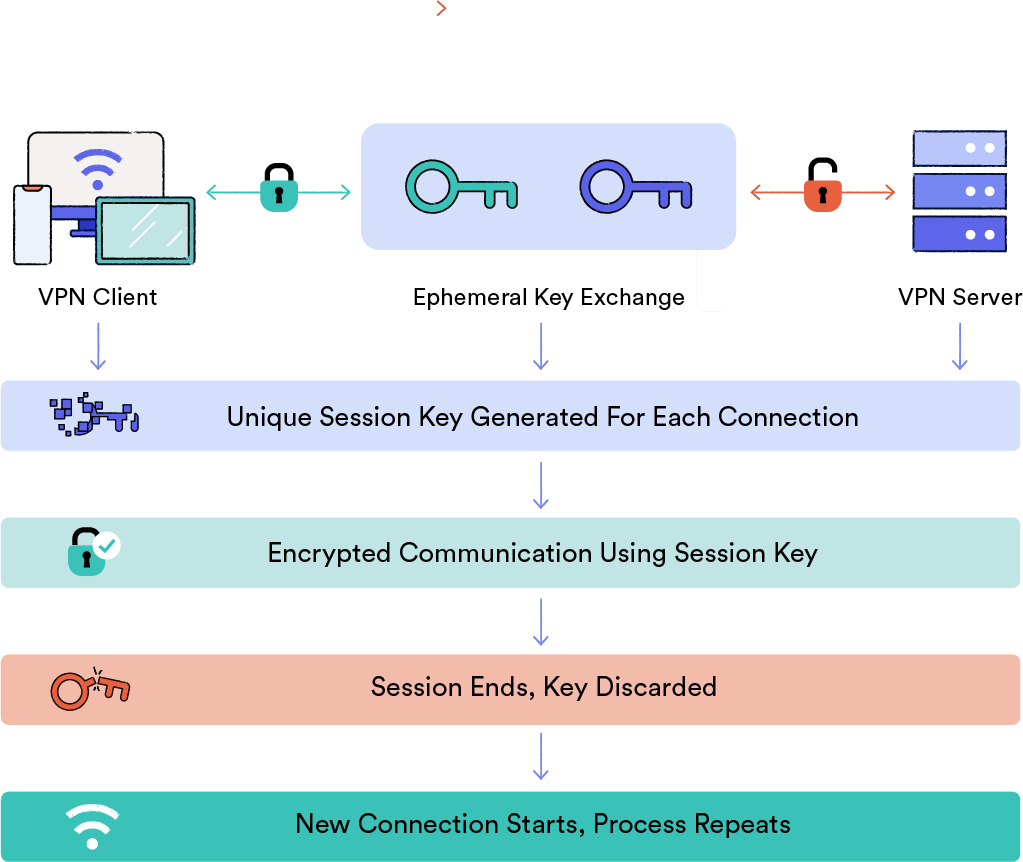
Diagram explaining how Perfect Forward Secrecy works.
Perfect Forward Secrecy (PFS) is a critical security feature in modern VPN protocols. It uses Diffie-Hellman (DH) or Elliptic Curve Diffie-Hellman (ECDH) algorithms to generate unique temporary session keys.
Perfect Forward Secrecy ensures encryption keys are never exchanged across the connection.
Key benefits of PFS include:
- Independent key generation: Both the VPN server and client independently derive the same encryption key without exchanging it.
- Session isolation: Each connection uses a unique key, limiting the potential damage from a single compromised session.
- Temporal security: Keys are temporary and discarded after use, preventing future decryption of any captured data.
While RSA is crucial for authentication, it cannot provide PFS on its own. Implementing PFS requires the inclusion of DH or ECDH in the cipher suite. ECDH offers robust security for handshakes, while DH should only be used together with other measures due to potential vulnerabilities otherwise.
OpenVPN and WireGuard, our recommended VPN protocols, both support Perfect Forward Secrecy.
Hash Authentication
Secure Hash Algorithms (SHA) play a vital role in VPN security by:
- Verifying data integrity during transmission
- Authenticating client-server connections
- Preventing unauthorized data manipulation
SHAs use a hash function to convert source data into a fixed-length string of characters, known as the “hash value”. This is a one-way process and can’t be reversed; changing even one character in the input drastically alters the output.
This is how it works in VPN communications:
- The sender applies an agreed-upon hash function to the data.
- The recipient generates a hash from the received data using the same function.
- If the generated hash matches the transmitted hash, the data’s integrity is confirmed.
- Mismatched hashes indicate potential tampering, and the data is discarded.
SHA hash authentication prevents man-in-the-middle attacks by detecting certificate tampering, which stops hackers from impersonating legitimate VPN servers.
For maximum security, we recommend VPN services using SHA-2 or higher. SHA-1 has known weaknesses that can compromise security.