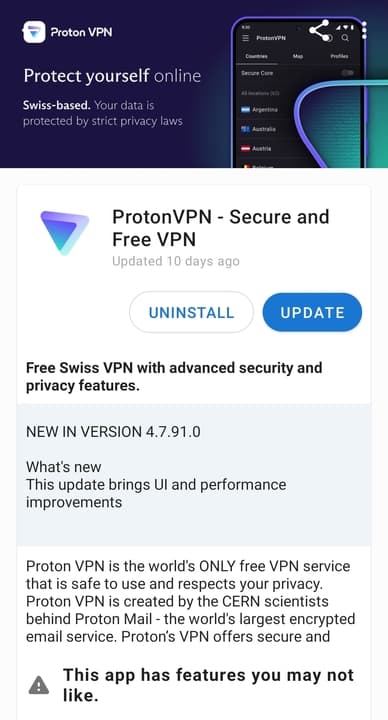
The table below compares the most common methods for bypassing internet restrictions. It explains how each method works, the types of internet censorship each method works to circumvent, and their limitations:
| Method |
How it Works |
Types of Censorship Circumvented |
Limitations |
| VPN Service |
Reroutes internet traffic through a remote server, encrypting and obfuscating the data along the way |
Content blocks, Geolocation restrictions, Deep packet inspection |
- Effectiveness and trustworthiness depends on the VPN provider
- May slow internet speeds to some extent
|
Proxy Server
|
Acts as an intermediary for requests from clients, allowing users to bypass internet filters |
Content blocks, Geolocation restrictions |
- Typically not encrypted
- Some proxies log user data
|
| Tor Browser |
Routes internet traffic through a global network of encrypted nodes to conceal users’ locations and activity |
Deep censorship, Content blocks, Deep packet inspection |
- Slower browsing speeds
- Some websites block Tor exit nodes
- Potential malicious exit nodes
|
| Custom DNS Server |
Bypasses ISP’s default DNS to circumvent domain-based blocking |
Domain-based blocks |
- The DNS request might not be encrypted
- ISPs can still see IP addresses visited
|
| Encrypted DNS (DoH/DoT) |
Encrypts DNS queries, preventing ISPs from seeing or manipulating domain requests |
Domain-based blocks, DNS tampering |
- Only encrypts the DNS query, not the entire connection
- Some ISPs might block encrypted DNS traffic
|
| SSH Tunneling |
Creates an encrypted tunnel between the user’s device and a remote server using SSH, allowing safe data transfer |
Content blocks, Surveillance |
- Requires access or ownership of a remote server
- Can be detected and blocked if SSH traffic is monitored
|
| Mirror Sites & IP Addresses |
Alternate websites or IP addresses replicating the content of the original site |
Domain and IP address blocks |
- Usually temporary (mirror sites can be blocked too)
- Trustworthiness and safety of mirror sites can vary
|
The most suitable method for you will depend on the censorship technique in use, and the resources you have available.
Before we explain each method in details, there are a few additional aspects to consider in order to make an informed decision:
- Security Implications: Consider the level of risk and the sensitivity of your communications. If you need the strongest possible security, use an encrypted tool like a VPN or the Tor Browser. Avoid weaker circumvention methods like web proxies, mirror sites, or custom DNS.
- Legal Implications: In some countries, the use of certain circumvention methods might be illegal. Consider the legal consequences in your jurisdiction before using any method.
- Ease of Setup: While some methods are relatively straightforward to set up (like installing a VPN application), others (like SSH tunneling) might require more technical expertise.
- Cost: Some methods might come at a cost. For instance, reliable VPN services usually charge monthly fees, whereas Tor is free.
- Anonymity: While some methods offer more privacy (e.g. Tor), others might log user activity (some VPNs and proxies). Read the privacy policy of the tool you’re using.
- Platform Support: Not all methods are available on all platforms. While VPN apps are prevalent across most devices, setting up Tor or SSH tunneling on mobile devices can be more challenging.
Here’s a more detailed look at each method:
Use a VPN (Virtual Private Network)
| Pros |
Cons |
| Bypasses against a range of common censorship techniques, including geo-restrictions |
May be difficult to download VPN software from within a censored country |
| Encrypts all web traffic leaving your device |
The most effective VPNs cost money |
| Hides your public IP address |
May slow down your internet connection somewhat |
| Easy to download and use on most devices |
Free VPNs may have weaker security, fewer server options, or may log your activity |
| Can protect multiple devices simultaneously with one account |
Some websites block or restrict access from known VPN IP ranges |
| Often provides additional security features, such as leak protection or a kill switch |
|
A VPN reroutes your data through a remote server via a secure, encrypted tunnel. The encrypted tunnel stops your ISP from seeing your online activities, while the remote server temporarily replaces your IP address with another IP address from a different region.
A VPN is the most effective way to bypass most forms of internet restriction. VPN encryption prevents censors from blocking your connection based on the website you’re visiting.
By connecting to a VPN server in a different country, VPNs also let you access content that’s typically blocked in your location. Many VPN services also have their own DNS servers, so you’re also protected from DNS tampering.
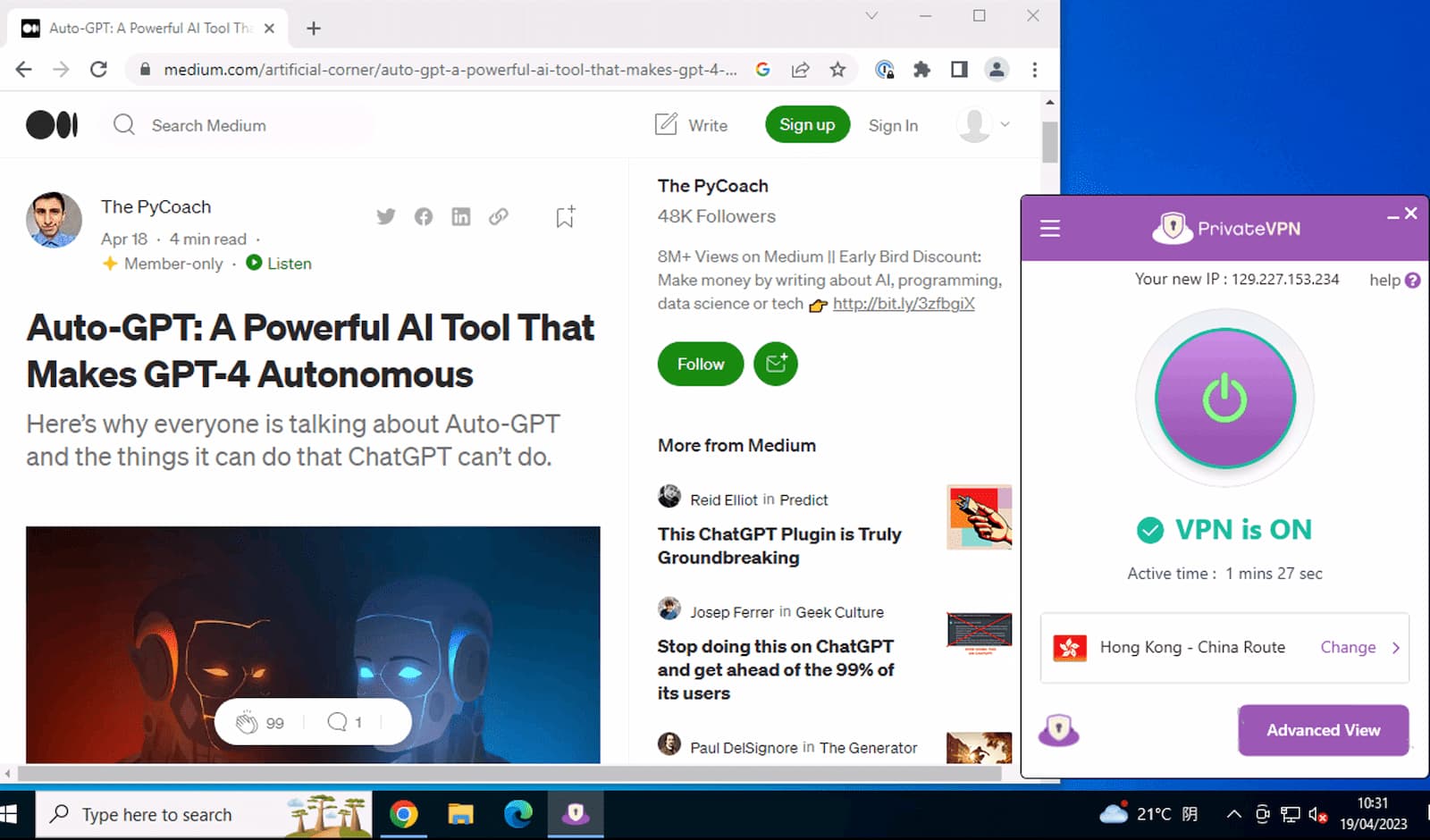
Tests with our Shanghai server in 2024 prove that PrivateVPN unblocks Medium in China.
When choosing a VPN to bypass censorship, look for:
- Obfuscation. VPN traffic has a distinctive signature which ISPs can identify and use to block your connection. To prevent this, some VPNs use obfuscation techniques that disguise the VPN traffic so it looks like normal web traffic.
- A trustworthy VPN provider. VPN providers have the technical ability to see who you are and what you’re doing online, so you need to pick a VPN that you trust. True no-logs VPNs store no data about their customers so nothing can be leaked or revealed, even under a court order.
- Independence. In high-censorship regimes such as China and Russia, state-approved VPNs will be compromised and insecure. Only unauthorized VPN services that are headquartered overseas are likely to protect you.
- A jurisdiction without surveillance. Some VPN services are based in countries with legal data retention or surveillance requirements. Look for a VPN headquartered in a privacy haven such as The British Virgin Islands.
- A reliable kill switch. This cuts off your internet connection if the VPN tunnel closes, which stops your true IP address (your real online identity) leaking. This is vital in countries where there are strict penalties for accessing censored content.
We’ve tested and reviewed 61 VPNs and found that Astrill is the most reliable VPN for avoiding censorship.
In the last three months, Astrill has worked to unblock censored websites in China 100% of the time. Astrill does not have a kill switch on its mobile apps though, so we recommend ExpressVPN instead if you’re primarily using an Android or iOS device.
Bypassing sophisticated internet censorship requires significant resources, so the most effective VPNs will typically require a monthly fee. However, there are a few trustworthy free VPNs, too.
EXPERT ADVICE: VPN websites are often blocked in countries with strict internet censorship. If you can’t access a VPN’s download page, search for a mirror website or file-sharing hosts through a private search engine such as DuckDuckGo. Otherwise, try to set up your VPN while abroad. Remember: VPNs are illegal in some countries, so exercise caution.
Use a Proxy Server
| Pros |
Cons |
| Often free to use |
Many proxy servers do not encrypt your data by default |
| Masks your IP address |
Advanced web filters can detect and block proxy servers |
| Can bypass geo-restrictions and access blocked content |
May require manual configuration |
| Some proxy servers offer encrypted connections for added security |
Free proxies can be unreliable or slow |
|
Many proxies lack transparent logging policies |
Proxy servers are similar to VPNs in some respects: they route your internet traffic through a remote server, spoofing your physical location and masking your IP address from other websites and services you connect to on the internet.
Unlike VPNs, proxy servers are often free to use — but they do not encrypt your data by default.
A proxy is useful for circumventing censorship in two situations:
- If the website you’re trying to access is blocked by your ISP, but you can use a web proxy service that isn’t. In that case, the web proxy can access the content for you and forward it on to you.
- If the web server you want to access is blocking your country, a web proxy can make you appear to be in a different country that is allowed access. For example, if a newspaper blocks visitors from your country, a web proxy might unblock it for you.
There are several different types of proxy server. Some types only reroute the data from a particular application (such as your browser), while others work for your whole device.
HTTPS and SOCKS5 proxies are the most secure options for bypassing censorship. HTTPS proxies use HTTPS encryption by default. SOCKS5 has no encryption built-in, but it can support encryption if configured correctly.
Other types — like common web proxies — are much less secure, and are typically only used to unblock banned websites in schools and workplaces.
SOCKS5 proxies can use the TCP or UDP connection protocols, which is similar to what most VPN protocols use. Much like VPN obfuscation, this improves your chances of bypassing local censorship without being blocked by your ISP.
In fact, VPNs that work in China and other highly-censored countries often use a protocol called ShadowSOCKS, which mimics the kind of TCP connection used by SOCKS5 proxies.
A small number of VPNs now provide SOCKS5 proxy servers as part of their service. This allows you to choose between a VPN server or a SOCKS5 proxy server. Be wary, though — the SOCKS5 option will not always encrypt your data.
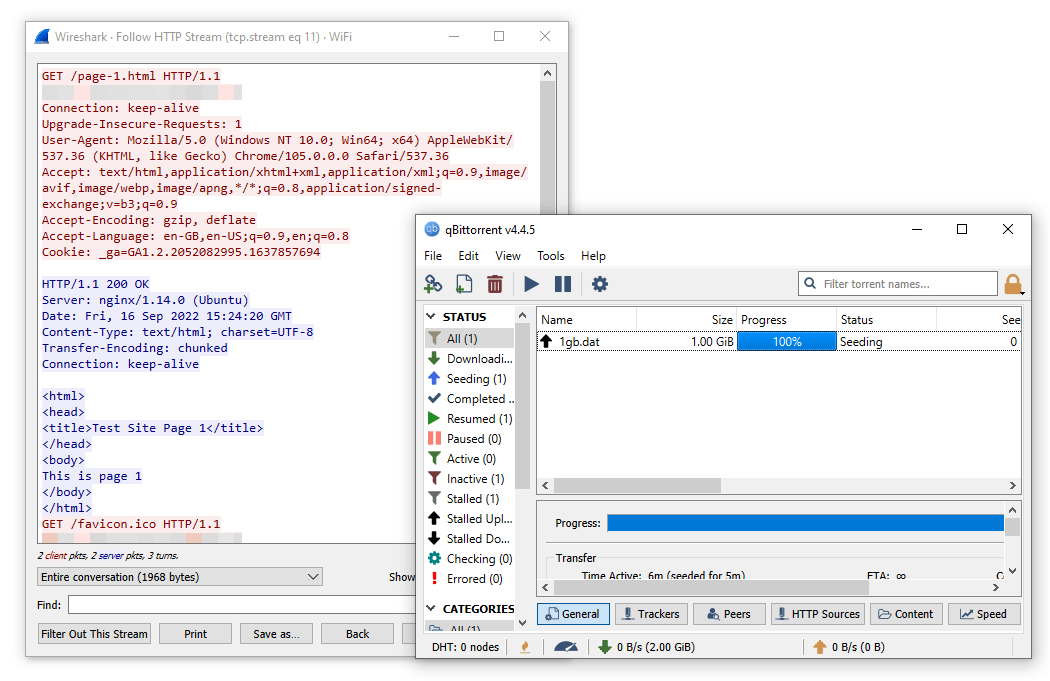
In our tests, NordVPN’s SOCKS5 proxy did not encrypt our torrenting traffic.
Unless you use a VPN with SOCKS5 support, the most effective proxies are typically quite difficult to configure.
Even when configured currently, a proxy doesn’t offer you the same security or privacy as a VPN. We recommend only using a proxy if your communications do not require additional privacy and security, or if the website blocks you’re bypassing are relatively rudimentary.
EXPERT ADVICE: Similar to a web proxy,Google Translate can fetch a website for you and show it in the browser. You don’t even have to change the language. Similarly, SodaPDF can create PDFs from web pages and may be able to fetch content you can’t access directly.
Use the Tor Browser
| Pros |
Cons |
| Open-source, free, and community-driven |
Tor’s network can be extremely slow |
| Reroutes traffic through multiple encrypted nodes |
Guard node sees your IP address |
| Can access the deep web and bypass internet censorship |
Exit node sees your unencrypted traffic |
| Does not keep user activity logs |
Exit nodes can be compromised or malicious |
|
No control over your final IP address location |
|
Some websites block or restrict access from Tor nodes |
|
Complex to set up and use for non-technical users |
|
May draw attention from your ISP |
The Tor Browser encrypts your traffic and routes it through three randomly-assigned servers, called nodes. It’s free to use and highly anonymous: no server can see both your IP address (who you are) and your web traffic (what you’re doing).
Tor is slow, so it’s not ideal for transferring large files, but it changes your IP address and bypasses URL filters effectively.
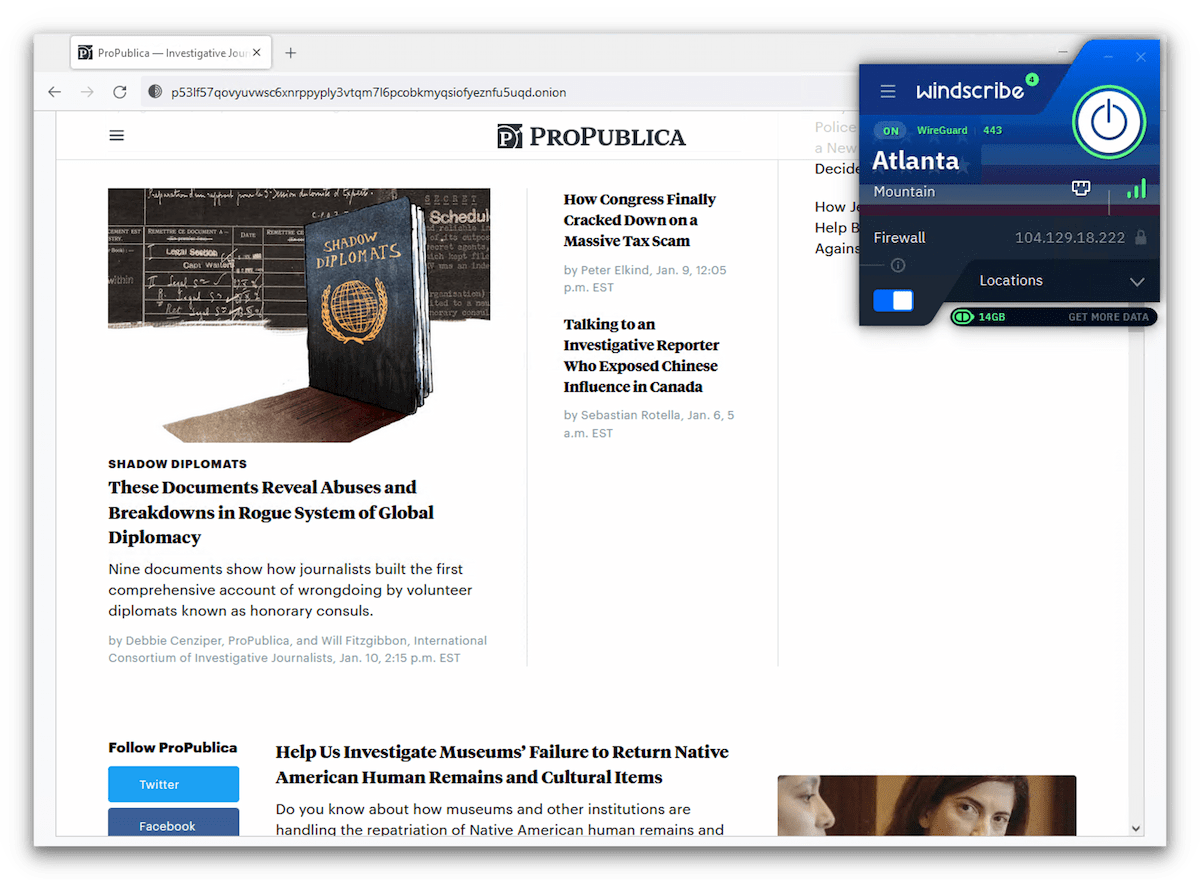
Connected to Windscribe free and the Tor browser, we accessed ProPublica’s onion site.
Though it can be a good choice for activists or whistleblowers sharing sensitive information, Tor isn’t always safe. Malicious exit nodes could insert malware in your traffic, and there is proof that some users can be de-anonymized.
Your ISP can see you’re using Tor and might flag you for surveillance. Put simply, Tor needs to be set up carefully if you want to be completely anonymous online.
The Tor browser also gives you access to the dark web, which is often used for illegal content but can be legitimately used to share information that is unreasonably restricted or subject to censorship.
Tor Snowflake can also be a useful tool in bypassing government censorship. You can install the extension on Firefox, Chrome and Edge. It works much like a proxy app and obfuscates your traffic allowing you to access blocked websites.
If Tor traffic is blocked, you can hide it by connecting to a VPN before running Tor. However, your VPN provider will see your true IP address and exit nodes can still see your traffic.
Use a Custom DNS Server
| Pros |
Cons |
| Can bypass DNS-based censorship by resolving domain names independently |
Unlikely to work against IP blocking, deep packet inspection, or other techniques employed by high-censorship countries |
| Allows for customization and control over domain name resolution |
Does not encrypt your traffic |
| Free and easy to set up |
A misconfigured DNS server can lead to security vulnerabilities |
|
Does not mask your IP address |
When you visit a website, DNS servers convert its web address (e.g. www.example.com) into the IP address of the server that hosts the website. The IP address is used to route your communications through the internet.
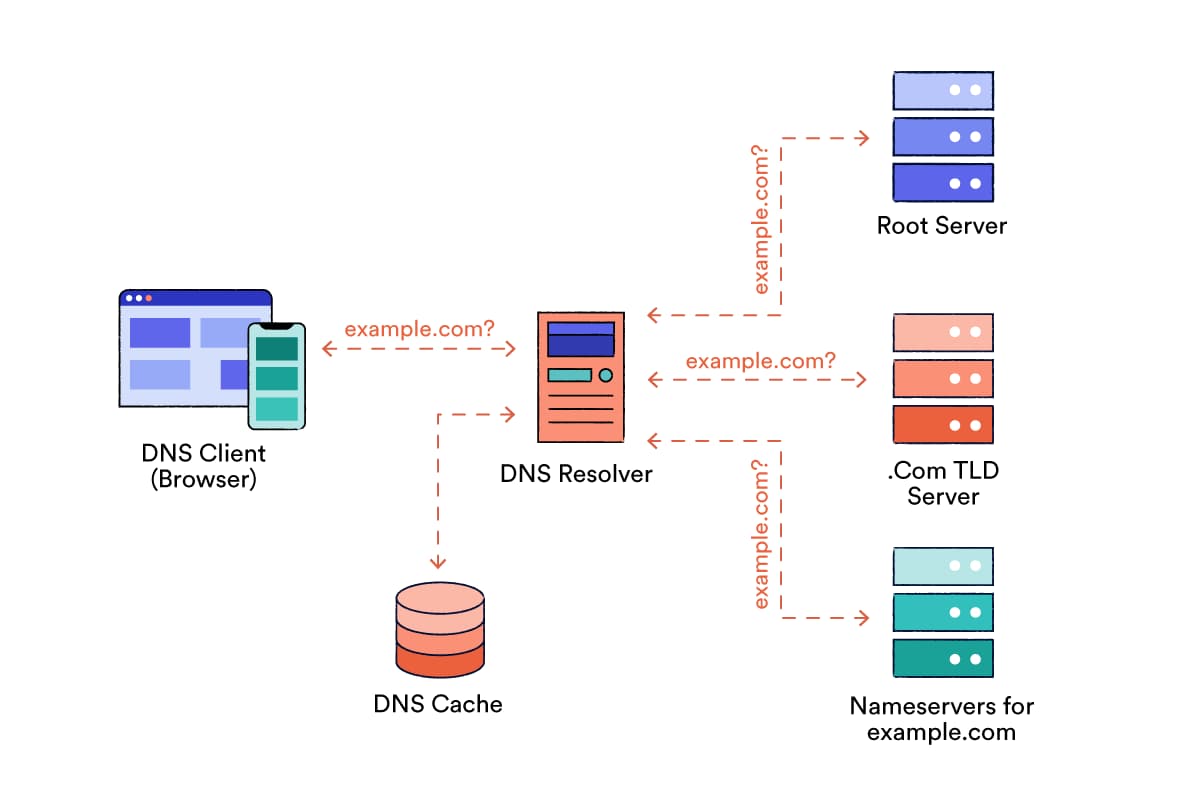
Your DNS resolver finds out the IP address for a website, so your device can connect to its server.
DNS servers can be made to enforce censorship by blocking access to sites or diverting you to compromised alternatives. If you use your ISP’s DNS server, your ISP can monitor which websites you visit.
To avoid DNS filtering, DNS spoofing, and ISP surveillance, you can try using a custom DNS server. We’ve compiled a list of safe, free DNS servers alongside our DNS checker tool, and you can find setup instructions in our guide comparing the differences between DNS and VPNs.
It’s worth noting that this method is unlikely to work against sophisticated censorship techniques such as IP blocking or deep packet inspection. These techniques do not use DNS to impose their restrictions.
Note: Many VPN services — including VyprVPN and Hide.me — use their own first-party DNS servers. By connecting to a VPN server operated by these services, you can combine the benefits of both a VPN and a custom DNS server.
Use Encrypted DNS
| Pros |
Cons |
| Prevents eavesdropping on DNS requests |
Does not encrypt your web traffic — just the DNS queries |
| Can bypass DNS-based censorship and surveillance |
Will not bypass censorship if IP blocking or deep packet inspection is used |
| Improved privacy and security compared to traditional DNS |
May be blocked or restricted in some regions or networks |
DNS traffic isn’t usually encrypted, so it’s vulnerable to eavesdropping and man-in-the-middle attacks. That means state agencies could track the websites you’re visiting and redirect your traffic to censored sites.
To avoid this, you can use DNS over HTTPS, which uses HTTPS encryption to protect your communications with the DNS server.
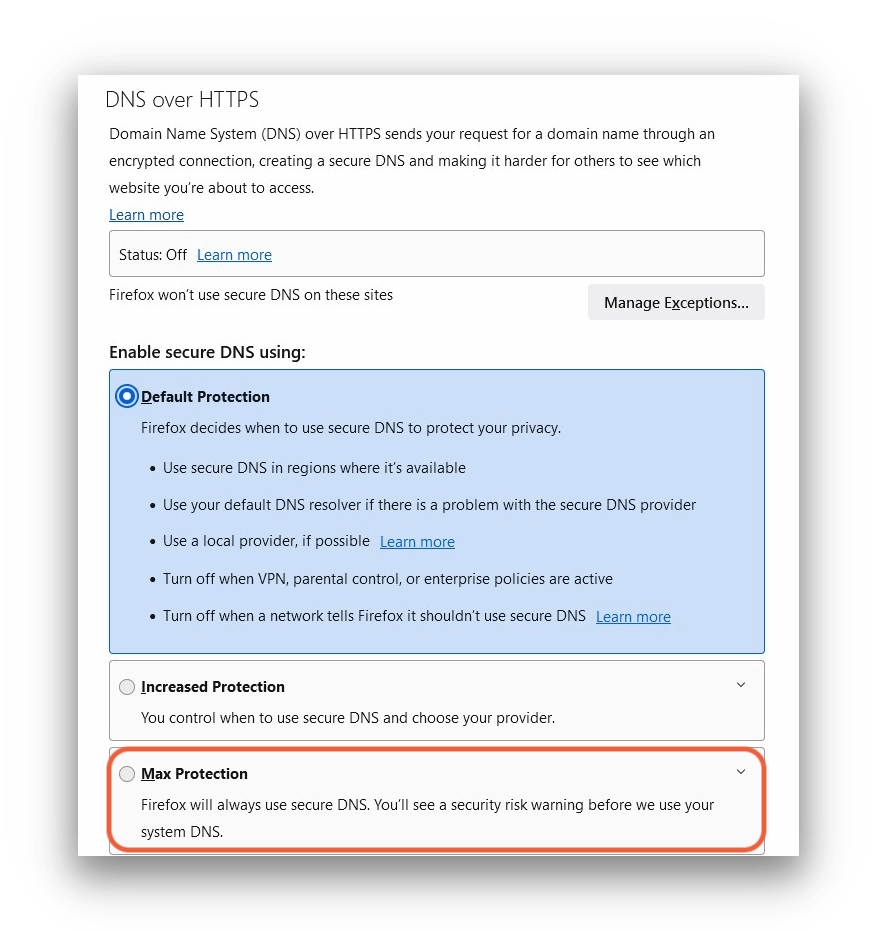
DNS over HTTPS increases user privacy and prevents eavesdropping.
Your ISP would still see your DNS requests if it operates the DNS server, so encrypted DNS is best used together with custom DNS in strictly censored countries.
Encrypted DNS is now supported in Windows 11, iOS, Android, and macOS. The Firefox browser uses DNS over HTTPS in the US, and the Tor Browser used DNS over HTTPs by default.
DNS over TLS is a similar solution based on a different encryption technology.
However, your internet traffic can still be disrupted after the DNS lookup stage. For this reason, encrypted DNS alone is unlikely to bypass most forms of government censorship alone.
Use SSH Tunneling
| Pros |
Cons |
| Encrypts traffic between your device and the SSH server |
Requires an understanding of networking |
| Can bypass some network restrictions and censorship |
Costs money to rent an SSH server |
| Masks your IP address |
SSH tunneling can be detected and blocked by some firewalls and deep packet inspection |
|
Not as user-friendly as VPN software |
|
Only tunnels requests from a browser that has been configured with SOCKS proxy access |
Secure Shell (SSH) Tunneling provides a secure method to bypass network restrictions and content filters by routing your traffic through an encrypted tunnel to an SSH server.
The server can be in another country, which may help in unblocking geo-restricted resources. Much like a VPN, the encrypted tunnel stops your ISP and others from snooping on your web traffic.
It’s also possible to use SSH tunneling to hide your OpenVPN traffic, though this is quite complicated and not recommended for technically inexperienced users.
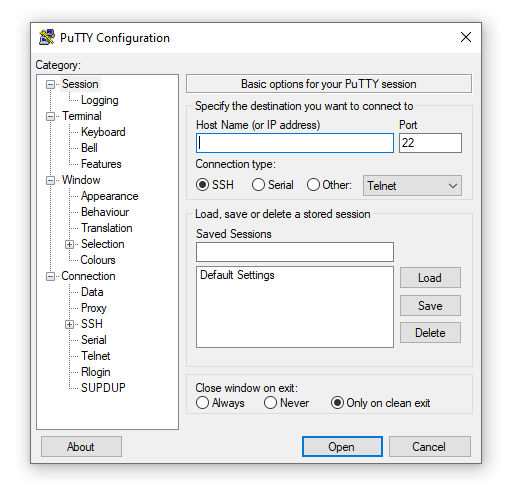
Use PuTTY to create an SSH tunnel on Windows.
For most people, a VPN is a more user-friendly option than SSH. That said, SSH is a good alternative if you already have a remote server you can use, or if you can’t access a VPN service. You can find SSH servers available to rent online.
To create an SSH tunnel, use PuTTY on Windows or the SSH command on Mac and Linux.
Use Mirror Sites and IP Addresses
| Pros |
Cons |
| Provides access to content that might be blocked or restricted |
Unlikely to bypass sophisticated censorship |
| No technical setup required |
May host outdated or incorrect information |
| Can bypass basic censorship mechanisms by providing the same content on different URLs |
Malicious actors can host mirror sites to distribute malware or gather user data |
|
Often blocked quickly if identified by censors |
|
No encryption, so your browsing activity could be monitored |
|
Your IP address and browsing activity are still visible to network administrators |
Mirror sites are copies of blocked content that are hosted on different URLs. They can provide a quick and easy way to access blocked or restricted content without any technical setup.
However, they come with significant drawbacks. Firstly, they’re unlikely to work against sophisticated state censorship. If they do, it’s likely they’ll be blocked or removed quickly once identified by censors.
Mirror sites also pose some security risks, depending on the sensitivity of the content they’re hosting. Most importantly, they lack any kind of encryption, and they do nothing to protect your digital privacy.
If there’s a particular site you want to access that has been blocked, there are several ways you can try to access its content:
- Mirror sites store copies of web pages and other information on different, unblocked domains. For example, Samizdat Online syndicates content blocked by the Russian government. It’s hosted on domains that are randomly named and automatically registered, making it hard for censors to keep up.
- Archives and caches store old copies of web pages. The Wayback Machine has date-stamped copies of most web pages, and you can try Google’s cache by searching for “cache:URL”, where “URL” is the web page you want to see.
- RSS aggregators such as Feedly might have access to the web page and be able to show it to you using the RSS syndication standard.