Internet Shutdowns & Free VPNs: Are The Most Popular Apps Safe?
Demand for VPN services surges whenever governments disrupt access to social media and other critical online services. This report tracks the VPNs that rise to popularity during these incidents and tests them for privacy and security issues.

Originally published June 17 2021. Most recently updated with Kazakhstan VPN analysis.
- Tested: 5 most popular VPN mobile apps in Kazakhstan installed before January internet shutdown
- IP address exposure: all 5 VPNs share or log a user’s true IP address. Two apps share VPN IP and true IP addresses at the same time.
- Leaks: one VPN exposes users’ browsing activity via DNS leaks
- Fingerprinting devices: 2 VPNs collect unique device identifying information, such as IMEI numbers.
- Email address exposure: one VPN shares users’ Google emails if they are logged into Chrome.
- Personal data-sharing with third parties: All VPNs shared personal info with Facebook and Google, along with other marketing platforms.
- Tested: 10 most popular VPN mobile apps in Myanmar since military coup resulted in rolling internet disruptions
- IP address exposure: 8 VPNs share or log a user’s true IP address
- Leaks: 3 VPNs expose users’ browsing activity via DNS and/or IP leaks
- Ad tracking: 7 VPNs share your unique Google Advertiser ID with third parties
- Device information: 4 VPNs share detailed information about users’ devices. A further 3 VPNs share basic device info.
- Tested: 5 most popular VPN mobile apps in Nigeria since the government banned Twitter
- IP address exposure: 4 VPNs share or log a user’s true IP address
- Ad tracking: 4 VPNs share your unique Google Advertiser ID with third parties
- Device information: 2 VPNs share detailed information about users’ devices. A further 2 VPNs share basic device info.
Kazakhstan VPNs
Myanmar VPNs
Nigeria VPNs
VPN Demand During Internet Shutdowns
Whenever governments around the world restrict access to social media and other online sources of information, demand for VPN services typically skyrockets as those affected scramble to circumvent the shutdown.
Internet shutdowns have cost the world over $25 billion since 2019 alone and continue to be popular with regimes looking to restrict the flow of information.
A VPN service, or Virtual Private Network, is a simple anti-censorship software tool. It encrypts users’ traffic and masks their IP address, hiding their identity and activity from internet censors.
Intentional internet shutdowns disproportionately affect the global south and although many VPN services are inexpensive, the resulting increase in demand naturally tends to be focused on free VPN Android apps.
Our research has previously highlighted the dangers of free VPNs. By monitoring these apps, we hope to ensure that those in need can access vital information without compromising their privacy, security, or even physical safety.
After identifying the most downloaded VPN Android apps during a particular incident, we run the following tests:
- Traffic analysis to determine what personal data is being logged or shared by the apps
- Leak testing to identify whether apps expose users’ activity via DNS or IP leaks
- Code analysis to determine whether any high-risk permissions have associated functionality that could impact user privacy
The results are compiled below by country. The number of VPNs tested varies according to the severity and extent of the internet shutdown.
What VPN Privacy Issues Did We Find?
We found the following types of user data being shared to third-party servers:
- Real IP address: can be used to track down and identify individuals based on their internet activity. Sharing it with third parties is especially problematic during censorship events.
- Google Advertising ID: this unique ID is often shared by free VPN apps with advertisers in order to track VPN users’ online activity to better target ads. As with sharing IP addresses, this takes on heightened privacy risk during internet shutdowns.
- Device information: Details ranging from operator, make and model to current battery level and storage space remaining are shared with third parties, such as advertisers and monetizing services.
We also found DNS and IP leaks, which pose a huge risk to the safety of VPN users during a shutdown. These fundamental failings expose users’ online activity, leaving them open to persecution from the authorities imposing the restrictions.
During our code analysis we most frequently found combinations of the WRITE_EXTERNAL_STORAGE permission and third-party advertising code that creates files on VPN users’ devices to assist in tracking ad performance.
Why Does It Matter?
Internet shutdowns already trample on the digital rights of those affected. It feels especially egregious when the victims of repression are exploited and put at risk by the very services purporting to help them.
By logging or sharing any identifying information at all, VPN services put their users at risk of exposure should the authorities decide to pursue those evading censorship.
The best VPN services won’t collect or share any personal user information at all, which leaves no opportunity for authorities to attempt to seize such data to persecute dissidents.
We will be updating and adding to this page regularly as major internet shutdowns take place around the world.
See all our investigations into the dangers of free VPN services.
Kazakhstan
The following table shows the results of our privacy and security tests of the 5 most popular VPN mobile apps in Kazakhstan on January 5 2022, before the government imposed a full internet blackout. They are ordered by popularity, ie by the number of local installs on that day.
Note that Clean Master Pro and Smart Clean are multi-purpose apps offering VPN services as well as data cleaning and device performance boosts.
For a full list of Play Store URLs, including archived versions, see this References document.
Analysis
VPN demand in Kazakhstan surged on January 5 in anticipation of the authorities potentially shutting down social media in response to escalating anti-government protests. The authorities had already severely disrupted mobile internet access by that point but instead of then targeting social media or individual websites for censorship, the Kazakh government instead completely shut down the internet. The blackout lasted until January 10, with only intermittent and brief periods of limited internet access.
Of course, the free VPN mobile apps that Kazakhs installed in huge numbers before the internet outage were not ultimately of any use in the face of a total internet blackout. However, it’s likely that Kazakhs will retain these apps and use them to keep their internet activity private from the authorities and to circumvent any censorship that may be looming as the government looks to regain its grip on power.
So it’s concerning to see every VPN app we tested shared users’ real IP addresses with Google. Two apps, Daily VPN and VPN Master Pro, also broadcast a user’s VPN IP address and their true IP address in the same server request to Google’s advertising platform, putting their users at potential risk of exposure in the process.
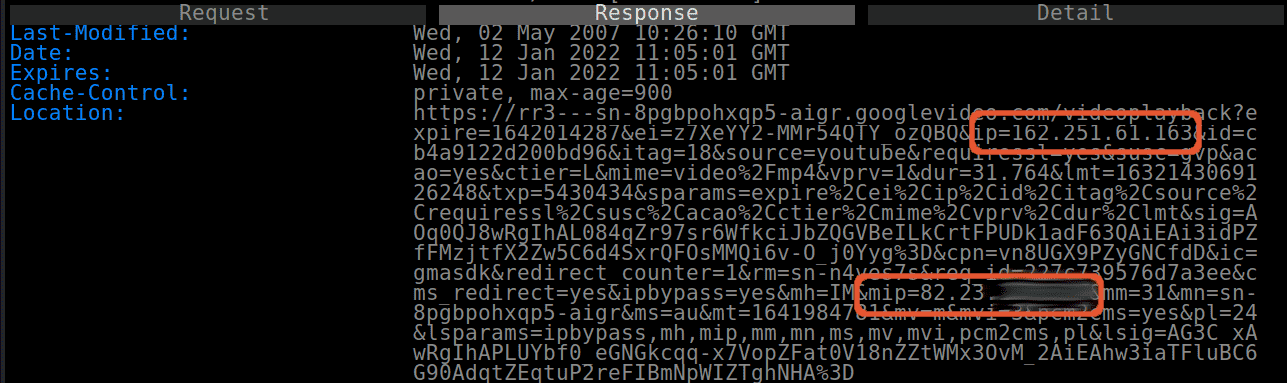
Mitmproxy screengrab showing VPN Master Pro sharing VPN and true IP addresses in same server request.
Our tests of Daily VPN also revealed that it leaks DNS requests, which means that Kazakhs using this VPN service are at risk of having their internet activity traced back to them during a time where 164 people have been reported killed and thousands arrested by authorities cracking down on dissent.
We also found that users of VPN Master Pro who were also logged into their Google account while connected to the VPN and using the Chrome browser would have their Google email address shared with Google along with other data about their supposedly private session.
Two other apps we analysed, RavoVPN and Smart Clean, contained code that fingerprints users’ devices by collecting extensive identifying data about that device. This includes data we would never want to see logged, such as the unique IMEI and IMSI numbers associated with that device.
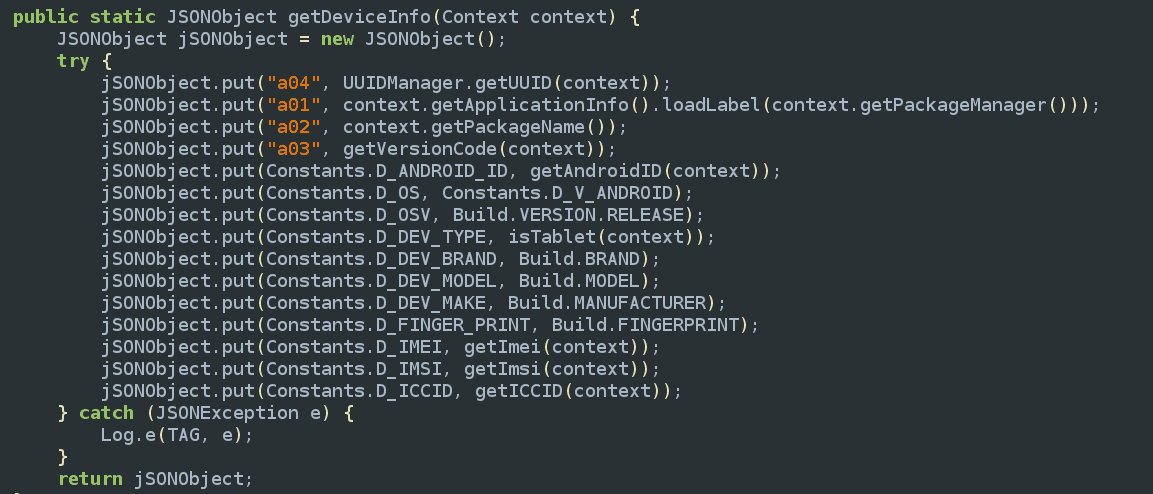
Screenshot of Smart Clean Android app code showing types of data collected.
We also found that DailyVPN contained code and the related permission to use both front and rear-facing cameras, flash and autofocus. This appears to be related to QR code/barcode scanner functionality included in the code but not advertised anywhere in the app’s user interface or web. While it’s not clear that this is explicitly malicious, it’s certainly a red flag in terms of trustworthiness.
All apps we tested shared personal data with Facebook and Google’s advertising platforms, along with other third parties, such as app marketing data services Adjust and Tenjin, and analytics platforms Firebase and Kochava.
Myanmar
The following table shows the results of our privacy and security tests of the 10 most popular VPN apps in Myanmar since the February 2021 coup. They are ordered by popularity, which is based on the number of days spent in the top 10 most-installed VPN apps in Myanmar.
For a full list of Play Store URLs, including archived versions, see this References document.
Analysis
Internet disruptions in Myanmar since the February coup have been severe and extremely drawn-out. Burmese people turned to VPNs in huge numbers, resulting in many free VPNs enjoying surges in popularity of varying duration.
Disturbingly, given the violence in the country, just two apps did not share or log users’ IP addresses. One app, VPN Super, actually broadcasts a user’s VPN server IP address and their true IP address in the same request back to its own servers.
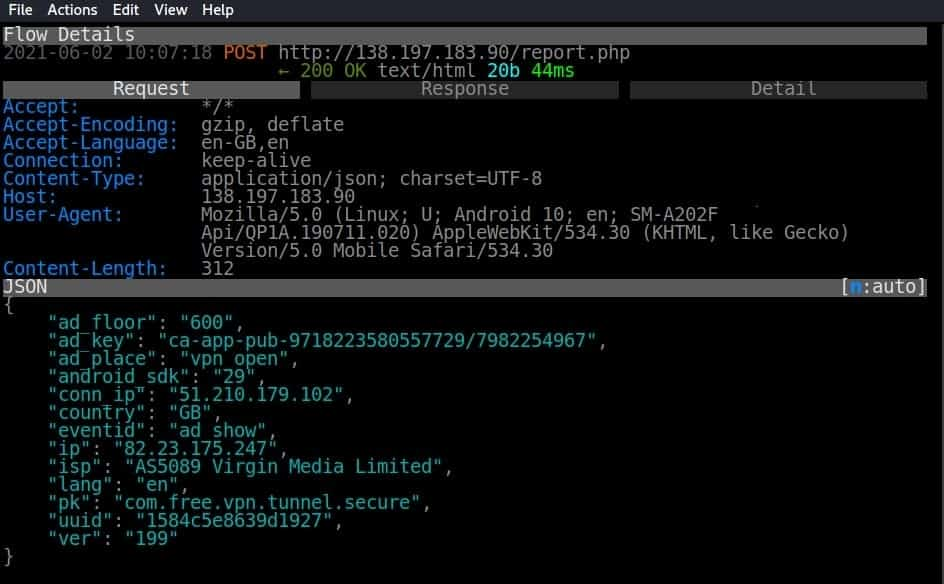
Mitmproxy screengrab showing VPN Super server request containing both VPN server and true IP addresses.
Most apps shared users’ true IP addresses with Google’s various advertising services, however VPN Super also shared this sensitive data with Facebook.
Cloudflare’s 1.1.1.1 / Warp VPN service sent the user IP address to its own servers only, where the data is stored temporarily before being purged, according to its privacy policy.
Even hugely popular apps like TurboVPN and Psiphon, which have over 150M installs between them worldwide, share personal data with third parties, such as app monetization services Vungle or Chartboost, and advertising platforms like Google, Unity and Freestar.
Other third parties that receive data from the VPNs we tested included marketing data service Adjust, customer messaging service OneSignal and analytics platforms Firebase and Criteo.
In terms of risky functions, our findings were largely related to the creation and storage of files on user devices as a result of third-party advertising code, as mentioned earlier in this report. However we did also find that LetsVPN included both the BLUETOOTH permission and code to listen for Bluetooth networks, which is not something we would expect or want to see in a VPN app.
Nigeria
The following table shows the results of our privacy and security tests for the five most popular VPN apps in Nigeria since the government banned Twitter in June 2021. They are ordered by popularity, which is based on the number of days spent in the top five most-installed apps in Nigeria during the ban.
We limited our analysis to five apps as the Twitter ban remains in its early days. Also the there has not been significant fluctuation in which VPN apps are most popular during this period.
For a full list of Play Store URLs, including archived versions, see this References document.
Analysis
The Nigerian government banned Twitter on 5 June 2021 and demand for VPN services immediately spiked by over 1,400%. The social media platform remains blocked and the government has threatened to prosecute anyone who uses a VPN to access it.
This threat of criminal charges makes it doubly important that Nigerians can trust their VPN service not to expose their internet activity.
Encouragingly, Windscribe has been the most popular VPN during the shutdown, which is arguably the best free VPN service available.
Unfortunately, many Nigerians are installing less private VPN apps to get around the Twitter ban and are therefore putting themselves at risk.
Three VPN apps share their users’ true IP address with third parties. Notably, one app SuperNet VPN shares this data with Bugly, an operation stats tracking service owned by Chinese mega-corporation Tencent. The other two shared user IP addresses with Google ad services.
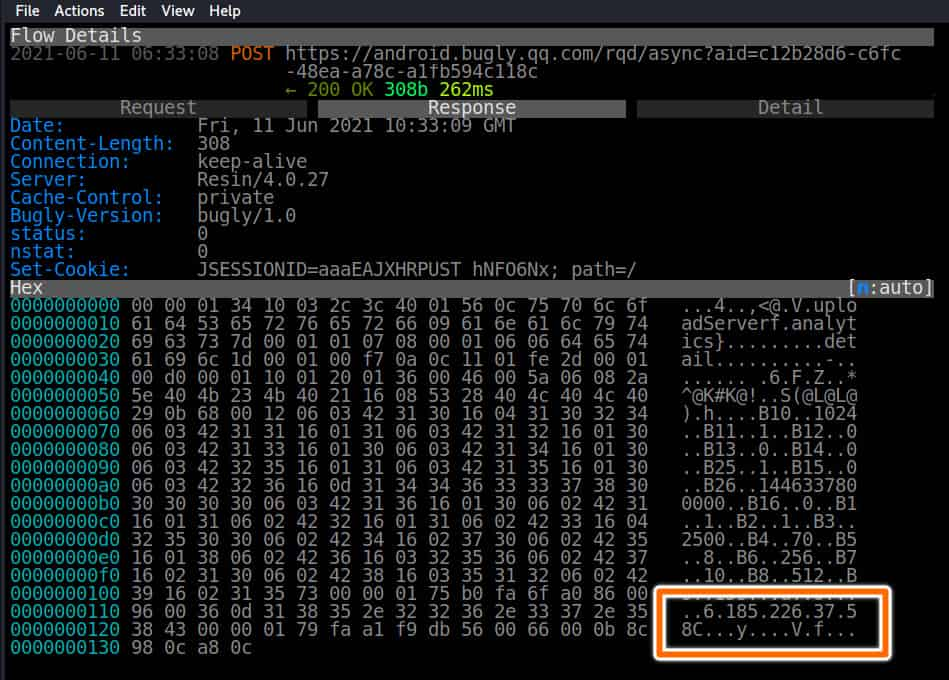
Mitmproxy screengrab showing SuperNet VPN server response from Bugly containing the real IP address used to connect to the service (highlighted).
Other third parties that receive data from the VPNs we tested included marketing data services Kochava and AppsFlyer, along with customer messaging service OneSignal, Google’s Android analytics platform Firebase, and Facebook.
Norton may be a well-known name in cybersecurity but our analysis revealed that its VPN app features the READ_PHONE_STATE permission to allow it to log the device’s unique IMEI code.
Methodology
The most popular VPNs during individual censorship events were identified for analysis using Sensor Tower data.
Traffic analysis of each VPN was conducted on a dedicated Android device in a sandboxed testing environment using mitmproxy. Leak testing was conducted using Wireshark. Analysis of the app code was conducted using various open source tools.
The authors of all our investigations abide by the journalists’ code of conduct.